Introduction to Virtual Networks and Software-Defined Networking
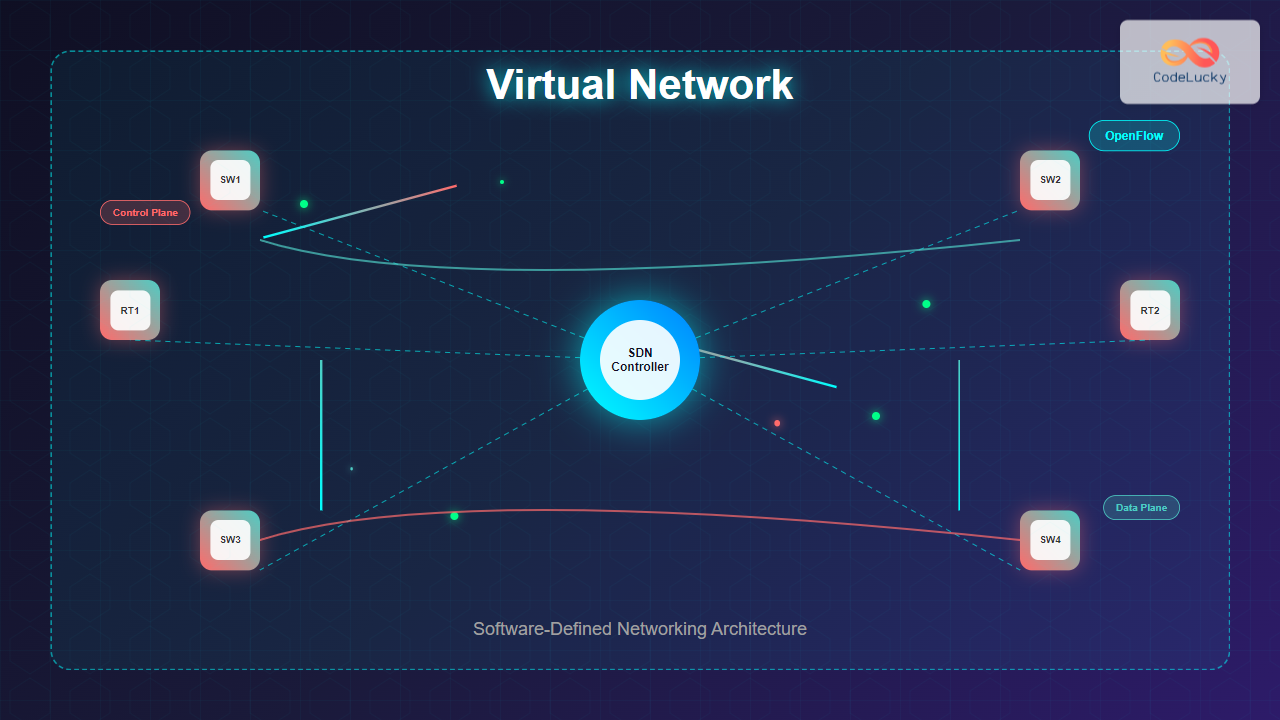
Virtual networks represent a fundamental shift in how we design, implement, and manage network infrastructure. Software-Defined Networking (SDN) decouples network control from the underlying hardware, enabling centralized management and programmable network behavior. This revolutionary approach transforms traditional networking by abstracting network services from physical infrastructure.
Unlike conventional networks where each device makes independent forwarding decisions, SDN centralizes network intelligence in a software-based controller. This separation of the control plane from the data plane enables dynamic network configuration, improved security, and enhanced scalability.
Core Components of Software-Defined Networking
SDN Controller Architecture
The SDN controller serves as the network’s brain, maintaining a global view of the entire network topology. It communicates with network devices through standardized protocols like OpenFlow, making centralized decisions about traffic routing and network policies.
Key controller functions include:
- Topology Discovery: Automatically mapping network structure and device connections
- Flow Management: Installing and managing flow rules across network devices
- Policy Enforcement: Implementing security and quality-of-service policies
- Network Optimization: Dynamically adjusting paths based on traffic conditions
Data Plane vs Control Plane Separation
Traditional networking combines both planes within each device, creating complexity and limited flexibility. SDN’s separation enables:
- Centralized Control: Single point for network-wide decisions and policies
- Simplified Devices: Switches become simple forwarding elements
- Programmability: Network behavior modification through software
- Vendor Independence: Standardized interfaces reduce vendor lock-in
Network Virtualization Technologies
Virtual LANs (VLANs)
VLANs create logical network segments within physical infrastructure, enabling traffic isolation and improved security. Each VLAN operates as a separate broadcast domain, preventing unnecessary traffic propagation.
VLAN Implementation Example:
# Configure VLAN on Linux bridge
sudo ip link add name br-vlan100 type bridge
sudo ip link set br-vlan100 up
# Add interface to VLAN
sudo bridge vlan add dev eth0 vid 100 pvid untagged
sudo bridge vlan show
Virtual Extensible LAN (VXLAN)
VXLAN extends Layer 2 networks across Layer 3 infrastructure using UDP encapsulation. This technology enables network virtualization in cloud environments by creating overlay networks that span multiple physical locations.
VXLAN Configuration Example:
# Create VXLAN interface
sudo ip link add vxlan100 type vxlan id 100 \
group 239.1.1.1 dev eth0 dstport 4789
# Configure VXLAN endpoint
sudo ip addr add 10.0.1.1/24 dev vxlan100
sudo ip link set vxlan100 up
# Verify VXLAN tunnel
sudo ip -d link show vxlan100
OpenFlow Protocol and Communication
OpenFlow Fundamentals
OpenFlow standardizes communication between SDN controllers and network switches. It defines how controllers install flow rules and receive network events, enabling vendor-agnostic network programmability.
Flow Table Structure:
| Match Fields | Priority | Counters | Instructions | Timeouts |
|---|---|---|---|---|
| Source IP, Destination Port | 100 | Packets: 1523 | Forward to Port 2 | Idle: 300s |
| Ethernet Type: IPv4 | 50 | Bytes: 98,432 | Drop Packet | Hard: 600s |
Flow Rule Programming
Controllers program switches by installing flow rules that specify packet handling actions. Each rule contains match criteria and corresponding instructions for packet processing.
Example Flow Rule Installation:
# Python OpenFlow controller example (using Ryu framework)
from ryu.controller import ofp_event
from ryu.controller.handler import set_ev_cls
from ryu.ofproto import ofproto_v1_3
def add_flow(self, datapath, priority, match, actions):
ofproto = datapath.ofproto
parser = datapath.ofproto_parser
# Create flow modification message
inst = [parser.OFPInstructionActions(
ofproto.OFPIT_APPLY_ACTIONS, actions)]
mod = parser.OFPFlowMod(
datapath=datapath, priority=priority,
match=match, instructions=inst)
# Send flow rule to switch
datapath.send_msg(mod)
# Install specific flow rule
match = parser.OFPMatch(in_port=1, eth_dst='00:00:00:00:00:01')
actions = [parser.OFPActionOutput(2)]
self.add_flow(datapath, 1, match, actions)
Virtual Network Implementation Examples
Container Networking with Docker
Container platforms leverage virtual networking extensively, creating isolated network namespaces for application containers while enabling controlled communication.
Docker Network Creation:
# Create custom bridge network
docker network create --driver bridge \
--subnet=192.168.1.0/24 \
--gateway=192.168.1.1 \
custom-network
# Run container on custom network
docker run -d --name web-server \
--network custom-network \
--ip 192.168.1.10 \
nginx:latest
# Inspect network configuration
docker network inspect custom-network
Kubernetes Virtual Networking
Kubernetes implements sophisticated virtual networking using Container Network Interface (CNI) plugins. Each pod receives a unique IP address within the cluster’s virtual network.
Pod Network Configuration:
# Kubernetes NetworkPolicy example
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: web-netpol
spec:
podSelector:
matchLabels:
app: web
policyTypes:
- Ingress
- Egress
ingress:
- from:
- podSelector:
matchLabels:
app: frontend
ports:
- protocol: TCP
port: 80
Cloud Virtual Networking
Virtual Private Clouds (VPC)
Virtual Private Clouds provide isolated network environments within public cloud infrastructure. VPCs enable secure, scalable networking with complete control over IP addressing, subnets, and routing.
AWS VPC Configuration Example:
# Create VPC using AWS CLI
aws ec2 create-vpc --cidr-block 10.0.0.0/16 \
--tag-specifications 'ResourceType=vpc,Tags=[{Key=Name,Value=MyVPC}]'
# Create subnet within VPC
aws ec2 create-subnet --vpc-id vpc-12345678 \
--cidr-block 10.0.1.0/24 \
--availability-zone us-west-2a
# Create internet gateway
aws ec2 create-internet-gateway \
--tag-specifications 'ResourceType=internet-gateway,Tags=[{Key=Name,Value=MyIGW}]'
Software-Defined WAN (SD-WAN)
SD-WAN extends SDN principles to wide area networks, providing centralized policy management and dynamic path selection across multiple connection types including MPLS, broadband, and cellular.
SD-WAN Benefits:
- Cost Reduction: Utilizing cheaper internet connections alongside MPLS
- Improved Performance: Dynamic path selection based on application requirements
- Simplified Management: Centralized policy configuration and monitoring
- Enhanced Security: Integrated firewall and encryption capabilities
Network Security in Virtual Environments
Micro-segmentation
Micro-segmentation creates granular security zones within virtual networks, limiting lateral movement of threats. This approach applies zero-trust principles by default-deny policies.
Implementation using iptables:
# Create micro-segmentation rules
# Allow web servers to communicate with database on port 3306
iptables -A FORWARD -s 10.0.1.0/24 -d 10.0.2.0/24 -p tcp --dport 3306 -j ACCEPT
# Block all other inter-subnet communication
iptables -A FORWARD -s 10.0.1.0/24 -d 10.0.2.0/24 -j DROP
# Log blocked attempts
iptables -A FORWARD -j LOG --log-prefix "BLOCKED: "
Virtual Firewall Integration
Virtual networks integrate distributed firewalls that move security closer to workloads, providing consistent policy enforcement regardless of traffic patterns.
Performance Optimization and Troubleshooting
Network Performance Monitoring
Virtual networks require specialized monitoring approaches due to their dynamic nature and software-defined characteristics. Flow-based monitoring provides visibility into traffic patterns and performance metrics.
Performance Monitoring Script:
# Monitor virtual interface performance
#!/bin/bash
interface="veth0"
echo "Monitoring $interface performance..."
while true; do
# Get interface statistics
rx_bytes=$(cat /sys/class/net/$interface/statistics/rx_bytes)
tx_bytes=$(cat /sys/class/net/$interface/statistics/tx_bytes)
rx_packets=$(cat /sys/class/net/$interface/statistics/rx_packets)
tx_packets=$(cat /sys/class/net/$interface/statistics/tx_packets)
echo "$(date): RX: $rx_bytes bytes ($rx_packets packets), TX: $tx_bytes bytes ($tx_packets packets)"
sleep 5
done
Common Troubleshooting Techniques
Virtual network troubleshooting involves multiple layers, from physical connectivity to virtual overlay configuration. Key diagnostic commands include:
# Check virtual interface status
ip link show type veth
ip netns list
# Verify VXLAN tunnel endpoints
bridge fdb show dev vxlan100
# Test connectivity between namespaces
ip netns exec ns1 ping 10.0.1.2
# Monitor OpenFlow messages
tcpdump -i any port 6633 -v
# Check flow table entries
ovs-ofctl dump-flows br0
Future Trends and Emerging Technologies
Intent-Based Networking (IBN)
Intent-Based Networking represents the next evolution of SDN, where administrators express business intent and the system automatically configures and maintains the network to achieve desired outcomes.
Network Function Virtualization (NFV)
NFV complements SDN by virtualizing network services like firewalls, load balancers, and intrusion detection systems. This approach enables rapid service deployment and scaling without dedicated hardware.
Service Function Chaining Example:
# Service Function Chain definition
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: security-chain
spec:
hosts:
- webapp
http:
- match:
- headers:
user-type:
exact: premium
route:
- destination:
host: firewall-service
weight: 100
- destination:
host: ids-service
weight: 100
- destination:
host: webapp
weight: 100
Best Practices for Virtual Network Design
Scalability Considerations
Design virtual networks with growth in mind, implementing hierarchical addressing schemes and automated provisioning processes. Consider controller scalability and distributed control plane architectures for large deployments.
Security Implementation Guidelines
- Default Deny: Implement restrictive policies by default
- Principle of Least Privilege: Grant minimum required network access
- Regular Auditing: Continuously review and update network policies
- Encryption: Secure overlay traffic with appropriate encryption methods
Conclusion
Virtual networks and software-defined networking fundamentally transform how organizations design, deploy, and manage network infrastructure. By separating control from data planes, SDN enables unprecedented flexibility, security, and automation capabilities.
The combination of network virtualization technologies like VXLANs, VLANs, and overlay networks with centralized SDN controllers creates powerful platforms for modern applications. As organizations continue adopting cloud-native architectures and containerized applications, understanding virtual networking becomes essential for system administrators, network engineers, and DevOps professionals.
Success with virtual networks requires mastering both theoretical concepts and practical implementation skills. Start with simple virtualization techniques, progress to SDN controllers and OpenFlow, and gradually incorporate advanced features like micro-segmentation and intent-based networking. The investment in learning these technologies pays dividends through improved network agility, security, and operational efficiency.
- Introduction to Virtual Networks and Software-Defined Networking
- Core Components of Software-Defined Networking
- Network Virtualization Technologies
- OpenFlow Protocol and Communication
- Virtual Network Implementation Examples
- Cloud Virtual Networking
- Network Security in Virtual Environments
- Performance Optimization and Troubleshooting
- Future Trends and Emerging Technologies
- Best Practices for Virtual Network Design
- Conclusion