Introduction to Role-based Access Control (RBAC)
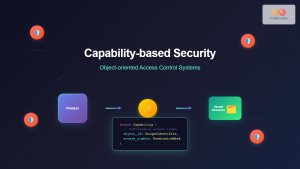
Role-based Access Control (RBAC) is a security paradigm that restricts system access based on user roles within an organization. Unlike traditional discretionary access control (DAC) or mandatory access control (MAC), RBAC provides a middle-ground approach that balances security with administrative efficiency.
In RBAC, permissions are assigned to roles rather than individual users. Users are then assigned to appropriate roles, automatically inheriting the permissions associated with those roles. This model significantly simplifies permission management in large-scale systems.
Core RBAC Components
Users, Roles, and Permissions
The RBAC model consists of three fundamental elements:
- Users: Individual entities (people, processes, or services) that need system access
- Roles: Job functions or titles that define levels of access within an organization
- Permissions: Specific access rights to system resources or operations
RBAC Relationships
The relationship between these components follows specific rules:
- A user can be assigned multiple roles
- A role can have multiple users
- A role can contain multiple permissions
- A permission can be assigned to multiple roles
RBAC Models and Levels
RBAC0 – Core RBAC
The foundational level that includes:
- User assignment to roles
- Permission assignment to roles
- User-role sessions
RBAC1 – Hierarchical RBAC
Extends RBAC0 with role hierarchies, where senior roles inherit permissions from junior roles.
RBAC2 – Constrained RBAC
Adds constraints such as:
- Mutual Exclusion: A user cannot be assigned conflicting roles simultaneously
- Cardinality: Limits on the number of users in a role or roles per user
- Prerequisites: Required roles before assignment to higher-level roles
RBAC3 – Consolidated RBAC
Combines all features from RBAC0, RBAC1, and RBAC2.
RBAC Implementation Architecture
Implementation Steps
Step 1: Define Organizational Roles
Start by analyzing your organization’s structure and identifying distinct job functions:
roles:
- name: "admin"
description: "System administrator with full access"
- name: "manager"
description: "Department manager with team oversight"
- name: "employee"
description: "Regular employee with basic access"
- name: "guest"
description: "Temporary user with limited access"
Step 2: Map Permissions to Resources
permissions:
- name: "user.create"
resource: "users"
action: "create"
- name: "user.read"
resource: "users"
action: "read"
- name: "user.update"
resource: "users"
action: "update"
- name: "user.delete"
resource: "users"
action: "delete"
- name: "report.generate"
resource: "reports"
action: "generate"
Step 3: Assign Permissions to Roles
role_permissions:
admin:
- user.create
- user.read
- user.update
- user.delete
- report.generate
manager:
- user.read
- user.update
- report.generate
employee:
- user.read
guest:
- user.read
Database Schema Design
A typical RBAC database schema includes the following tables:
-- Users table
CREATE TABLE users (
user_id INT PRIMARY KEY AUTO_INCREMENT,
username VARCHAR(50) UNIQUE NOT NULL,
email VARCHAR(100) UNIQUE NOT NULL,
password_hash VARCHAR(255) NOT NULL,
created_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
-- Roles table
CREATE TABLE roles (
role_id INT PRIMARY KEY AUTO_INCREMENT,
role_name VARCHAR(50) UNIQUE NOT NULL,
description TEXT,
created_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
-- Permissions table
CREATE TABLE permissions (
permission_id INT PRIMARY KEY AUTO_INCREMENT,
permission_name VARCHAR(100) UNIQUE NOT NULL,
resource VARCHAR(50) NOT NULL,
action VARCHAR(50) NOT NULL,
description TEXT
);
-- User-Role assignments
CREATE TABLE user_roles (
user_id INT,
role_id INT,
assigned_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP,
PRIMARY KEY (user_id, role_id),
FOREIGN KEY (user_id) REFERENCES users(user_id),
FOREIGN KEY (role_id) REFERENCES roles(role_id)
);
-- Role-Permission assignments
CREATE TABLE role_permissions (
role_id INT,
permission_id INT,
granted_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP,
PRIMARY KEY (role_id, permission_id),
FOREIGN KEY (role_id) REFERENCES roles(role_id),
FOREIGN KEY (permission_id) REFERENCES permissions(permission_id)
);
Programming Implementation Examples
Python RBAC Implementation
class RBACSystem:
def __init__(self):
self.users = {}
self.roles = {}
self.permissions = {}
self.user_roles = {}
self.role_permissions = {}
def create_user(self, user_id, username):
"""Create a new user"""
self.users[user_id] = {
'username': username,
'active': True
}
self.user_roles[user_id] = set()
def create_role(self, role_id, role_name):
"""Create a new role"""
self.roles[role_id] = {
'name': role_name,
'active': True
}
self.role_permissions[role_id] = set()
def create_permission(self, perm_id, resource, action):
"""Create a new permission"""
self.permissions[perm_id] = {
'resource': resource,
'action': action
}
def assign_role_to_user(self, user_id, role_id):
"""Assign a role to a user"""
if user_id in self.users and role_id in self.roles:
self.user_roles[user_id].add(role_id)
return True
return False
def assign_permission_to_role(self, role_id, perm_id):
"""Assign a permission to a role"""
if role_id in self.roles and perm_id in self.permissions:
self.role_permissions[role_id].add(perm_id)
return True
return False
def check_permission(self, user_id, resource, action):
"""Check if user has permission for resource/action"""
if user_id not in self.users:
return False
user_roles = self.user_roles.get(user_id, set())
for role_id in user_roles:
role_perms = self.role_permissions.get(role_id, set())
for perm_id in role_perms:
perm = self.permissions[perm_id]
if perm['resource'] == resource and perm['action'] == action:
return True
return False
# Example usage
rbac = RBACSystem()
# Create users
rbac.create_user(1, "alice")
rbac.create_user(2, "bob")
# Create roles
rbac.create_role(1, "admin")
rbac.create_role(2, "user")
# Create permissions
rbac.create_permission(1, "users", "read")
rbac.create_permission(2, "users", "write")
rbac.create_permission(3, "reports", "generate")
# Assign permissions to roles
rbac.assign_permission_to_role(1, 1) # admin can read users
rbac.assign_permission_to_role(1, 2) # admin can write users
rbac.assign_permission_to_role(1, 3) # admin can generate reports
rbac.assign_permission_to_role(2, 1) # user can read users
# Assign roles to users
rbac.assign_role_to_user(1, 1) # alice is admin
rbac.assign_role_to_user(2, 2) # bob is user
# Check permissions
print(rbac.check_permission(1, "users", "write")) # True (alice/admin)
print(rbac.check_permission(2, "users", "write")) # False (bob/user)
print(rbac.check_permission(2, "users", "read")) # True (bob/user)
Node.js Express Middleware Implementation
const rbacMiddleware = (requiredPermission) => {
return async (req, res, next) => {
try {
const userId = req.user.id;
const [resource, action] = requiredPermission.split(':');
// Get user roles from database
const userRoles = await getUserRoles(userId);
// Check if any role has the required permission
const hasPermission = await checkUserPermission(
userRoles,
resource,
action
);
if (hasPermission) {
next();
} else {
res.status(403).json({
error: 'Insufficient permissions'
});
}
} catch (error) {
res.status(500).json({
error: 'Permission check failed'
});
}
};
};
// Usage in routes
app.get('/admin/users',
authenticateToken,
rbacMiddleware('users:read'),
(req, res) => {
// Handle request
}
);
app.post('/admin/users',
authenticateToken,
rbacMiddleware('users:create'),
(req, res) => {
// Handle request
}
);
RBAC in Operating Systems
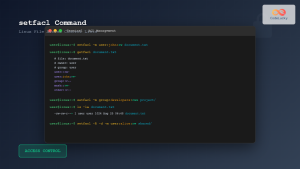
Linux RBAC Implementation
Linux systems implement RBAC-like functionality through groups and sudo configurations:
# Create groups (roles)
sudo groupadd developers
sudo groupadd sysadmins
sudo groupadd dbusers
# Add users to groups
sudo usermod -a -G developers john
sudo usermod -a -G sysadmins alice
sudo usermod -a -G dbusers bob
# Configure sudo permissions in /etc/sudoers
%sysadmins ALL=(ALL) ALL
%developers ALL=(www-data) /usr/bin/systemctl restart apache2
%dbusers ALL=(postgres) /usr/bin/psql
Windows RBAC with Active Directory
Windows Active Directory provides comprehensive RBAC through:
- Security Groups (roles)
- Group Policy Objects (permissions)
- Organizational Units (resource containers)
Best Practices for RBAC Implementation
Principle of Least Privilege
Grant users the minimum permissions necessary to perform their job functions:
Role Design Guidelines
- Keep roles simple: Avoid overly complex role hierarchies
- Use descriptive names: Role names should clearly indicate their purpose
- Regular audits: Periodically review role assignments and permissions
- Separation of duties: Implement controls to prevent conflicts of interest
Security Considerations
class SecureRBACSystem(RBACSystem):
def __init__(self):
super().__init__()
self.session_timeout = 3600 # 1 hour
self.max_failed_attempts = 3
self.audit_log = []
def authenticate_and_authorize(self, user_id, password, resource, action):
"""Secure authentication and authorization"""
# Authenticate user
if not self.authenticate_user(user_id, password):
self.log_audit_event(user_id, "AUTH_FAILED", resource, action)
return False
# Check session validity
if not self.is_session_valid(user_id):
self.log_audit_event(user_id, "SESSION_EXPIRED", resource, action)
return False
# Check permissions
if self.check_permission(user_id, resource, action):
self.log_audit_event(user_id, "ACCESS_GRANTED", resource, action)
return True
else:
self.log_audit_event(user_id, "ACCESS_DENIED", resource, action)
return False
def log_audit_event(self, user_id, event_type, resource, action):
"""Log security events for auditing"""
import datetime
self.audit_log.append({
'timestamp': datetime.datetime.now(),
'user_id': user_id,
'event_type': event_type,
'resource': resource,
'action': action
})
Common RBAC Challenges and Solutions
Role Explosion
Problem: Too many granular roles making management complex
Solution: Use role composition and inheritance patterns
Permission Creep
Problem: Users accumulating unnecessary permissions over time
Solution: Implement regular access reviews and automated cleanup
Cross-System Integration
Problem: Maintaining consistent roles across multiple systems
Solution: Centralized identity and access management (IAM)
Monitoring and Auditing
Effective RBAC implementation requires continuous monitoring:
def generate_access_report():
"""Generate comprehensive access report"""
report = {
'total_users': len(rbac.users),
'total_roles': len(rbac.roles),
'total_permissions': len(rbac.permissions),
'role_assignments': {},
'orphaned_users': [],
'unused_roles': []
}
# Analyze role assignments
for user_id, roles in rbac.user_roles.items():
username = rbac.users[user_id]['username']
report['role_assignments'][username] = [
rbac.roles[role_id]['name'] for role_id in roles
]
if not roles:
report['orphaned_users'].append(username)
# Find unused roles
assigned_roles = set()
for roles in rbac.user_roles.values():
assigned_roles.update(roles)
for role_id, role_data in rbac.roles.items():
if role_id not in assigned_roles:
report['unused_roles'].append(role_data['name'])
return report
Future of RBAC
Modern RBAC implementations are evolving to include:
- Attribute-Based Access Control (ABAC): More dynamic, context-aware permissions
- Zero Trust Architecture: Continuous verification and least-privilege access
- AI-Powered Access Management: Machine learning for anomaly detection and automated role suggestions
- Cloud-Native RBAC: Kubernetes RBAC, AWS IAM, and Azure AD integration
Conclusion
Role-based Access Control provides a robust foundation for managing system security at scale. By implementing RBAC correctly with proper role design, regular auditing, and security best practices, organizations can achieve both strong security posture and administrative efficiency.
The key to successful RBAC implementation lies in understanding your organization’s structure, designing roles that reflect real job functions, and maintaining the system through regular reviews and updates. As systems continue to evolve toward cloud and microservices architectures, RBAC remains a fundamental component of comprehensive security strategies.
- Introduction to Role-based Access Control (RBAC)
- Core RBAC Components
- RBAC Models and Levels
- RBAC Implementation Architecture
- Implementation Steps
- Database Schema Design
- Programming Implementation Examples
- RBAC in Operating Systems
- Best Practices for RBAC Implementation
- Common RBAC Challenges and Solutions
- Monitoring and Auditing
- Future of RBAC
- Conclusion