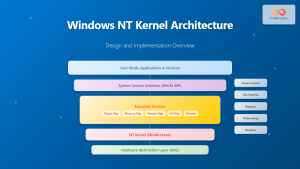
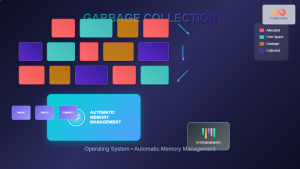
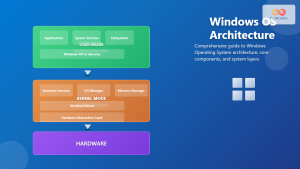
The kernel stands as the fundamental cornerstone of any operating system, serving as the critical bridge between hardware components and software applications. This essential system component manages every aspect of computer operations, from memory allocation to process scheduling, making it indispensable for modern computing environments.
What is an Operating System Kernel?
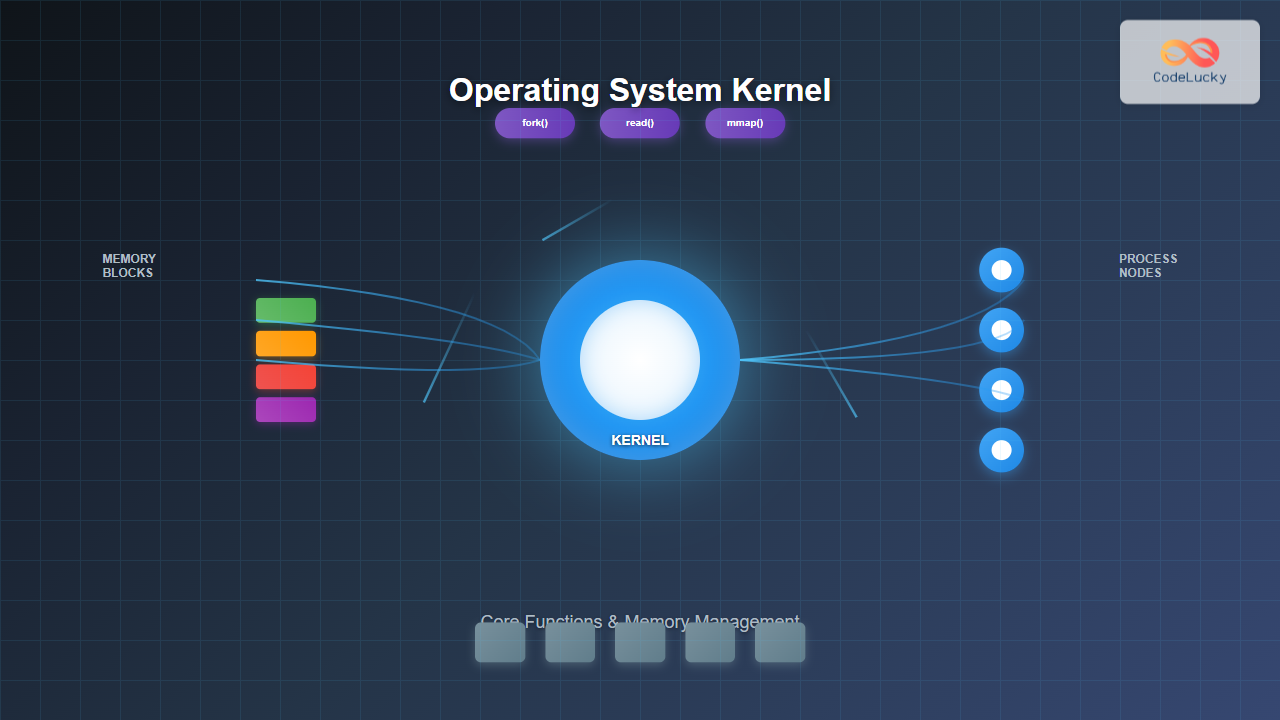
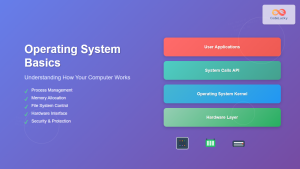
The kernel is the core component of an operating system that maintains complete control over system resources and hardware interactions. It operates at the highest privilege level, managing critical system functions that applications cannot directly access for security and stability reasons.
Unlike user applications that run in user space with limited privileges, the kernel operates in kernel space with unrestricted access to system hardware and memory. This separation ensures system integrity while providing controlled access to resources through well-defined interfaces.
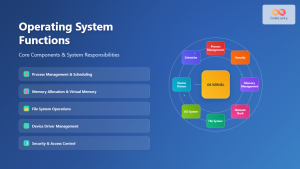
Core Functions of the Operating System Kernel
Process Management and Scheduling
The kernel’s process management capabilities handle the creation, execution, and termination of processes. It maintains process control blocks (PCBs) containing essential information about each running process, including process ID, memory allocation, and execution state.
Process scheduling algorithms determine which process receives CPU time and for how long. Common scheduling algorithms include:
- Round Robin: Each process receives equal time slices
- Priority Scheduling: Higher priority processes execute first
- Shortest Job First: Processes with shorter execution times run first
- Multilevel Queue: Different queues for different process types
Example: Process State Transitions
// Process states in Linux kernel
typedef enum {
TASK_RUNNING, // Process is runnable
TASK_INTERRUPTIBLE, // Process is sleeping, can be woken by signals
TASK_UNINTERRUPTIBLE,// Process is sleeping, cannot be interrupted
TASK_STOPPED, // Process execution stopped
TASK_ZOMBIE // Process terminated but not cleaned up
} process_state_t;
Memory Management Architecture
Memory management represents one of the kernel’s most critical responsibilities. The kernel implements sophisticated virtual memory systems that provide each process with its own virtual address space while efficiently managing physical RAM.
Virtual Memory Implementation
Virtual memory creates an abstraction layer between logical addresses used by programs and physical memory addresses. This system provides several advantages:
- Process Isolation: Each process operates in its own address space
- Memory Protection: Prevents processes from accessing unauthorized memory
- Efficient Memory Usage: Allows overcommitment of memory resources
- Simplified Programming: Provides consistent memory layout for applications
Page Table Management
The kernel maintains page tables that map virtual addresses to physical addresses. Modern systems use multi-level page tables to efficiently handle large address spaces:
// Simplified page table entry structure
struct page_table_entry {
unsigned long pfn:40; // Physical Frame Number
unsigned int present:1; // Page is in physical memory
unsigned int writable:1; // Page can be written to
unsigned int user:1; // Page accessible from user mode
unsigned int accessed:1; // Page has been accessed
unsigned int dirty:1; // Page has been modified
};
System Call Interface
The kernel exposes its functionality through system calls, which provide a controlled interface for user applications to access kernel services. System calls ensure security by validating parameters and maintaining privilege separation.
Common System Call Categories
| Category | Examples | Purpose |
|---|---|---|
| Process Control | fork(), exec(), exit() | Process creation and management |
| File Operations | open(), read(), write(), close() | File system interactions |
| Device Management | ioctl(), mmap() | Hardware device control |
| Information Maintenance | getpid(), alarm(), sleep() | System information and timing |
System Call Execution Example
// C program demonstrating system calls
#include <sys/types.h>
#include <unistd.h>
#include <stdio.h>
int main() {
pid_t pid;
// System call to create new process
pid = fork();
if (pid == 0) {
// Child process
printf("Child process ID: %d\n", getpid());
// System call to replace process image
execl("/bin/echo", "echo", "Hello from child!", NULL);
} else if (pid > 0) {
// Parent process
printf("Parent process ID: %d\n", getpid());
printf("Created child with PID: %d\n", pid);
}
return 0;
}
Memory Management Techniques
Paging and Segmentation
Paging divides both virtual and physical memory into fixed-size blocks called pages and frames respectively. This approach simplifies memory allocation and reduces external fragmentation.
Page Replacement Algorithms
When physical memory becomes full, the kernel must decide which pages to swap to storage. Common algorithms include:
- Least Recently Used (LRU): Removes pages that haven’t been accessed recently
- First-In-First-Out (FIFO): Removes the oldest pages first
- Clock Algorithm: Approximates LRU with lower overhead
- Working Set: Maintains pages actively used by processes
Memory Allocation Strategies
The kernel employs various allocation strategies to manage memory efficiently:
Buddy System Algorithm
The buddy system manages free memory blocks by pairing blocks of equal size. When a block is freed, the kernel checks if its “buddy” is also free and merges them into a larger block.
// Buddy system allocation example
struct buddy_block {
size_t size; // Block size (power of 2)
int is_free; // Free status
struct buddy_block *next;
};
// Allocate memory block
void* buddy_alloc(size_t size) {
// Find smallest power-of-2 block >= size
size_t block_size = next_power_of_2(size);
// Search for free block of appropriate size
struct buddy_block *block = find_free_block(block_size);
if (!block) {
// Split larger block if available
block = split_block(block_size);
}
return block ? mark_allocated(block) : NULL;
}
Memory Protection Mechanisms
Modern kernels implement multiple layers of memory protection to ensure system security and stability:
Hardware-Assisted Protection
- Memory Management Unit (MMU): Hardware component that translates virtual addresses
- Translation Lookaside Buffer (TLB): Cache for recent address translations
- Control Registers: Hardware registers controlling memory access permissions
Software Protection Features
// Memory protection flags in Linux
#define PROT_READ 0x1 // Page can be read
#define PROT_WRITE 0x2 // Page can be written
#define PROT_EXEC 0x4 // Page can be executed
#define PROT_NONE 0x0 // Page cannot be accessed
// mmap() system call with protection
void *addr = mmap(NULL, 4096,
PROT_READ | PROT_WRITE,
MAP_PRIVATE | MAP_ANONYMOUS,
-1, 0);
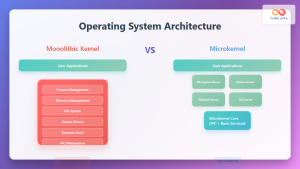
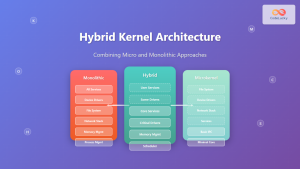
Kernel Types and Architecture
Monolithic Kernels
Monolithic kernels implement all system services within a single kernel space. This design provides excellent performance but reduces modularity and fault isolation.
Advantages of Monolithic Design
- High Performance: Direct function calls between components
- Efficient Resource Sharing: Components share kernel memory space
- Simplified Development: Single codebase and compilation unit
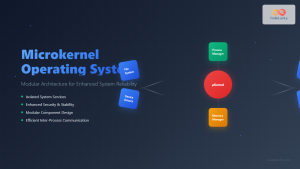
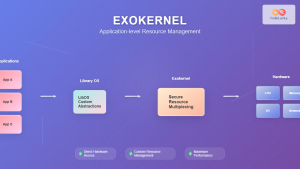
Microkernel Architecture
Microkernels implement only essential functions in kernel space, moving other services to user space as separate processes. This approach enhances reliability and security at the cost of performance.
Microkernel Components
| Component | Location | Responsibility |
|---|---|---|
| Process Scheduler | Kernel Space | CPU scheduling and context switching |
| Memory Manager | Kernel Space | Virtual memory and address translation |
| File System | User Space | File operations and storage management |
| Device Drivers | User Space | Hardware device management |
Kernel Performance Optimization
Context Switching Optimization
Context switching overhead significantly impacts system performance. Modern kernels employ various optimization techniques:
Lazy Context Switching
// Optimized context switch implementation
void optimized_context_switch(struct task_struct *prev,
struct task_struct *next) {
// Save only modified registers
if (prev->flags & TASK_FPU_USED) {
save_fpu_state(&prev->fpu_state);
}
// Load minimal required state
load_cpu_state(&next->cpu_state);
// Lazy TLB flushing - flush only when necessary
if (prev->mm != next->mm) {
switch_page_directory(next->mm->pgd);
}
}
Memory Management Optimization
Copy-on-Write (COW)
The copy-on-write mechanism optimizes memory usage by sharing pages between processes until modification occurs:
// Copy-on-write page fault handler
int cow_page_fault(struct vm_area_struct *vma,
unsigned long address) {
struct page *old_page, *new_page;
// Get the shared page
old_page = get_page(address);
if (page_count(old_page) == 1) {
// Only reference, make writable
set_page_writable(old_page);
return 0;
}
// Multiple references, copy page
new_page = alloc_page(GFP_KERNEL);
copy_page_data(old_page, new_page);
// Update page table
update_page_table(vma, address, new_page);
put_page(old_page);
return 0;
}
Modern Kernel Features
Real-Time Capabilities
Modern kernels incorporate real-time features to support time-critical applications with deterministic response times:
- Priority Inheritance: Prevents priority inversion problems
- Preemptible Kernel: Allows high-priority tasks to interrupt kernel operations
- High-Resolution Timers: Provides microsecond-level timing accuracy
Security Enhancements
Address Space Layout Randomization (ASLR)
ASLR randomizes memory layout to prevent exploitation of memory corruption vulnerabilities:
// ASLR implementation example
unsigned long get_random_base(unsigned long base,
unsigned long range) {
unsigned long random_offset;
// Generate cryptographically secure random offset
get_random_bytes(&random_offset, sizeof(random_offset));
// Align to page boundaries
random_offset &= PAGE_MASK;
random_offset %= range;
return base + random_offset;
}
Troubleshooting Kernel Issues
Kernel Debugging Techniques
Effective kernel debugging requires specialized tools and techniques:
Kernel Log Analysis
# View kernel messages
dmesg | tail -20
# Monitor kernel logs in real-time
tail -f /var/log/kern.log
# Check for memory issues
grep -i "out of memory\|killed process" /var/log/messages
Performance Monitoring
# Monitor system calls
strace -c -p <pid>
# Analyze memory usage
cat /proc/meminfo
cat /proc/<pid>/status
# Check kernel statistics
cat /proc/stat
vmstat 1
Conclusion
The operating system kernel serves as the fundamental foundation enabling modern computing systems. Its sophisticated memory management, process scheduling, and resource allocation capabilities provide the stable platform upon which all software applications depend. Understanding kernel architecture and functionality proves essential for system administrators, developers, and anyone working with computer systems at a deep level.
Modern kernels continue evolving to address emerging challenges in security, performance, and hardware compatibility. As computing environments become increasingly complex with cloud platforms, containerization, and distributed systems, the kernel’s role in providing efficient abstraction and resource management becomes even more critical for system reliability and performance.