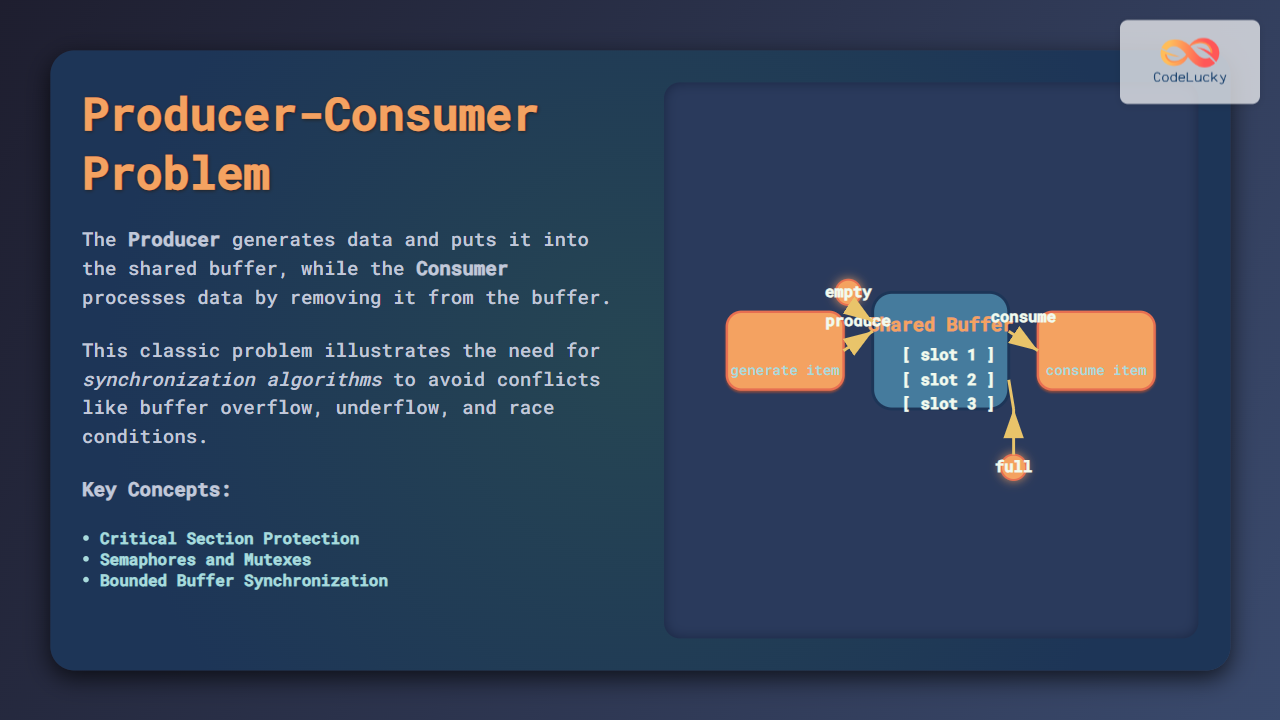
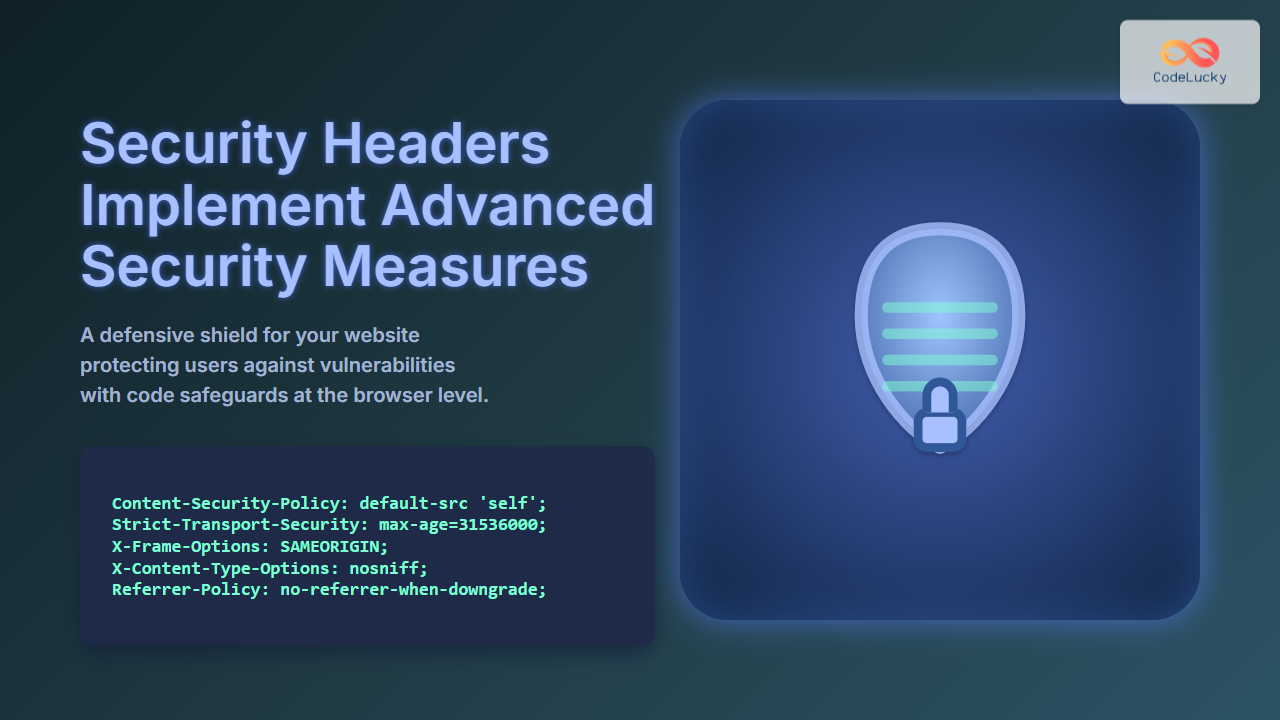
Buffer overflow vulnerabilities represent one of the most critical and persistent security threats in modern computing systems. These memory-related exploits have been responsible for countless security breaches, from simple application crashes to sophisticated remote code execution attacks that compromise entire systems.
Understanding Buffer Overflow Fundamentals
A buffer overflow occurs when a program writes more data to a buffer than it can hold, causing the excess data to overwrite adjacent memory locations. This seemingly simple concept underlies some of the most devastating security vulnerabilities in computing history.
Memory Layout and Stack Structure
To understand buffer overflows, we must first examine how programs organize memory. The typical memory layout includes several key sections:
- Stack: Contains local variables, function parameters, and return addresses
- Heap: Dynamically allocated memory for runtime objects
- Data Segment: Global and static variables
- Code Segment: Executable program instructions
Types of Buffer Overflow Attacks
Stack-Based Buffer Overflows
Stack-based overflows target the function call stack, attempting to overwrite return addresses or function pointers. Here’s a vulnerable C code example:
#include <stdio.h>
#include <string.h>
void vulnerable_function(char *input) {
char buffer[64];
strcpy(buffer, input); // Vulnerable: No bounds checking
printf("Buffer content: %s\n", buffer);
}
int main(int argc, char *argv[]) {
if (argc > 1) {
vulnerable_function(argv[1]);
}
return 0;
}
Output when exploited:
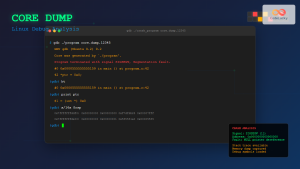
$ ./vulnerable_program $(python -c "print('A' * 100)")
Buffer content: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...
Segmentation fault (core dumped)
Heap-Based Buffer Overflows
Heap overflows target dynamically allocated memory, potentially corrupting heap metadata or adjacent objects:
#include <stdlib.h>
#include <string.h>
void heap_overflow_example() {
char *buffer1 = malloc(64);
char *buffer2 = malloc(64);
// Vulnerable: Writing beyond buffer1's boundary
strcpy(buffer1, "Very long string that exceeds 64 characters and corrupts heap");
free(buffer1);
free(buffer2);
}
Common Exploitation Techniques
Return Address Overwriting
The classic buffer overflow technique involves overwriting the return address on the stack to redirect program execution:
# Exploit payload structure
payload = "A" * 64 # Fill the buffer
payload += "B" * 4 # Overwrite saved base pointer
payload += "\x78\x56\x34\x12" # New return address (little-endian)
Shellcode Injection
Attackers often inject malicious code (shellcode) that spawns a shell or executes system commands:
; Example x86 shellcode to spawn /bin/sh
xor eax, eax ; Clear EAX register
push eax ; Push null terminator
push 0x68732f2f ; Push "//sh"
push 0x6e69622f ; Push "/bin"
mov ebx, esp ; Point EBX to "/bin//sh"
mov ecx, eax ; Clear ECX
mov edx, eax ; Clear EDX
mov al, 0x0b ; System call number for execve
int 0x80 ; Trigger system call
Advanced Exploitation Methods
Return-Oriented Programming (ROP)
ROP attacks chain together existing code fragments (gadgets) to bypass modern security measures:
Format String Vulnerabilities
These vulnerabilities arise when user input is passed directly to format string functions:
// Vulnerable code
printf(user_input); // Should be printf("%s", user_input);
// Exploitation example
// Input: "%x %x %x %x" reveals stack contents
// Input: "%n" can write to memory addresses
Modern Defense Mechanisms
Address Space Layout Randomization (ASLR)
ASLR randomizes memory layout to make exploitation more difficult:
# Check ASLR status on Linux
cat /proc/sys/kernel/randomize_va_space
# 0 = Disabled, 1 = Conservative, 2 = Full randomization
Stack Canaries
Stack canaries detect buffer overflows by placing known values before critical data:
// Compiler-generated canary protection
void protected_function() {
unsigned long canary = __stack_chk_guard;
char buffer[64];
// Function body
if (canary != __stack_chk_guard) {
__stack_chk_fail(); // Abort on corruption
}
}
Data Execution Prevention (DEP/NX)
DEP marks memory pages as either executable or writable, but not both:
Secure Coding Practices
Safe String Functions
Replace dangerous functions with safer alternatives:
// Dangerous functions
strcpy(dest, src); // Use strncpy() or strcpy_s()
strcat(dest, src); // Use strncat() or strcat_s()
sprintf(buffer, fmt); // Use snprintf()
gets(buffer); // Use fgets()
// Safer alternatives
strncpy(dest, src, sizeof(dest) - 1);
dest[sizeof(dest) - 1] = '\0';
snprintf(buffer, sizeof(buffer), "%s", input);
Input Validation and Bounds Checking
Always validate input length and implement proper bounds checking:
int secure_copy(char *dest, const char *src, size_t dest_size) {
if (!dest || !src || dest_size == 0) {
return -1; // Invalid parameters
}
size_t src_len = strlen(src);
if (src_len >= dest_size) {
return -1; // Source too large
}
memcpy(dest, src, src_len);
dest[src_len] = '\0';
return 0;
}
Detection and Analysis Tools
Static Analysis Tools
- Clang Static Analyzer: Detects potential buffer overflows during compilation
- Coverity: Commercial static analysis with extensive vulnerability detection
- PC-lint: Identifies unsafe coding patterns and potential overflows
Dynamic Analysis Tools
# Valgrind for memory error detection
valgrind --tool=memcheck ./your_program
# AddressSanitizer compilation flag
gcc -fsanitize=address -g -o program program.c
# Running with AddressSanitizer
./program
Real-World Impact and Case Studies
Historical Vulnerabilities
Several major security incidents have resulted from buffer overflow vulnerabilities:
- Morris Worm (1988): Exploited buffer overflow in fingerd service
- Code Red (2001): Targeted IIS buffer overflow vulnerability
- Slammer Worm (2003): Exploited SQL Server buffer overflow
Modern Vulnerability Examples
Even with modern defenses, buffer overflows continue to affect systems:
# Example: Checking for recent CVEs
curl -s "https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=buffer+overflow" | grep -i "buffer overflow"
Penetration Testing and Exploitation
Fuzzing Techniques
Fuzzing helps discover buffer overflow vulnerabilities through automated testing:
import random
import subprocess
import string
def generate_fuzzing_input(length):
return ''.join(random.choices(string.ascii_letters, k=length))
# Basic fuzzing loop
for i in range(100, 2000, 100):
payload = generate_fuzzing_input(i)
try:
result = subprocess.run(['./target_program', payload],
timeout=5, capture_output=True)
if result.returncode != 0:
print(f"Potential crash with input length: {i}")
except subprocess.TimeoutExpired:
print(f"Timeout with input length: {i}")
Prevention Strategies and Best Practices
Development Guidelines
- Use memory-safe languages: Consider Rust, Go, or Java for new projects
- Enable compiler protections: Use -fstack-protector, -D_FORTIFY_SOURCE=2
- Implement proper error handling: Never ignore return values from security functions
- Regular security audits: Conduct code reviews focusing on buffer boundaries
System-Level Protections
# Enable system-wide ASLR
echo 2 | sudo tee /proc/sys/kernel/randomize_va_space
# Compile with security flags
gcc -fstack-protector-strong -D_FORTIFY_SOURCE=2 -fPIE -pie program.c
# Enable core dump analysis
ulimit -c unlimited
gdb ./program core
Future Trends and Emerging Threats
As systems evolve, so do the techniques for exploiting buffer overflows:
- Hardware-assisted security: Intel CET, ARM Pointer Authentication
- Machine learning detection: AI-powered vulnerability discovery
- Container security: Protecting containerized applications from memory corruption
- IoT vulnerabilities: Buffer overflows in resource-constrained devices
Conclusion
Buffer overflow vulnerabilities remain a significant threat to system security despite decades of research and defensive improvements. Understanding these vulnerabilities, their exploitation methods, and prevention techniques is crucial for developers, security professionals, and system administrators.
The key to defending against buffer overflows lies in implementing multiple layers of protection: secure coding practices, compiler-based defenses, runtime protections, and regular security testing. As attackers develop new bypass techniques, the security community must continue evolving defensive strategies to stay ahead of emerging threats.
By combining proper education, robust development practices, and comprehensive security measures, organizations can significantly reduce their exposure to buffer overflow attacks and build more resilient systems capable of withstanding sophisticated security threats.