Winlogbeat is a lightweight shipper designed to forward Windows Event Logs to Elasticsearch or Logstash. While it primarily runs on Windows systems, managing and configuring Winlogbeat from Linux environments is a common requirement in mixed infrastructure setups. This comprehensive guide will walk you through everything you need to know about working with Winlogbeat from Linux systems.
What is Winlogbeat?
Winlogbeat is part of the Elastic Stack (ELK Stack) and serves as a specialized data shipper for Windows Event Logs. It reads from one or more event logs using Windows APIs, filters the events based on user-configured criteria, and ships the event data to the configured outputs.
Key Features of Winlogbeat
- Real-time Event Shipping: Continuously monitors and ships Windows events
- Flexible Filtering: Advanced filtering capabilities to send only relevant events
- Multiple Output Support: Ships to Elasticsearch, Logstash, Kafka, and other outputs
- Low Resource Usage: Lightweight agent with minimal system impact
- Built-in Dashboards: Pre-configured Kibana dashboards for visualization
Prerequisites for Linux-based Management
Before diving into Winlogbeat configuration from Linux, ensure you have:
- A Linux system with network access to Windows machines
- Elasticsearch cluster (can be on Linux)
- Windows systems where Winlogbeat will be installed
- Administrative access to both Linux and Windows systems
- Basic understanding of YAML configuration files
Installing Winlogbeat on Windows (Managed from Linux)
While Winlogbeat runs on Windows, you can manage the installation and configuration remotely from Linux using various methods.
Method 1: Using PowerShell Remoting
From your Linux system, you can use PowerShell Core to remotely install Winlogbeat:
# Install PowerShell Core on Linux (Ubuntu/Debian)
sudo apt-get update
sudo apt-get install -y wget apt-transport-https software-properties-common
wget -q https://packages.microsoft.com/config/ubuntu/20.04/packages-microsoft-prod.deb
sudo dpkg -i packages-microsoft-prod.deb
sudo apt-get update
sudo apt-get install -y powershell
# Connect to Windows system and install Winlogbeat
pwsh -c "
\$session = New-PSSession -ComputerName 'your-windows-server' -Credential (Get-Credential)
Invoke-Command -Session \$session -ScriptBlock {
# Download Winlogbeat
Invoke-WebRequest -Uri 'https://artifacts.elastic.co/downloads/beats/winlogbeat/winlogbeat-8.8.0-windows-x86_64.zip' -OutFile 'winlogbeat.zip'
# Extract and install
Expand-Archive winlogbeat.zip -DestinationPath 'C:\Program Files\'
Rename-Item 'C:\Program Files\winlogbeat-8.8.0-windows-x86_64' 'C:\Program Files\Winlogbeat'
# Install as service
cd 'C:\Program Files\Winlogbeat'
.\install-service-winlogbeat.ps1
}
"Method 2: Using Ansible
Create an Ansible playbook to automate Winlogbeat deployment:
# winlogbeat-deploy.yml
---
- hosts: windows_servers
vars:
winlogbeat_version: "8.8.0"
elasticsearch_hosts: ["http://elastic-node1:9200", "http://elastic-node2:9200"]
tasks:
- name: Download Winlogbeat
win_get_url:
url: "https://artifacts.elastic.co/downloads/beats/winlogbeat/winlogbeat-{{ winlogbeat_version }}-windows-x86_64.zip"
dest: "C:\\temp\\winlogbeat.zip"
- name: Extract Winlogbeat
win_unzip:
src: "C:\\temp\\winlogbeat.zip"
dest: "C:\\Program Files\\"
- name: Install Winlogbeat service
win_shell: |
cd "C:\Program Files\winlogbeat-{{ winlogbeat_version }}-windows-x86_64"
.\install-service-winlogbeat.ps1
become: yesRun the playbook from Linux:
ansible-playbook -i inventory winlogbeat-deploy.ymlConfiguring Winlogbeat from Linux
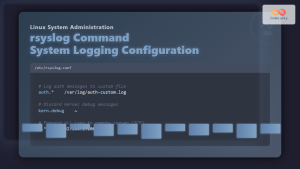
The main configuration file for Winlogbeat is winlogbeat.yml. You can create and manage this configuration from your Linux system and deploy it to Windows machines.
Basic Configuration Structure
# winlogbeat.yml
winlogbeat.event_logs:
- name: Application
ignore_older: 72h
level: info
- name: System
ignore_older: 72h
level: error
- name: Security
ignore_older: 72h
# Output configuration
output.elasticsearch:
hosts: ["http://elasticsearch-server:9200"]
username: "elastic"
password: "changeme"
index: "winlogbeat-%{+yyyy.MM.dd}"
# Logging configuration
logging.level: info
logging.to_files: true
logging.files:
path: C:\ProgramData\winlogbeat\Logs
name: winlogbeat
keepfiles: 7
permissions: 0644
# Processors
processors:
- add_host_metadata:
when.not.contains.tags: forwardedAdvanced Event Log Configuration
For more granular control over which events to ship:
winlogbeat.event_logs:
- name: Application
ignore_older: 72h
level: info
event_id: 1000, 1001, 1002
provider:
- Microsoft-Windows-Application-Experience
include_xml: true
- name: System
ignore_older: 72h
level: error
exclude_event_id: 5, 10
- name: Security
ignore_older: 168h # 1 week
level: info
event_id: 4624, 4625, 4648, 4720
processors:
- drop_event:
when:
equals:
winlog.event_id: 4634Deploying Configuration from Linux
Using SCP and SSH
# Copy configuration file to Windows machine
scp winlogbeat.yml administrator@windows-server:"C:/Program Files/Winlogbeat/"
# Restart Winlogbeat service remotely
ssh administrator@windows-server "sc stop winlogbeat && sc start winlogbeat"Using Rsync over SSH
# Sync entire configuration directory
rsync -avz -e ssh ./winlogbeat-configs/ administrator@windows-server:"/cygdrive/c/Program Files/Winlogbeat/"Managing Multiple Windows Servers
When managing Winlogbeat across multiple Windows servers from Linux, create a centralized management approach:
Configuration Management Script
#!/bin/bash
# manage-winlogbeat.sh
SERVERS=("server1.example.com" "server2.example.com" "server3.example.com")
CONFIG_FILE="winlogbeat.yml"
WINLOGBEAT_PATH="/cygdrive/c/Program Files/Winlogbeat"
deploy_config() {
local server=$1
echo "Deploying configuration to $server..."
# Copy configuration
scp $CONFIG_FILE administrator@$server:"$WINLOGBEAT_PATH/"
# Restart service
ssh administrator@$server "sc stop winlogbeat; sc start winlogbeat"
# Check service status
ssh administrator@$server "sc query winlogbeat"
}
# Deploy to all servers
for server in "${SERVERS[@]}"; do
deploy_config $server
echo "Completed deployment to $server"
echo "------------------------"
doneMonitoring Winlogbeat from Linux
Set up monitoring scripts to check Winlogbeat status across your Windows fleet:
#!/bin/bash
# monitor-winlogbeat.sh
check_winlogbeat_status() {
local server=$1
echo "Checking Winlogbeat status on $server..."
# Check service status
status=$(ssh administrator@$server "sc query winlogbeat | grep STATE")
echo "$server: $status"
# Check recent logs
ssh administrator@$server "powershell Get-EventLog -LogName Application -Source winlogbeat -Newest 5 | Select TimeGenerated, Message"
}
# Check all servers
SERVERS=("server1.example.com" "server2.example.com")
for server in "${SERVERS[@]}"; do
check_winlogbeat_status $server
echo "------------------------"
doneTroubleshooting Common Issues
Connection Issues
Test connectivity from Windows to Elasticsearch:
# From Linux, run PowerShell command on Windows machine
pwsh -c "
Invoke-Command -ComputerName 'windows-server' -ScriptBlock {
Test-NetConnection -ComputerName 'elasticsearch-server' -Port 9200
# Test HTTP connectivity
try {
\$response = Invoke-WebRequest -Uri 'http://elasticsearch-server:9200' -UseBasicParsing
Write-Output \"Elasticsearch is reachable: \$(\$response.StatusCode)\"
} catch {
Write-Output \"Connection failed: \$(\$_.Exception.Message)\"
}
}
"Log Analysis
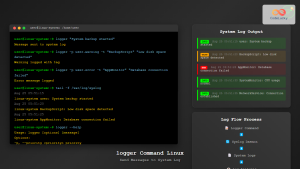
Analyze Winlogbeat logs remotely:
# View recent Winlogbeat logs
ssh administrator@windows-server "powershell Get-Content 'C:\ProgramData\winlogbeat\Logs\winlogbeat' | Select-Object -Last 50"
# Search for specific errors
ssh administrator@windows-server "powershell Select-String -Path 'C:\ProgramData\winlogbeat\Logs\winlogbeat' -Pattern 'ERROR'"Performance Optimization
Optimized Configuration for High-Volume Environments
# High-performance winlogbeat.yml
winlogbeat.event_logs:
- name: Security
batch_read_size: 100
include_xml: false
processors:
- drop_fields:
fields: ["agent", "ecs", "host.architecture"]
# Bulk configuration for better throughput
output.elasticsearch:
hosts: ["http://es-node1:9200", "http://es-node2:9200"]
worker: 2
bulk_max_size: 3200
flush_interval: 1s
compression_level: 1
# Memory and CPU optimization
queue.mem:
events: 4096
flush.min_events: 512
flush.timeout: 1sSecurity Best Practices
Secure Configuration Template
# Secure winlogbeat.yml
output.elasticsearch:
hosts: ["https://elasticsearch:9200"]
protocol: "https"
username: "winlogbeat_writer"
password: "${ELASTIC_PASSWORD}"
ssl:
certificate_authorities: ["ca.crt"]
certificate: "client.crt"
key: "client.key"
# Enable SSL/TLS
ssl:
enabled: true
certificate_authorities:
- /etc/ssl/certs/ca-certificates.crt
# Secure logging
logging.level: warning
logging.selectors: ["*"]
logging.files:
permissions: 0600Managing Credentials Securely
Store sensitive configuration in environment variables:
# Set environment variables on Windows from Linux
ssh administrator@windows-server "setx ELASTIC_PASSWORD 'your-secure-password' /M"
# Use in configuration
output.elasticsearch:
password: "${ELASTIC_PASSWORD}"Integration with CI/CD Pipelines
Integrate Winlogbeat deployment into your DevOps pipeline:
# Jenkins pipeline example
pipeline {
agent any
stages {
stage('Deploy Winlogbeat Config') {
steps {
script {
def servers = ['server1', 'server2', 'server3']
servers.each { server ->
sh """
scp winlogbeat.yml administrator@${server}:"/cygdrive/c/Program Files/Winlogbeat/"
ssh administrator@${server} "sc stop winlogbeat; sc start winlogbeat"
"""
}
}
}
}
stage('Verify Deployment') {
steps {
script {
sh './scripts/verify-winlogbeat-deployment.sh'
}
}
}
}
}Conclusion
Managing Winlogbeat from Linux systems provides a centralized approach to Windows event log collection in mixed environments. By leveraging remote management tools, automation scripts, and proper configuration management, you can efficiently deploy and maintain Winlogbeat across your Windows infrastructure from Linux systems.
Key takeaways include using remote PowerShell for management, implementing configuration automation with Ansible or custom scripts, and maintaining security best practices throughout your deployment. Regular monitoring and optimization ensure your log shipping pipeline remains reliable and performant.
This approach scales well from small deployments to enterprise environments, providing the flexibility and control needed for modern IT infrastructures where Linux and Windows systems coexist.