In today’s interconnected world, securing your data is paramount. MySQL databases, storing critical information for countless applications, are prime targets for malicious actors. Just like a bank vault protects your valuables, MySQL security measures shield your data from unauthorized access and manipulation. Did you know? 💡 Cyberattacks on databases are increasing by 15% annually, making robust security practices essential for everyone!
Why is MySQL Security Important?
Before we dive deep into the technical aspects, let’s understand why MySQL security is so crucial:
🔒 Key Reasons:
- Data Confidentiality: Protecting sensitive information from unauthorized viewing.
- Data Integrity: Ensuring that your data remains accurate and unaltered.
- System Availability: Preventing denial-of-service attacks and ensuring uninterrupted access for authorized users.
- Compliance: Meeting regulatory requirements for data protection (e.g., GDPR, HIPAA).
- Reputation: Maintaining user trust by safeguarding their personal and financial data.
🎯 Fun Fact: A single data breach can cost an organization millions of dollars and irreparably damage its reputation. Implementing proactive security measures is always more cost-effective than recovering from a breach!
Pillars of MySQL Security
MySQL security rests on three fundamental pillars:
- Authentication: Verifying the identity of users attempting to connect to the database.
- Authorization: Determining what actions authenticated users are permitted to perform within the database.
- Encryption: Protecting data both in transit and at rest using cryptographic techniques.
Let’s examine each pillar in detail:
1. Authentication: Verifying User Identity
Authentication is the first line of defense against unauthorized access. Just like a password to your email, MySQL requires credentials to verify user identity:
MySQL uses a combination of usernames and passwords for authentication. However, it’s crucial to manage these credentials carefully:
- Strong Passwords: Use a mix of uppercase and lowercase letters, numbers, and special characters.
- Password Rotation: Regularly change passwords to minimize the risk of compromise.
- Secure Storage: Never store passwords in plain text; use secure hashing algorithms instead.
⚙️ Pro Tip: Avoid using default usernames like “root” in production environments. Create specific users with limited privileges for everyday tasks.
2. Authorization: Controlling Access to Data
Once a user is authenticated, authorization defines what they can do within the database. MySQL uses a robust privilege system to manage access control:
- Granting Privileges: Assigning permissions to users to perform specific actions (e.g., SELECT, INSERT, UPDATE, DELETE).
- Revoking Privileges: Removing previously granted permissions when they are no longer needed.
- Least Privilege Principle: Granting only the necessary privileges required for a user to perform their role.
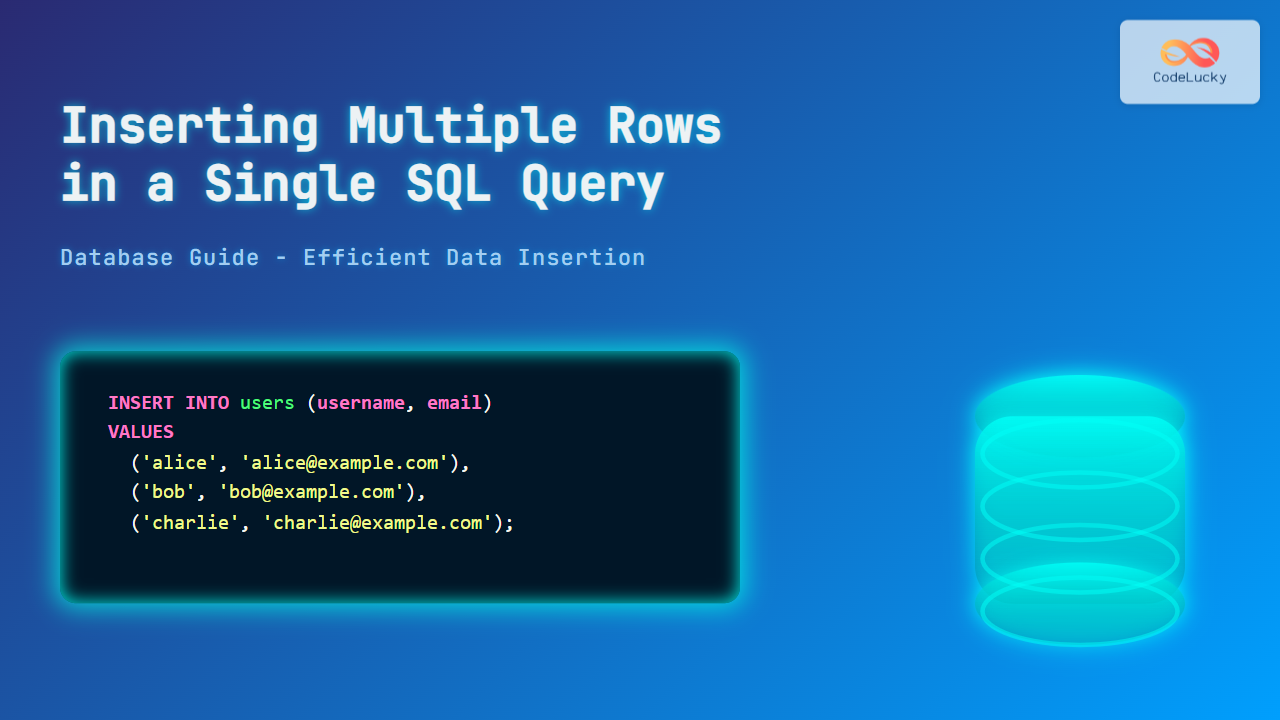
-- Example: Grant SELECT privilege to 'user1' on 'mytable'
GRANT SELECT ON mydatabase.mytable TO 'user1'@'localhost';
-- Example: Revoke UPDATE privilege from 'user2' on 'mytable'
REVOKE UPDATE ON mydatabase.mytable FROM 'user2'@'localhost';
🔍 Fun Fact: MySQL’s privilege system is based on granular access control, meaning that different users can have different permissions on the same table!
3. Encryption: Protecting Data in Transit and at Rest
Encryption is essential for safeguarding your data, both during transfer over the network and when it’s stored on disk:
- Data in Transit (SSL/TLS): Encrypting the communication channel between the client and the server, protecting data from eavesdropping.
- Data at Rest: Encrypting the database files on the server’s disk to protect data from unauthorized physical access.
SSL/TLS encryption ensures that even if someone intercepts the network traffic, they won’t be able to decipher the data. Data at rest encryption protects against physical theft of hard drives.
🛡️ Pro Tip: Always use SSL/TLS to encrypt your connection and configure your storage for encryption.
Security Best Practices: A Comprehensive Approach
Implementing robust security requires a multi-faceted approach:
- Keep MySQL Updated: Regularly update MySQL to patch vulnerabilities.
- Secure Your Server: Harden the operating system and network configuration of your database server.
- Firewall: Implement a firewall to restrict access to your MySQL server from specific IP addresses.
- Audit Logging: Enable audit logging to track user activities and identify suspicious behavior.
- Regular Backups: Perform regular backups of your database and store them in a secure location.
- Limit Exposure: Minimize the number of access points to your database server.
- User Management: Regularly review user accounts and revoke unnecessary privileges.
Common Pitfalls and How to Avoid Them
- Default Credentials: Never use default usernames and passwords for production databases.
- Weak Passwords: Always use strong and unique passwords.
- Excessive Privileges: Grant users only the minimum privileges necessary.
- Unencrypted Connections: Always use SSL/TLS to encrypt your database connections.
- Ignoring Updates: Regularly update your MySQL server to patch security vulnerabilities.
Real-World Examples
- Securing a Web Application: Configure your web application to use a dedicated MySQL user with limited privileges, preventing direct access to the database from the public.
- Protecting Financial Data: Encrypt sensitive financial data both in transit and at rest, ensuring compliance with industry regulations.
- Auditing User Activity: Enable audit logging to track user activities and detect suspicious behavior, protecting against internal threats.
Key Takeaways
In this guide, you’ve learned:
- 🔑 The importance of MySQL security
- 👤 The three pillars of security: Authentication, Authorization, and Encryption
- 🔒 Best practices to secure your MySQL database
- 🛡️ Common pitfalls and how to avoid them
- 💡 Real-world examples of security practices
What’s Next?
Now that you have a strong grasp of MySQL security fundamentals, you can explore these related topics:
- MySQL Users: Dive deeper into user creation and management.
- MySQL Privileges: Learn how to effectively manage granular access control.
- MySQL SSL Configuration: Implement SSL/TLS for secure connections.
- MySQL Encryption: Explore data at rest encryption techniques.
Remember, security is an ongoing process, not a one-time task. By following these best practices, you can significantly enhance the security of your MySQL databases and protect your valuable data.
🚀 Final Fact: Robust security measures can prevent up to 90% of common database attacks. Prioritize these strategies to ensure your data’s safety.