The s6 service manager represents a revolutionary approach to Linux process supervision, offering a lightweight and secure alternative to traditional init systems like systemd. Developed by Laurent Bercot, s6 follows the Unix philosophy of doing one thing well, providing robust service management without the complexity of monolithic solutions.
What is s6 Linux Service Manager?
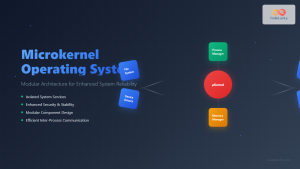
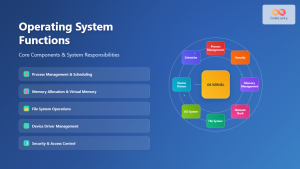
s6 is a process supervision suite designed for Unix-like systems, including Linux. Unlike traditional init systems, s6 focuses exclusively on process supervision and service management, making it incredibly lightweight and secure. The system consists of several interconnected components that work together to provide reliable service supervision.
Key Features of s6
- Minimal Resource Usage: Extremely low memory footprint and CPU usage
- Security-First Design: Built with security principles from the ground up
- Fast Boot Times: Services start quickly and efficiently
- Reliable Supervision: Automatic service restart on failure
- Logging Integration: Built-in logging capabilities
- No Dependencies: Self-contained with minimal external requirements
Installing s6 on Linux
The installation process varies depending on your Linux distribution. Here’s how to install s6 on different systems:
Ubuntu/Debian Installation
# Update package repositories
sudo apt update
# Install s6 and related tools
sudo apt install s6 s6-tools
# Verify installation
s6-svscan --versionCentOS/RHEL Installation
# Install EPEL repository first
sudo yum install epel-release
# Install s6
sudo yum install s6
# For newer versions, use dnf
sudo dnf install s6Arch Linux Installation
# Install from AUR
yay -S s6
# Or using pacman if available in repositories
sudo pacman -S s6Understanding s6 Architecture
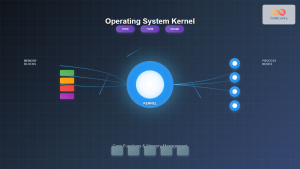
s6 follows a modular architecture with several key components:
Core Components
- s6-svscan: The main supervisor daemon
- s6-supervise: Individual service supervisor
- s6-svc: Service control utility
- s6-svstat: Service status checker
- s6-log: Logging daemon
Basic s6 Service Management
Let’s explore how to create and manage services with s6. The process involves creating service directories with specific files that define service behavior.
Creating Your First s6 Service
Here’s how to create a simple web server service:
# Create service directory structure
sudo mkdir -p /etc/s6/services/webserver
# Create the run script
sudo tee /etc/s6/services/webserver/run << 'EOF'
#!/bin/sh
exec python3 -m http.server 8080
EOF
# Make run script executable
sudo chmod +x /etc/s6/services/webserver/run
# Create log directory and script
sudo mkdir -p /etc/s6/services/webserver/log
sudo tee /etc/s6/services/webserver/log/run << 'EOF'
#!/bin/sh
exec s6-log t /var/log/webserver
EOF
sudo chmod +x /etc/s6/services/webserver/log/runService Directory Structure
A typical s6 service directory contains these files:
/etc/s6/services/myservice/
├── run # Main service script
├── finish # Cleanup script (optional)
├── down # Prevents auto-start (optional)
├── timeout-kill # Kill timeout (optional)
└── log/
└── run # Logging scriptService Control Commands
s6 provides several utilities for managing services. Here are the essential commands:
Starting and Stopping Services
# Start a service
sudo s6-svc -u /etc/s6/services/webserver
# Stop a service
sudo s6-svc -d /etc/s6/services/webserver
# Restart a service
sudo s6-svc -r /etc/s6/services/webserver
# Send TERM signal
sudo s6-svc -t /etc/s6/services/webserver
# Send KILL signal
sudo s6-svc -k /etc/s6/services/webserverChecking Service Status
# Check service status
s6-svstat /etc/s6/services/webserver
# Example output:
# up (pid 1234) 15 seconds
# Check multiple services
s6-svstat /etc/s6/services/*Advanced Service Configuration
s6 offers advanced configuration options for complex service management scenarios.
Service Dependencies
Create service dependencies using the notification system:
# Create database service
sudo mkdir -p /etc/s6/services/database
sudo tee /etc/s6/services/database/run << 'EOF'
#!/bin/sh
# Start database
exec mysqld --no-daemon
EOF
# Create web application with database dependency
sudo mkdir -p /etc/s6/services/webapp
sudo tee /etc/s6/services/webapp/run << 'EOF'
#!/bin/sh
# Wait for database to be ready
s6-svwait -u /etc/s6/services/database
# Start web application
exec /usr/local/bin/webapp
EOFEnvironment Variables
Configure service environment using the env directory:
# Create environment directory
sudo mkdir -p /etc/s6/services/webapp/env
# Set environment variables
echo "production" | sudo tee /etc/s6/services/webapp/env/NODE_ENV
echo "5432" | sudo tee /etc/s6/services/webapp/env/DB_PORT
echo "/var/log/app.log" | sudo tee /etc/s6/services/webapp/env/LOG_FILEUser and Group Management
Run services as specific users for enhanced security:
# Create service user
sudo useradd -r -s /bin/false webapp-user
# Modify run script to use specific user
sudo tee /etc/s6/services/webapp/run << 'EOF'
#!/bin/sh
exec s6-setuidgid webapp-user /usr/local/bin/webapp
EOFLogging with s6
s6 integrates seamlessly with s6-log for robust logging capabilities:
Basic Logging Setup
# Create log service
sudo mkdir -p /etc/s6/services/myapp/log
sudo tee /etc/s6/services/myapp/log/run << 'EOF'
#!/bin/sh
exec s6-log -b t /var/log/myapp
EOF
sudo chmod +x /etc/s6/services/myapp/log/run
# Create log directory
sudo mkdir -p /var/log/myapp
sudo chown nobody:nobody /var/log/myappAdvanced Logging Configuration
# Log rotation and filtering
sudo tee /etc/s6/services/myapp/log/run << 'EOF'
#!/bin/sh
exec s6-log -b \
s1000000 n20 \
t /var/log/myapp
EOFThis configuration:
s1000000: Rotate logs at 1MBn20: Keep 20 log filest: Add timestamps
s6 vs Other Init Systems
Understanding how s6 compares to other init systems helps in making informed decisions:
| Feature | s6 | systemd | SysV Init |
|---|---|---|---|
| Memory Usage | Very Low | High | Low |
| Boot Speed | Fast | Fast | Slow |
| Complexity | Simple | Complex | Simple |
| Security | High | Medium | Medium |
| Dependencies | Minimal | Many | Few |
Real-World Examples
Let’s examine practical implementations of s6 in different scenarios:
Web Server with Load Balancer
# Nginx service
sudo mkdir -p /etc/s6/services/nginx
sudo tee /etc/s6/services/nginx/run << 'EOF'
#!/bin/sh
exec nginx -g "daemon off;"
EOF
# Application server instances
for i in {1..3}; do
sudo mkdir -p /etc/s6/services/app-$i
sudo tee /etc/s6/services/app-$i/run << EOF
#!/bin/sh
export PORT=$((8000 + $i))
exec s6-setuidgid app-user /usr/local/bin/app
EOF
doneDatabase with Backup Service
# PostgreSQL service
sudo mkdir -p /etc/s6/services/postgresql
sudo tee /etc/s6/services/postgresql/run << 'EOF'
#!/bin/sh
exec s6-setuidgid postgres \
postgres -D /var/lib/postgresql/data
EOF
# Backup service
sudo mkdir -p /etc/s6/services/db-backup
sudo tee /etc/s6/services/db-backup/run << 'EOF'
#!/bin/sh
# Wait for database
s6-svwait -u /etc/s6/services/postgresql
# Run periodic backup
while true; do
pg_dump mydb > /backups/backup-$(date +%Y%m%d).sql
sleep 3600 # Backup every hour
done
EOFTroubleshooting s6 Services
Common issues and their solutions when working with s6:
Service Won’t Start
# Check service status
s6-svstat /etc/s6/services/myservice
# Check logs
tail -f /var/log/myservice/current
# Verify run script permissions
ls -la /etc/s6/services/myservice/run
# Test run script manually
sudo /etc/s6/services/myservice/runHigh Memory Usage
# Monitor service resource usage
ps aux | grep myservice
# Check for memory leaks
valgrind --leak-check=full /usr/local/bin/myservice
# Limit service resources
sudo tee /etc/s6/services/myservice/run << 'EOF'
#!/bin/sh
# Limit memory to 100MB
ulimit -m 102400
exec /usr/local/bin/myservice
EOFSecurity Best Practices
Implementing security measures with s6 services:
Service Isolation
# Create dedicated user for each service
sudo useradd -r -s /bin/false service-user
# Use chroot for additional isolation
sudo tee /etc/s6/services/isolated-app/run << 'EOF'
#!/bin/sh
exec chroot /var/chroot/myapp \
s6-setuidgid app-user /bin/myapp
EOFResource Limits
# Limit file descriptors and processes
sudo tee /etc/s6/services/limited-app/run << 'EOF'
#!/bin/sh
# Set resource limits
ulimit -n 1024 # Max 1024 file descriptors
ulimit -u 50 # Max 50 processes
ulimit -f 10240 # Max 10MB file size
exec s6-setuidgid app-user /usr/local/bin/app
EOFPerformance Optimization
Optimize s6 services for better performance:
Parallel Service Startup
# Use s6-rc for dependency management
sudo s6-rc-compile /etc/s6-rc/compiled /etc/s6-rc/source
# Start all services
sudo s6-rc -up change defaultMonitoring and Metrics
# Create monitoring service
sudo mkdir -p /etc/s6/services/monitor
sudo tee /etc/s6/services/monitor/run << 'EOF'
#!/bin/sh
while true; do
# Check all services
for service in /etc/s6/services/*/; do
if ! s6-svstat "$service" | grep -q "up"; then
echo "Service $(basename $service) is down" | \
logger -t s6-monitor
fi
done
sleep 30
done
EOFMigration from Other Init Systems
Migrating existing services to s6:
From systemd
# Convert systemd unit file
# Original: /etc/systemd/system/myapp.service
# [Unit]
# Description=My Application
# After=network.target
#
# [Service]
# Type=simple
# ExecStart=/usr/local/bin/myapp
# User=myapp
# Restart=always
# s6 equivalent
sudo mkdir -p /etc/s6/services/myapp
sudo tee /etc/s6/services/myapp/run << 'EOF'
#!/bin/sh
exec s6-setuidgid myapp /usr/local/bin/myapp
EOFConclusion
s6 provides a lightweight, secure, and efficient approach to service management on Linux systems. Its minimal design philosophy makes it an excellent choice for containerized environments, embedded systems, and security-conscious deployments. By following the examples and best practices outlined in this guide, you can effectively implement s6 for robust service supervision.
The modular architecture and Unix philosophy behind s6 ensure that your system remains maintainable and secure while providing the reliability needed for production environments. Whether you’re managing a simple web server or a complex microservices architecture, s6 offers the tools and flexibility to meet your service management needs.