The iwlist command is a powerful Linux utility that allows users to scan and display detailed information about wireless networks in their vicinity. Whether you’re troubleshooting connectivity issues, monitoring network performance, or simply exploring available WiFi networks, iwlist provides comprehensive wireless network analysis capabilities.
What is the iwlist Command?
iwlist is part of the wireless-tools package in Linux systems, designed to display various types of information from wireless network interfaces. It can scan for available access points, show encryption details, display signal strength, and provide channel information for wireless networks.
The command is particularly useful for network administrators, security professionals, and users who need to analyze wireless network environments or troubleshoot connectivity problems.
Installing iwlist
Most Linux distributions include iwlist by default, but if it’s not available, you can install it using your package manager:
Ubuntu/Debian:
sudo apt update
sudo apt install wireless-toolsCentOS/RHEL/Fedora:
sudo yum install wireless-tools
# or for newer versions
sudo dnf install wireless-toolsArch Linux:
sudo pacman -S wireless_toolsBasic Syntax and Options
The basic syntax of the iwlist command is:
iwlist [interface] [scanning_type] [options]Common Options:
scan– Scan for wireless access pointsfreq– List available frequencieschannel– List available channelsrate– List available bit rateskeys– List encryption keyspower– List power management settingstxpower– List transmit power settings
Scanning for Wireless Networks
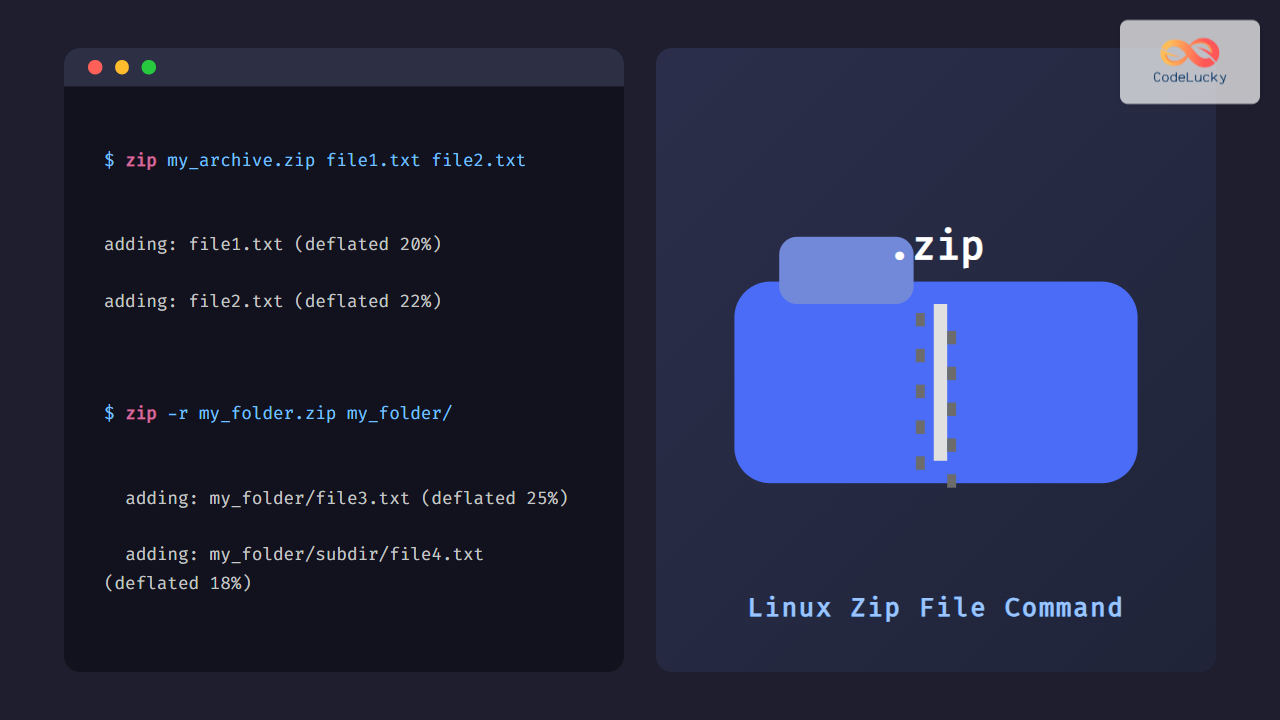
The most common use of iwlist is to scan for available wireless networks. Here’s how to perform a basic scan:
sudo iwlist wlan0 scanThis command will produce output similar to:
wlan0 Scan completed :
Cell 01 - Address: 00:1A:2B:3C:4D:5E
ESSID:"MyHomeNetwork"
Mode:Master
Frequency:2.437 GHz (Channel 6)
Quality=70/70 Signal level=-40 dBm
Encryption key:on
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s
9 Mb/s; 12 Mb/s; 18 Mb/s
Bit Rates:24 Mb/s; 36 Mb/s; 48 Mb/s; 54 Mb/s
Extra:tsf=0000000000000000
Extra:Last beacon=100ms ago
IE: Unknown: 0D4D79486F6D654E6574776F726B
IE: IEEE 802.11i/WPA2 Version 1
Group Cipher : CCMP
Pairwise Ciphers (1) : CCMP
Authentication Suites (1) : PSK
Cell 02 - Address: 11:22:33:44:55:66
ESSID:"GuestNetwork"
Mode:Master
Frequency:2.462 GHz (Channel 11)
Quality=45/70 Signal level=-65 dBm
Encryption key:off
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/sUnderstanding Scan Results
Each wireless network in the scan results contains several important pieces of information:
Key Fields Explained:
- Cell – Sequential number for each detected network
- Address – MAC address of the access point
- ESSID – Network name (Service Set Identifier)
- Mode – Operating mode (usually Master for access points)
- Frequency/Channel – Operating frequency and channel number
- Quality – Signal quality measurement
- Signal level – Signal strength in dBm
- Encryption key – Whether the network is secured
- Bit Rates – Supported data transmission rates
Filtering and Sorting Scan Results
You can combine iwlist with other Linux commands to filter and sort results. Here are some practical examples:
Show Only Network Names (ESSID):
sudo iwlist wlan0 scan | grep ESSIDOutput:
ESSID:"MyHomeNetwork"
ESSID:"GuestNetwork"
ESSID:"NeighborWiFi"Show Signal Strength Information:
sudo iwlist wlan0 scan | grep -E "(ESSID|Signal level)"Output:
ESSID:"MyHomeNetwork"
Quality=70/70 Signal level=-40 dBm
ESSID:"GuestNetwork"
Quality=45/70 Signal level=-65 dBmSort Networks by Signal Strength:
sudo iwlist wlan0 scan | awk '/Cell|ESSID|Signal/ {print}' | paste - - - | sort -k6 -nrAdvanced Scanning Techniques
Scanning Specific Channels:
You can scan specific channels to focus on particular frequency ranges:
sudo iwlist wlan0 scan freq 2.437GGetting Encryption Information:
sudo iwlist wlan0 scan | grep -A5 -B5 "Encryption key:on"Monitoring Signal Strength Over Time:
watch -n 5 "sudo iwlist wlan0 scan | grep -E '(ESSID|Signal level)'"Other iwlist Functions
List Available Channels:
iwlist wlan0 channelOutput:
wlan0 11 channels in total; available frequencies :
Channel 01 : 2.412 GHz
Channel 02 : 2.417 GHz
Channel 03 : 2.422 GHz
Channel 04 : 2.427 GHz
Channel 05 : 2.432 GHz
Channel 06 : 2.437 GHz
Channel 07 : 2.442 GHz
Channel 08 : 2.447 GHz
Channel 09 : 2.452 GHz
Channel 10 : 2.457 GHz
Channel 11 : 2.462 GHz
Current Frequency:2.437 GHz (Channel 6)Show Supported Bit Rates:
iwlist wlan0 rateDisplay Power Management Information:
iwlist wlan0 powerPractical Use Cases
1. Network Troubleshooting:
When experiencing connectivity issues, use iwlist to check if your network is visible and assess signal strength:
sudo iwlist wlan0 scan | grep -A10 "ESSID:\"YourNetworkName\""2. Security Assessment:
Identify unsecured networks in your area:
sudo iwlist wlan0 scan | grep -B5 -A5 "Encryption key:off"3. Channel Analysis:
Find the least congested channel for your own access point:
sudo iwlist wlan0 scan | grep Frequency | sort | uniq -c | sort -nr4. Signal Strength Monitoring:
Create a simple script to monitor your connection quality:
#!/bin/bash
while true; do
echo "$(date): Signal strength check"
sudo iwlist wlan0 scan | grep -A1 "ESSID:\"YourNetwork\"" | grep "Signal level"
sleep 30
doneCommon Issues and Troubleshooting
Permission Denied Error:
If you encounter permission errors, ensure you’re running the command with appropriate privileges:
sudo iwlist wlan0 scanInterface Not Found:
First, identify your wireless interface name:
ip link show
# or
iwconfigCommon interface names include wlan0, wlp3s0, or wlo1.
No Scan Results:
If no networks are found, try:
- Bringing the interface up:
sudo ip link set wlan0 up - Checking if the wireless card is enabled
- Verifying driver installation
Security Considerations
When using iwlist, keep these security aspects in mind:
- Passive Scanning:
iwlistperforms passive scanning, making it undetectable to access points - Privacy: The command reveals information about nearby networks but doesn’t compromise them
- Legal Usage: Use the tool responsibly and only on networks you own or have permission to analyze
Integration with Other Tools
iwlist works well with other Linux networking tools:
Combined with nmcli:
nmcli device wifi list
sudo iwlist wlan0 scan | grep ESSIDUsed with awk for parsing:
sudo iwlist wlan0 scan | awk '/Cell|ESSID|Quality|Encryption/ {print}'Creating Custom Scripts
Here’s a useful script that creates a formatted report of nearby networks:
#!/bin/bash
echo "Wireless Network Scan Report"
echo "============================"
echo "Timestamp: $(date)"
echo ""
sudo iwlist wlan0 scan | awk '
BEGIN {
print "Network Name\t\tChannel\tSignal\tSecurity"
print "============\t\t=======\t======\t========"
}
/Cell/ { cell = $1 }
/ESSID:/ {
gsub(/"/,"",$2);
gsub(/ESSID:/,"",$2);
essid = $2
}
/Frequency:/ {
match($0, /Channel ([0-9]+)/, arr);
channel = arr[1]
}
/Signal level/ {
match($0, /Signal level=([^[:space:]]+)/, arr);
signal = arr[1]
}
/Encryption key:/ {
if ($3 == "on") security = "Secured";
else security = "Open";
printf "%-20s\t%s\t%s\t%s\n", essid, channel, signal, security
}
'Conclusion
The iwlist command is an essential tool for wireless network analysis in Linux environments. From basic network discovery to advanced troubleshooting scenarios, it provides comprehensive information about wireless networks in your vicinity. By mastering its various options and combining it with other Linux tools, you can effectively monitor, analyze, and troubleshoot wireless network environments.
Whether you’re a system administrator managing enterprise networks or a home user optimizing your WiFi setup, iwlist offers the detailed insights needed to make informed decisions about wireless connectivity. Regular use of this command can help maintain optimal network performance and identify potential security concerns in your wireless environment.
- What is the iwlist Command?
- Installing iwlist
- Basic Syntax and Options
- Scanning for Wireless Networks
- Understanding Scan Results
- Filtering and Sorting Scan Results
- Advanced Scanning Techniques
- Other iwlist Functions
- Practical Use Cases
- Common Issues and Troubleshooting
- Security Considerations
- Integration with Other Tools
- Creating Custom Scripts
- Conclusion