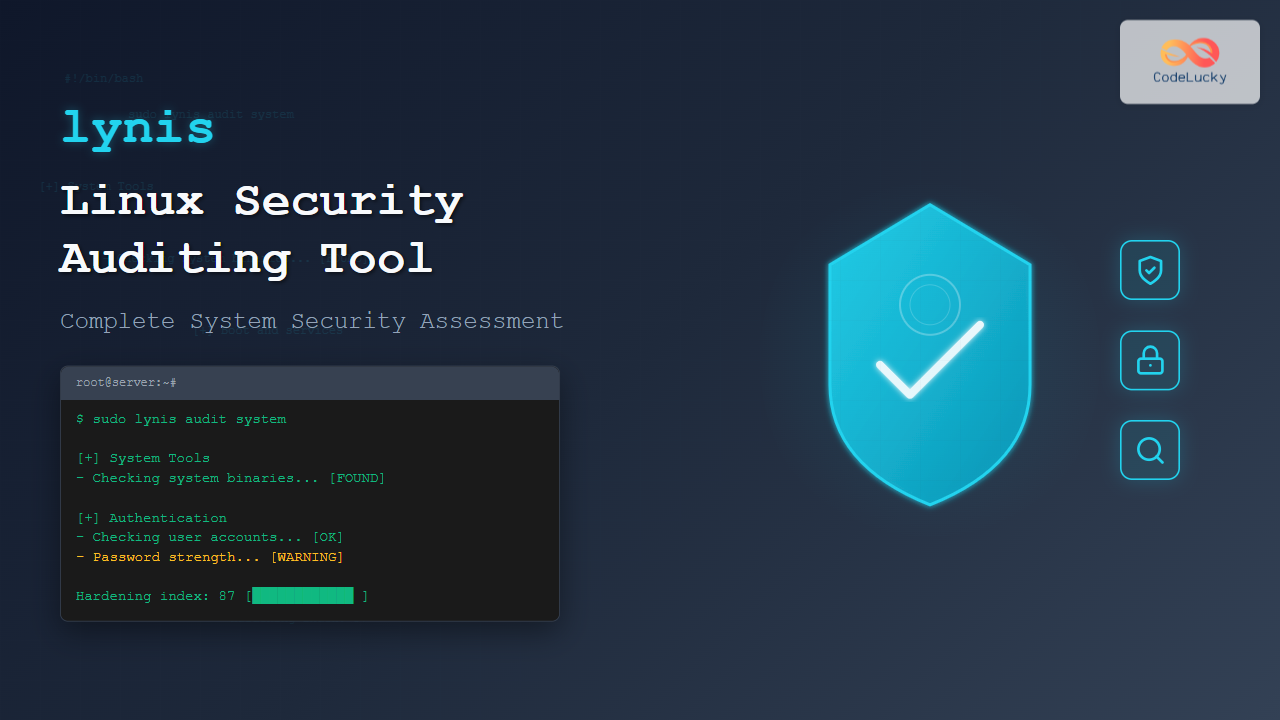
The lynis command is a powerful, open-source security auditing tool designed specifically for Unix-based systems including Linux, macOS, and BSD. This comprehensive security scanner helps system administrators identify vulnerabilities, misconfigurations, and compliance issues within their systems.
What is Lynis?
Lynis performs over 250 security tests to assess your system’s security posture. It examines various aspects of your system including:
- System configuration and hardening
- Network security settings
- File permissions and access controls
- Running services and processes
- Installed software and updates
- Compliance with security standards
Installing Lynis on Linux
Ubuntu/Debian Installation
# Update package list
sudo apt update
# Install lynis
sudo apt install lynis
# Verify installation
lynis --versionCentOS/RHEL/Fedora Installation
# For CentOS/RHEL (enable EPEL repository first)
sudo yum install epel-release
sudo yum install lynis
# For Fedora
sudo dnf install lynisInstalling from Source
# Download latest version
wget https://downloads.cisofy.com/lynis/lynis-3.0.8.tar.gz
# Extract archive
tar -xzf lynis-3.0.8.tar.gz
# Navigate to directory
cd lynis
# Run lynis directly
sudo ./lynis audit systemBasic Lynis Commands and Usage
System Audit
The most common use case is performing a complete system audit:
sudo lynis audit systemSample Output:
[ Lynis 3.0.8 ]
################################################################################
Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are
welcome to redistribute it under the terms of the GNU General Public License.
See the LICENSE file for details about using this software.
2025 Copyright, CISOfy - https://cisofy.com/lynis/
Enterprise support available (compliance, plugins, interface and tools)
################################################################################
[+] Initializing program
------------------------------------
- Detecting OS... [ DONE ]
- Checking profiles... [ DONE ]
---------------------------------------------------
Program version: 3.0.8
Operating system: Linux
Operating system name: Ubuntu Linux
Operating system version: 22.04
Kernel version: 5.15.0
Hardware platform: x86_64
Hostname: ubuntu-server
---------------------------------------------------Quick Audit
For a faster scan with essential checks only:
sudo lynis audit system --quickSpecific Category Audits
Target specific areas of your system:
# Audit only authentication
sudo lynis audit system --tests-from-group authentication
# Audit only networking
sudo lynis audit system --tests-from-group networking
# Audit only file systems
sudo lynis audit system --tests-from-group filesystemsUnderstanding Lynis Output
Test Results Format
Lynis displays results with clear indicators:
[+] Boot and services
------------------------------------
- Service Manager [ systemd ]
- Checking UEFI boot [ DISABLED ]
- Checking presence GRUB2 [ FOUND ]
- Checking presence GRUB2 password [ WARNING ]
- Check running services (systemctl) [ DONE ]
Result: found 23 running services
- Check enabled services at boot (systemctl) [ DONE ]
Result: found 34 enabled servicesStatus Indicators
- [OK] – Test passed successfully
- [DONE] – Test completed
- [WARNING] – Potential security issue found
- [SUGGESTION] – Improvement recommendation
- [SKIPPED] – Test not applicable
Advanced Lynis Features
Custom Profiles
Create custom audit profiles for specific requirements:
# Create custom profile
sudo nano /etc/lynis/custom.prf
# Example profile content:
# Skip certain tests
skip-test=BOOT-5122
skip-test=NETW-3001
# Enable specific plugins
plugin=compliance
plugin=forensics
# Set compliance standards
compliance-standards=cis,pci-dssUse the custom profile:
sudo lynis audit system --profile /etc/lynis/custom.prfGenerating Reports
Create detailed reports in various formats:
# Generate report with specific name
sudo lynis audit system --report-file /tmp/security-audit-$(date +%Y%m%d)
# View the generated report
cat /var/log/lynis-report.datCompliance Checking
Check compliance with security standards:
# Check CIS compliance
sudo lynis audit system --compliance cis
# Check PCI-DSS compliance
sudo lynis audit system --compliance pci-dss
# Multiple standards
sudo lynis audit system --compliance "cis,pci-dss,iso27001"Interpreting Security Findings
Common Warning Examples
SSH Configuration Warning:
[+] SSH Support
------------------------------------
- Checking running SSH daemon [ FOUND ]
- Checking SSH configuration [ FOUND ]
- SSH option: AllowTcpForwarding [ WARNING ]
- SSH option: ClientAliveCountMax [ OK ]
- SSH option: Compression [ WARNING ]
- SSH option: FingerprintHash [ OK ]
- SSH option: GatewayPorts [ OK ]
- SSH option: IgnoreRhosts [ OK ]File Permissions Warning:
[+] File systems
------------------------------------
- Checking mount points [ DONE ]
- Query system volume group (LVM) [ FOUND ]
- Checking LVM volume groups [ FOUND ]
- Checking Locate database [ FOUND ]
- Checking /tmp, /var/tmp, and /dev/shm [ WARNING ]
- /tmp is not mounted with noexec optionAddressing Findings
For each warning, Lynis provides suggestions. Example fixes:
# Fix SSH AllowTcpForwarding
sudo nano /etc/ssh/sshd_config
# Add: AllowTcpForwarding no
sudo systemctl restart sshd
# Fix /tmp mount with noexec
sudo mount -o remount,noexec /tmp
# Make permanent in /etc/fstab
# Add noexec to /tmp mount optionsAutomated Security Monitoring
Scheduling Regular Audits
Set up automated security scans using cron:
# Edit crontab
sudo crontab -e
# Add weekly security audit (every Sunday at 2 AM)
0 2 * * 0 /usr/bin/lynis audit system --cronjob --quiet --report-file /var/log/lynis/weekly-audit-$(date +\%Y\%m\%d) 2>&1
# Add monthly compliance check
0 3 1 * * /usr/bin/lynis audit system --cronjob --compliance cis --report-file /var/log/lynis/monthly-compliance-$(date +\%Y\%m\%d) 2>&1Email Notifications
Create a script to send audit results via email:
#!/bin/bash
# lynis-audit-notify.sh
REPORT_FILE="/var/log/lynis-report-$(date +%Y%m%d).dat"
EMAIL="[email protected]"
# Run lynis audit
/usr/bin/lynis audit system --report-file "$REPORT_FILE" --quiet
# Extract summary
WARNINGS=$(grep "warnings\[\]=" "$REPORT_FILE" | wc -l)
SUGGESTIONS=$(grep "suggestion\[\]=" "$REPORT_FILE" | wc -l)
# Send email notification
echo "Lynis Security Audit Summary
Date: $(date)
Warnings Found: $WARNINGS
Suggestions: $SUGGESTIONS
Full report available at: $REPORT_FILE" | mail -s "Security Audit Report - $(hostname)" "$EMAIL"Lynis Configuration Files
Main Configuration
The primary configuration file location:
# System-wide configuration
/etc/lynis/default.prf
# View current configuration
sudo lynis show settingsCustom Settings Example
# Custom Lynis configuration
# File: /etc/lynis/custom.prf
# Skip specific tests that don't apply
skip-test=FIRE-4508
skip-test=MAIL-8818
# Set custom log directory
logdir=/var/log/lynis/
# Enable specific plugins
plugin=malware
plugin=compliance
# Set warning level
warning-level=3
# Define custom checks
custom-url-1=http://example.com/custom-rules.datIntegration with Other Tools
SIEM Integration
Parse Lynis output for SIEM systems:
# Export findings in structured format
sudo lynis audit system --no-colors --quiet | grep -E "(WARNING|SUGGESTION)" > /tmp/lynis-findings.txt
# Convert to JSON format
awk -F'[][]' '{print "{\"timestamp\":\"" strftime("%Y-%m-%d %H:%M:%S") "\",\"level\":\"" $2 "\",\"message\":\"" $0 "\"}"}' /tmp/lynis-findings.txtAnsible Playbook Integration
---
- name: Run Lynis Security Audit
hosts: all
become: yes
tasks:
- name: Install Lynis
package:
name: lynis
state: present
- name: Run Lynis audit
command: lynis audit system --cronjob --quiet
register: lynis_result
- name: Create audit report directory
file:
path: /var/log/lynis-reports
state: directory
mode: '0755'
- name: Copy Lynis report
copy:
src: /var/log/lynis-report.dat
dest: "/var/log/lynis-reports/{{ inventory_hostname }}-{{ ansible_date_time.date }}.dat"
remote_src: yesTroubleshooting Common Issues
Permission Errors
Always run Lynis with appropriate permissions:
# Incorrect - limited access
lynis audit system
# Correct - full system access
sudo lynis audit systemIncomplete Scans
If scans terminate unexpectedly:
# Check system resources
df -h
free -m
# Run with debug mode
sudo lynis audit system --debug
# Check for conflicting processes
ps aux | grep lynisPlugin Issues
Troubleshoot plugin problems:
# List available plugins
lynis show plugins
# Test specific plugin
sudo lynis audit system --plugin malware --debug
# Check plugin directory
ls -la /usr/share/lynis/plugins/Best Practices for Using Lynis
Regular Audit Schedule
- Daily: Quick scans on critical systems
- Weekly: Full system audits
- Monthly: Comprehensive compliance checks
- Quarterly: Review and update custom profiles
Results Management
# Organize reports by date
mkdir -p /var/log/lynis/{daily,weekly,monthly}
# Archive old reports
find /var/log/lynis/ -name "*.dat" -mtime +90 -exec gzip {} \;Security Considerations
- Store audit reports securely with restricted permissions
- Regularly update Lynis to the latest version
- Review and validate all findings before implementing fixes
- Document remediation actions for audit trails
Conclusion
The lynis command is an invaluable tool for Linux system administrators seeking to maintain robust security postures. By implementing regular security audits with Lynis, you can proactively identify vulnerabilities, ensure compliance with security standards, and maintain hardened systems.
Remember that Lynis is a diagnostic tool – it identifies potential issues but requires human judgment to determine appropriate remediation actions. Always test security changes in non-production environments before applying them to critical systems.
Start with basic system audits, gradually implement automated scanning schedules, and customize profiles to match your specific security requirements. This systematic approach will help you build a comprehensive security monitoring strategy using Lynis.