Introduction to Windows NT Kernel
The Windows NT Kernel forms the foundation of all modern Windows operating systems, from Windows NT 3.1 to the latest Windows 11. Unlike its predecessors, the NT kernel was designed from the ground up to be a robust, secure, and portable operating system kernel that could support multiple hardware architectures and provide enterprise-grade reliability.
The NT (New Technology) kernel represents a significant departure from the MS-DOS-based Windows systems, introducing advanced features like preemptive multitasking, memory protection, and symmetric multiprocessing (SMP) support.
NT Kernel Architecture Overview
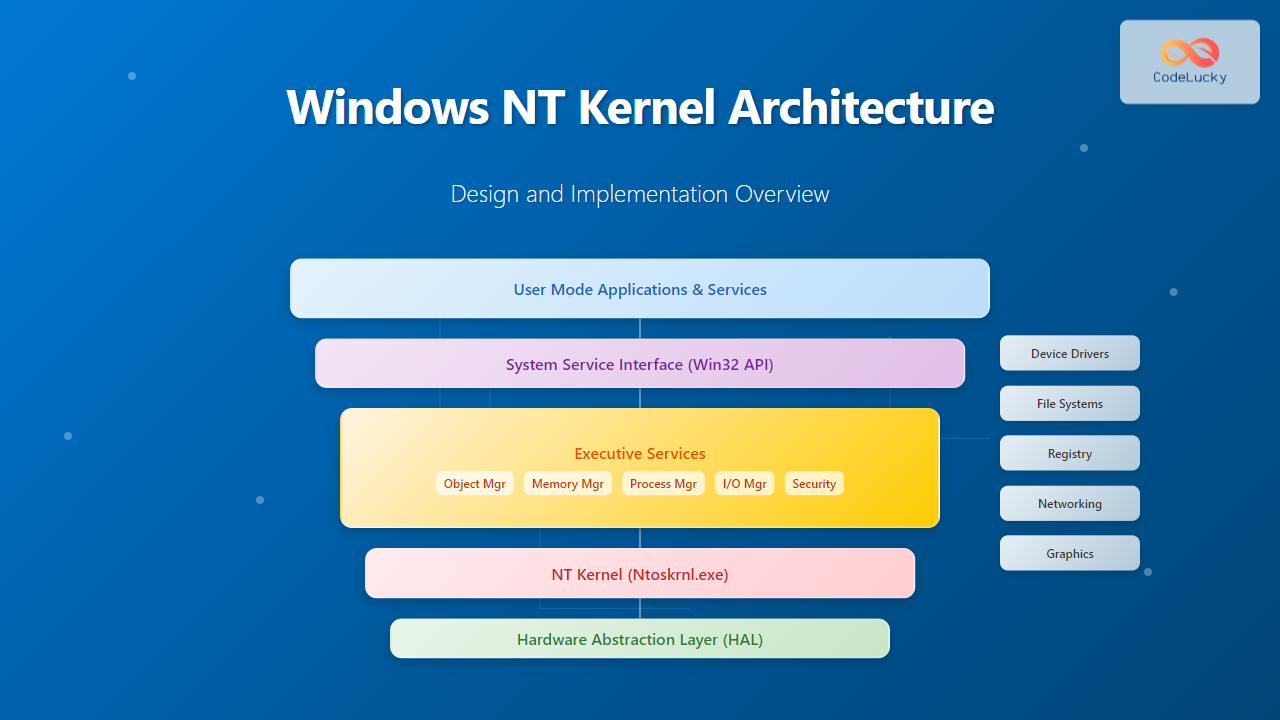
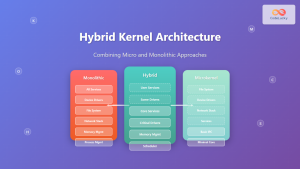
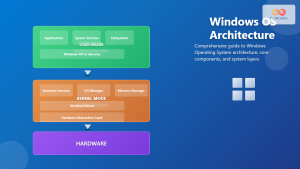
The Windows NT kernel follows a hybrid microkernel architecture, combining elements of both monolithic and microkernel designs. This approach provides the performance benefits of a monolithic kernel while maintaining the modularity and reliability of a microkernel.
Key Architectural Components
1. Hardware Abstraction Layer (HAL)
The HAL provides a consistent interface between the kernel and the underlying hardware. It abstracts hardware-specific details, enabling the same kernel to run on different hardware platforms.
Key Functions:
- Interrupt handling and routing
- DMA (Direct Memory Access) operations
- Timer and clock management
- System bus interface
- Power management interface
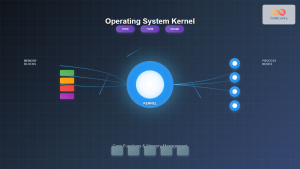
2. NT Kernel (Ntoskrnl.exe)
The core kernel provides fundamental operating system services including:
- Thread scheduling and dispatching
- Interrupt and exception handling
- Synchronization primitives
- Low-level memory management
3. Executive Services
The Executive layer implements higher-level operating system services:
- Object Manager: Manages kernel objects and namespaces
- Memory Manager: Virtual memory management and paging
- Process Manager: Process and thread management
- I/O Manager: Device drivers and file system interface
- Security Reference Monitor: Access control and auditing
Memory Management Architecture
The NT kernel implements a sophisticated virtual memory system that provides each process with its own 4GB virtual address space (on 32-bit systems) or much larger on 64-bit systems.
Memory Management Components
Virtual Memory Manager (VMM)
The VMM handles:
- Page fault handling
- Working set management
- Page file operations
- Memory-mapped files
Memory Pools
The kernel maintains two primary memory pools:
- Paged Pool: Can be swapped to disk, used for less critical data
- Non-Paged Pool: Always remains in physical memory, used for critical kernel structures
Page Table Management
The NT kernel uses a two-level page table structure on x86 systems:
// Example: Virtual address translation
// Virtual Address: 0x12345678
//
// Bits 31-22: Page Directory Index = 0x048 (72 decimal)
// Bits 21-12: Page Table Index = 0x345 (837 decimal)
// Bits 11-0: Offset = 0x678 (1656 decimal)
typedef struct _PTE {
ULONG Valid : 1;
ULONG Write : 1;
ULONG Owner : 1;
ULONG WriteThrough : 1;
ULONG CacheDisable : 1;
ULONG Accessed : 1;
ULONG Dirty : 1;
ULONG LargePage : 1;
ULONG Global : 1;
ULONG CopyOnWrite : 1;
ULONG Prototype : 1;
ULONG reserved : 1;
ULONG PageFrameNumber : 20;
} PTE, *PPTE;
Process and Thread Management
The NT kernel implements a sophisticated process and thread model that supports preemptive multitasking and symmetric multiprocessing.
Process Structure
Each process in the NT kernel is represented by several key data structures:
- EPROCESS: Executive process block (kernel-mode representation)
- PEB (Process Environment Block): User-mode process information
- KPROCESS: Kernel process block
// Simplified EPROCESS structure
typedef struct _EPROCESS {
KPROCESS Pcb; // Kernel process block
PVOID ProcessLock; // Process synchronization
LARGE_INTEGER CreateTime; // Process creation time
LARGE_INTEGER ExitTime; // Process exit time
HANDLE UniqueProcessId; // Process ID
LIST_ENTRY ActiveProcessLinks; // Link in active process list
PVOID VadRoot; // Virtual address descriptor tree
PVOID ObjectTable; // Handle table
PVOID Token; // Security token
// ... many more fields
} EPROCESS, *PEPROCESS;
Thread Scheduling
The NT kernel uses a priority-based, preemptive scheduling algorithm with 32 priority levels (0-31):
Quantum-based Scheduling
Each thread receives a time quantum (typically 10-120ms) during which it can execute before being preempted:
// Thread quantum calculation example
ULONG CalculateQuantum(UCHAR Priority, BOOLEAN IsServer) {
ULONG BaseQuantum = IsServer ? 120 : 60; // milliseconds
if (Priority >= 16) {
// Real-time threads get longer quantum
return BaseQuantum * 2;
} else {
// Variable priority threads
return BaseQuantum + (Priority * 5);
}
}
I/O System Architecture
The NT kernel’s I/O system is built around a layered driver model that provides flexibility and extensibility.
I/O Request Packets (IRPs)
All I/O operations in the NT kernel are handled through I/O Request Packets (IRPs):
// Simplified IRP structure
typedef struct _IRP {
CSHORT Type; // IRP type
USHORT Size; // Size of IRP
PMDL MdlAddress; // Memory descriptor list
ULONG Flags; // IRP flags
NTSTATUS IoStatus; // I/O status
KPROCESSOR_MODE RequestorMode; // Requestor mode
BOOLEAN PendingReturned; // Pending flag
CHAR StackCount; // Number of stack locations
PIO_STACK_LOCATION CurrentLocation; // Current stack location
// ... additional fields
} IRP, *PIRP;
// I/O Stack Location
typedef struct _IO_STACK_LOCATION {
UCHAR MajorFunction; // IRP_MJ_xxx
UCHAR MinorFunction; // IRP_MN_xxx
UCHAR Flags; // Stack flags
UCHAR Control; // Stack control
PDEVICE_OBJECT DeviceObject; // Target device
PFILE_OBJECT FileObject; // File object
union {
// Different parameter structures for different operations
struct {
ULONG Length;
LARGE_INTEGER ByteOffset;
} Read;
struct {
ULONG Length;
LARGE_INTEGER ByteOffset;
} Write;
// ... other operation types
} Parameters;
} IO_STACK_LOCATION, *PIO_STACK_LOCATION;
Driver Types and Hierarchy
The NT kernel supports several types of drivers:
- Highest Level Drivers: File system drivers (NTFS, FAT32)
- Intermediate Drivers: Volume managers, filter drivers
- Lowest Level Drivers: Hardware device drivers
Object Management System
The NT kernel implements a unified object model where all system resources are represented as objects.
Object Types
Common object types include:
- Process and Thread objects
- File and Directory objects
- Event and Semaphore objects
- Registry Key objects
- Device objects
Object Manager Functions
// Object creation example
NTSTATUS CreateObjectExample() {
OBJECT_ATTRIBUTES ObjectAttributes;
UNICODE_STRING ObjectName;
HANDLE EventHandle;
NTSTATUS Status;
RtlInitUnicodeString(&ObjectName, L"\\BaseNamedObjects\\MyEvent");
InitializeObjectAttributes(&ObjectAttributes,
&ObjectName,
OBJ_CASE_INSENSITIVE,
NULL,
NULL);
Status = ZwCreateEvent(&EventHandle,
EVENT_ALL_ACCESS,
&ObjectAttributes,
SynchronizationEvent,
FALSE);
return Status;
}
Object Namespace
The NT kernel maintains a hierarchical namespace for all objects:
Security Architecture
The NT kernel implements comprehensive security through the Security Reference Monitor (SRM).
Access Control Model
Security in NT is based on:
- Security Identifiers (SIDs): Unique identifiers for users and groups
- Access Tokens: Contain security information for processes/threads
- Security Descriptors: Define permissions for objects
- Access Control Lists (ACLs): List of access control entries
// Access token structure (simplified)
typedef struct _TOKEN {
LUID TokenId; // Token identifier
LUID AuthenticationId; // Logon session identifier
LARGE_INTEGER ExpirationTime; // Token expiration
TOKEN_TYPE TokenType; // Primary or impersonation
SECURITY_IMPERSONATION_LEVEL ImpersonationLevel;
TOKEN_SOURCE TokenSource; // Token source
PSID_AND_ATTRIBUTES UserAndGroups; // User and group SIDs
PLUID_AND_ATTRIBUTES Privileges; // Privileges
// ... additional fields
} TOKEN, *PTOKEN;
// Security descriptor structure
typedef struct _SECURITY_DESCRIPTOR {
UCHAR Revision; // Descriptor revision
UCHAR Sbz1; // Reserved
SECURITY_DESCRIPTOR_CONTROL Control; // Control flags
PSID Owner; // Owner SID
PSID Group; // Primary group SID
PACL Sacl; // System ACL
PACL Dacl; // Discretionary ACL
} SECURITY_DESCRIPTOR, *PSECURITY_DESCRIPTOR;
Privilege System
The NT kernel implements a fine-grained privilege system with privileges like:
- SeDebugPrivilege: Debug other processes
- SeBackupPrivilege: Bypass file security for backup
- SeLoadDriverPrivilege: Load device drivers
- SeShutdownPrivilege: Shut down the system
Synchronization Mechanisms
The NT kernel provides various synchronization primitives for coordinating access to shared resources.
Kernel Synchronization Objects
- Mutexes: Mutual exclusion with ownership
- Semaphores: Counting synchronization
- Events: Signaling mechanisms
- Critical Sections: Fast user-mode synchronization
- Spin Locks: High-performance kernel synchronization
// Spin lock example
KSPIN_LOCK MySpinLock;
KIRQL OldIrql;
// Initialize spin lock
KeInitializeSpinLock(&MySpinLock);
// Acquire spin lock
KeAcquireSpinLock(&MySpinLock, &OldIrql);
// Critical section code here
// Access shared resource
// Release spin lock
KeReleaseSpinLock(&MySpinLock, OldIrql);
// Fast mutex example for better performance
FAST_MUTEX MyFastMutex;
ExInitializeFastMutex(&MyFastMutex);
// Acquire fast mutex
ExAcquireFastMutex(&MyFastMutex);
// Critical section
// Modify shared data structure
// Release fast mutex
ExReleaseFastMutex(&MyFastMutex);
Performance and Scalability Features
Symmetric Multiprocessing (SMP)
The NT kernel was designed from the ground up to support multiple processors:
- Per-processor data structures
- Processor affinity control
- Load balancing algorithms
- NUMA (Non-Uniform Memory Access) support
Kernel Optimizations
- Lazy evaluation: Defer expensive operations when possible
- Copy-on-write: Optimize memory usage for process creation
- Lookaside lists: Fast allocation of frequently used objects
- Working set optimization: Intelligent memory management
// Lookaside list example
NPAGED_LOOKASIDE_LIST MyLookasideList;
// Initialize lookaside list
ExInitializeNPagedLookasideList(&MyLookasideList,
NULL, // Allocate function
NULL, // Free function
0, // Flags
sizeof(MY_STRUCTURE), // Size
'Tag1', // Pool tag
0); // Depth
// Allocate from lookaside list
PMY_STRUCTURE pStruct = ExAllocateFromNPagedLookasideList(&MyLookasideList);
// Use the structure
if (pStruct != NULL) {
// Initialize and use structure
// ...
// Free back to lookaside list
ExFreeToNPagedLookasideList(&MyLookasideList, pStruct);
}
Debugging and Diagnostic Features
Kernel Debugging Support
The NT kernel provides extensive debugging capabilities:
- Blue Screen of Death (BSOD): System crash information
- Kernel debugger integration
- Event Tracing for Windows (ETW)
- System call tracing
- Memory pool tracking
Crash Dump Analysis
// Crash dump header structure
typedef struct _DUMP_HEADER {
ULONG Signature; // 'DUMP' or 'PAGE'
ULONG ValidDump; // 'DUMP'
ULONG MajorVersion; // Major version
ULONG MinorVersion; // Minor version
ULONG DirectoryTableBase; // Page directory
PULONG PfnDataBase; // Page frame database
PLIST_ENTRY PsLoadedModuleList; // Loaded modules
PLIST_ENTRY PsActiveProcessHead; // Active processes
ULONG MachineImageType; // Machine type
ULONG NumberProcessors; // Processor count
ULONG BugCheckCode; // Bug check code
// ... additional crash information
} DUMP_HEADER, *PDUMP_HEADER;
Evolution and Modern Enhancements
Windows 10/11 Kernel Improvements
Recent versions of the NT kernel include:
- Kernel Control Flow Guard (kCFG): Enhanced security against ROP attacks
- Hypervisor Code Integrity (HVCI): Hardware-enforced code integrity
- Kernel Address Space Layout Randomization (kASLR)
- Memory compression: Improved memory utilization
- Container support: Windows containers and Hyper-V isolation
Performance Monitoring
Modern NT kernel includes advanced performance monitoring:
// ETW (Event Tracing for Windows) example
REGHANDLE RegistrationHandle;
EVENT_DESCRIPTOR EventDescriptor;
// Register ETW provider
EventRegister(&MyProviderGuid,
NULL, // Enable callback
NULL, // Context
&RegistrationHandle);
// Define event
EventDescCreate(&EventDescriptor,
1, // Event ID
0, // Version
0, // Channel
TRACE_LEVEL_INFORMATION, // Level
0, // Task
0, // OpCode
0); // Keyword
// Write event
EventWrite(RegistrationHandle,
&EventDescriptor,
0, // User data count
NULL); // User data
// Unregister
EventUnregister(RegistrationHandle);
Best Practices for Kernel Development
Driver Development Guidelines
- Use appropriate IRQL levels: Understand when code runs at different interrupt levels
- Minimize time in critical sections: Avoid long-running operations while holding locks
- Handle all error conditions: Always check return values and handle failures gracefully
- Use proper memory management: Match allocations with deallocations
- Follow coding standards: Use consistent naming and documentation
Common Pitfalls
- IRQL violations: Calling pageable code at elevated IRQL
- Memory leaks: Not freeing allocated memory
- Deadlocks: Improper lock ordering
- Buffer overruns: Not validating input parameters
- Resource leaks: Not releasing handles and objects
Conclusion
The Windows NT kernel represents a sophisticated and well-engineered operating system foundation that has evolved over three decades. Its hybrid architecture combines the best aspects of different kernel designs, providing excellent performance while maintaining reliability and security.
Key strengths of the NT kernel include:
- Robust architecture: Clean separation between user and kernel modes
- Scalability: Excellent SMP and NUMA support
- Security: Comprehensive access control and privilege system
- Extensibility: Layered driver model and object-oriented design
- Portability: HAL abstraction enables multi-platform support
Understanding the NT kernel’s design and implementation is crucial for system developers, security professionals, and anyone working with Windows at a low level. The kernel’s continued evolution demonstrates Microsoft’s commitment to maintaining a modern, secure, and high-performance operating system foundation.
As Windows continues to evolve with cloud computing, containers, and modern security requirements, the NT kernel remains the stable foundation that enables these advanced features while maintaining backward compatibility with decades of existing software.
- Introduction to Windows NT Kernel
- NT Kernel Architecture Overview
- Memory Management Architecture
- Process and Thread Management
- I/O System Architecture
- Object Management System
- Security Architecture
- Synchronization Mechanisms
- Performance and Scalability Features
- Debugging and Diagnostic Features
- Evolution and Modern Enhancements
- Best Practices for Kernel Development
- Conclusion