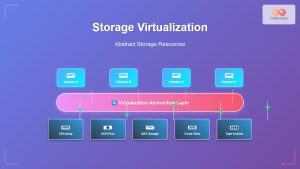
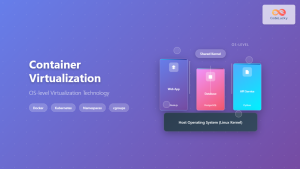
Introduction to Hardware-assisted Virtualization
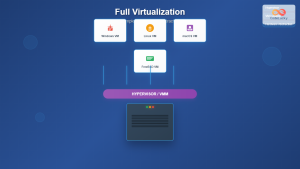
Hardware-assisted virtualization represents a revolutionary advancement in computing architecture, enabling efficient creation and management of virtual machines through dedicated processor features. Unlike traditional software-based virtualization that relies entirely on hypervisor software, hardware-assisted virtualization leverages specialized CPU instructions and memory management capabilities to dramatically improve performance and security.
The two dominant implementations are Intel VT-x (Virtualization Technology) and AMD-V (AMD Virtualization), both introduced in the mid-2000s to address the limitations of purely software-based virtualization solutions.
Understanding Virtualization Challenges
Traditional Software Virtualization Limitations
Before hardware assistance, virtualization faced significant technical hurdles:
- Privilege Level Conflicts: Guest operating systems expecting to run at Ring 0 (highest privilege) conflicted with hypervisor requirements
- Performance Overhead: Binary translation and trap-and-emulate techniques consumed substantial CPU cycles
- Memory Management Complexity: Shadow page tables created memory overhead and synchronization challenges
- I/O Virtualization Bottlenecks: Device emulation through software introduced significant latency
The Ring Compression Problem
Traditional x86 architecture uses four privilege rings (0-3), with Ring 0 providing complete system access. Virtualization created a fundamental problem: both hypervisor and guest OS needed Ring 0 access, leading to the famous “ring compression” issue.
Intel VT-x Architecture
Core Components
Intel VT-x introduces two fundamental operating modes:
- VMX Root Operation: Native execution mode for hypervisor
- VMX Non-Root Operation: Restricted execution mode for guest virtual machines
Virtual Machine Control Structure (VMCS)
The VMCS serves as the central data structure controlling VM behavior:
// VMCS Fields Example
struct vmcs_fields {
// Guest State Area
uint64_t guest_rip; // Guest instruction pointer
uint64_t guest_rsp; // Guest stack pointer
uint64_t guest_cr0; // Guest control register 0
uint64_t guest_cr3; // Guest page table base
// Host State Area
uint64_t host_rip; // Host resume point
uint64_t host_rsp; // Host stack pointer
// VM Execution Controls
uint32_t pin_controls; // Pin-based controls
uint32_t primary_controls; // Primary processor controls
uint32_t secondary_controls; // Secondary processor controls
// VM Exit Controls
uint32_t exit_controls; // VM exit behavior
uint64_t exit_msr_load; // MSRs to load on exit
};
VMX Instructions
Intel VT-x provides specific instructions for hypervisor operations:
| Instruction | Purpose | Description |
|---|---|---|
| VMXON | Enable VMX | Activates VMX operation mode |
| VMXOFF | Disable VMX | Deactivates VMX operation mode |
| VMLAUNCH | Start VM | Launches new virtual machine |
| VMRESUME | Resume VM | Resumes existing virtual machine |
| VMCALL | Hypercall | Guest to hypervisor communication |
| VMPTRLD | Load VMCS | Loads VMCS pointer |
| VMREAD | Read VMCS | Reads VMCS field value |
| VMWRITE | Write VMCS | Writes VMCS field value |
AMD-V (SVM) Architecture
Secure Virtual Machine Extensions
AMD-V, based on Secure Virtual Machine (SVM) technology, provides similar capabilities with different implementation approaches:
- Host Mode: Native execution for hypervisor
- Guest Mode: Virtualized execution for guest systems
Virtual Machine Control Block (VMCB)
AMD-V uses VMCB as the primary control structure:
// VMCB Structure Overview
struct vmcb {
// Control Area
struct {
uint32_t intercept_cr; // Control register intercepts
uint32_t intercept_dr; // Debug register intercepts
uint32_t intercept_exception; // Exception intercepts
uint64_t intercept_instruction; // Instruction intercepts
uint64_t msrpm_base; // MSR permission map
uint64_t iopm_base; // I/O permission map
} control;
// State Save Area
struct {
uint64_t rip; // Guest instruction pointer
uint64_t rsp; // Guest stack pointer
uint64_t cr0, cr2, cr3, cr4; // Control registers
uint64_t dr6, dr7; // Debug registers
} save_state;
};
SVM Instructions
AMD-V provides streamlined instruction set:
| Instruction | Purpose | Equivalent Intel |
|---|---|---|
| VMRUN | Enter guest mode | VMLAUNCH/VMRESUME |
| VMLOAD | Load guest state | Part of VMCS |
| VMSAVE | Save guest state | Part of VMCS |
| VMMCALL | Hypercall | VMCALL |
| SKINIT | Secure initialization | N/A |
Memory Virtualization
Extended Page Tables (EPT) – Intel
Intel’s EPT provides hardware-assisted memory virtualization by creating a second level of address translation:
EPT eliminates the need for shadow page tables, reducing memory overhead and improving performance:
// EPT Page Table Entry Structure
typedef union {
uint64_t value;
struct {
uint64_t read : 1; // Read permission
uint64_t write : 1; // Write permission
uint64_t execute : 1; // Execute permission
uint64_t memory_type : 3; // Memory type
uint64_t ignore_pat : 1; // Ignore PAT
uint64_t large_page : 1; // Large page indicator
uint64_t accessed : 1; // Accessed flag
uint64_t dirty : 1; // Dirty flag
uint64_t user_execute : 1; // User mode execute
uint64_t reserved : 1;
uint64_t pfn : 36; // Page frame number
uint64_t reserved2 : 16;
};
} ept_entry_t;
Rapid Virtualization Indexing (RVI) – AMD
AMD’s RVI (also called Nested Page Tables) provides similar functionality to EPT with optimized implementation for AMD processors.
I/O Virtualization Enhancements
I/O Memory Management Unit (IOMMU)
Both Intel (VT-d) and AMD (Vi) provide IOMMU capabilities for secure direct device access:
- DMA Remapping: Translates device DMA addresses through hardware
- Interrupt Remapping: Securely routes device interrupts to appropriate VMs
- Device Assignment: Enables direct hardware access for virtual machines
Performance Benefits and Benchmarks
CPU Virtualization Overhead
Hardware-assisted virtualization significantly reduces CPU overhead compared to software-only solutions:
| Workload Type | Software Virtualization | Hardware-assisted | Improvement |
|---|---|---|---|
| CPU-intensive | 15-25% overhead | 2-5% overhead | 80% reduction |
| Memory-intensive | 20-30% overhead | 3-8% overhead | |
| I/O operations | 40-60% overhead | 10-15% overhead | 75% reduction |
| System calls | 25-35% overhead | 5-10% overhead | 70% reduction |
Memory Virtualization Performance
EPT and RVI eliminate shadow page table overhead:
# Performance comparison example
# Shadow Page Tables (Software)
Memory overhead: 10-20% of guest memory
TLB miss penalty: 300-500 cycles
# Hardware-assisted (EPT/RVI)
Memory overhead: <2% of guest memory
TLB miss penalty: 100-150 cycles
Security Enhancements
Hardware Isolation
Hardware virtualization provides stronger isolation boundaries:
- Memory Protection: Hardware-enforced memory separation between VMs
- Privilege Separation: Clear separation between hypervisor and guest execution
- Attack Surface Reduction: Reduced hypervisor code complexity
Intel TXT and AMD SVM Security
Additional security features enhance trusted execution:
Practical Implementation Example
Basic Hypervisor Structure
Here’s a simplified example of hypervisor initialization using Intel VT-x:
// Hypervisor initialization pseudocode
int initialize_hypervisor(void) {
// Check for VMX support
if (!check_vmx_support()) {
return -1;
}
// Enable VMX in CR4
uint64_t cr4 = read_cr4();
cr4 |= CR4_VMXE;
write_cr4(cr4);
// Allocate VMXON region
void *vmxon_region = allocate_aligned_memory(4096, 4096);
setup_vmxon_region(vmxon_region);
// Enter VMX operation
if (vmxon(vmxon_region) != 0) {
return -1;
}
// Allocate and setup VMCS
void *vmcs_region = allocate_aligned_memory(4096, 4096);
setup_vmcs(vmcs_region);
// Load VMCS
if (vmptrld(vmcs_region) != 0) {
vmxoff();
return -1;
}
return 0;
}
// VM launch function
int launch_guest_vm(struct guest_state *guest) {
// Configure guest state in VMCS
vmwrite(GUEST_RIP, guest->entry_point);
vmwrite(GUEST_RSP, guest->stack_pointer);
vmwrite(GUEST_CR0, guest->cr0);
vmwrite(GUEST_CR3, guest->page_table_base);
// Configure execution controls
vmwrite(PIN_BASED_CONTROLS, PIN_EXTERNAL_INTERRUPT_EXIT);
vmwrite(PRIMARY_PROCESSOR_CONTROLS,
PROC_USE_MSR_BITMAPS | PROC_USE_SECONDARY_CONTROLS);
// Launch the VM
int result = vmlaunch();
if (result != 0) {
handle_vmlaunch_error();
return -1;
}
return 0;
}
Modern Virtualization Ecosystem
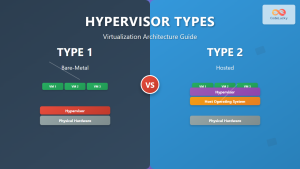
Hypervisor Types
Hardware-assisted virtualization enables both Type 1 and Type 2 hypervisors:
Container Integration
Hardware virtualization also enhances container security through technologies like:
- Intel Clear Containers: VM-based container isolation
- AWS Firecracker: Lightweight VM for serverless computing
- Google gVisor: User-space kernel with hardware assistance
Troubleshooting and Optimization
Common Issues
When implementing hardware-assisted virtualization, developers often encounter:
| Issue | Cause | Solution |
|---|---|---|
| VMXON failure | VMX not enabled in BIOS | Enable VT-x in firmware settings |
| VMCS corruption | Improper field initialization | Validate all VMCS fields before launch |
| EPT violations | Incorrect page table setup | Verify EPT entry permissions and mappings |
| Performance degradation | Excessive VM exits | Optimize intercept configuration |
Performance Tuning
// Optimization example: Minimize VM exits
uint32_t processor_controls =
PROC_USE_MSR_BITMAPS | // Selective MSR access
PROC_USE_IO_BITMAPS | // Selective I/O access
PROC_USE_SECONDARY_CONTROLS | // Enable advanced features
PROC_UNRESTRICTED_GUEST; // Reduce privilege checks
// Configure MSR bitmap to allow direct access
void configure_msr_bitmap(void *msr_bitmap) {
// Allow direct access to performance counters
clear_msr_intercept(msr_bitmap, MSR_IA32_PERF_GLOBAL_CTRL);
clear_msr_intercept(msr_bitmap, MSR_IA32_PMC0);
// Intercept sensitive MSRs
set_msr_intercept(msr_bitmap, MSR_IA32_FEATURE_CONTROL);
set_msr_intercept(msr_bitmap, MSR_IA32_VMX_BASIC);
}
Future Developments
Emerging Technologies
Hardware-assisted virtualization continues evolving with new capabilities:
- Memory Protection Keys: Fine-grained memory access control
- Control Flow Integrity: Hardware-enforced execution flow protection
- Confidential Computing: Encrypted VM memory and secure enclaves
- SR-IOV Evolution: Enhanced device virtualization capabilities
Cloud Computing Integration
Modern cloud platforms extensively leverage hardware virtualization for:
- Multi-tenant Isolation: Secure workload separation
- Resource Efficiency: Optimal hardware utilization
- Elastic Scaling: Dynamic resource allocation
- Security Boundaries: Hardware-enforced tenant isolation
Conclusion
Hardware-assisted virtualization through Intel VT-x and AMD-V has fundamentally transformed computing infrastructure, enabling efficient, secure, and scalable virtual machine deployment. These technologies eliminate the performance bottlenecks and security limitations of software-only virtualization while providing robust isolation mechanisms essential for modern cloud computing, containerization, and security applications.
Understanding these hardware capabilities enables developers and system administrators to build more efficient hypervisors, optimize virtual machine performance, and implement secure multi-tenant environments. As processor manufacturers continue advancing virtualization features, we can expect even greater performance improvements and security enhancements in future generations.
The investment in learning hardware-assisted virtualization pays dividends across multiple domains, from operating system development to cloud architecture design, making it an essential skill for modern systems professionals.
- Introduction to Hardware-assisted Virtualization
- Understanding Virtualization Challenges
- Intel VT-x Architecture
- AMD-V (SVM) Architecture
- Memory Virtualization
- I/O Virtualization Enhancements
- Performance Benefits and Benchmarks
- Security Enhancements
- Practical Implementation Example
- Modern Virtualization Ecosystem
- Troubleshooting and Optimization
- Future Developments
- Conclusion