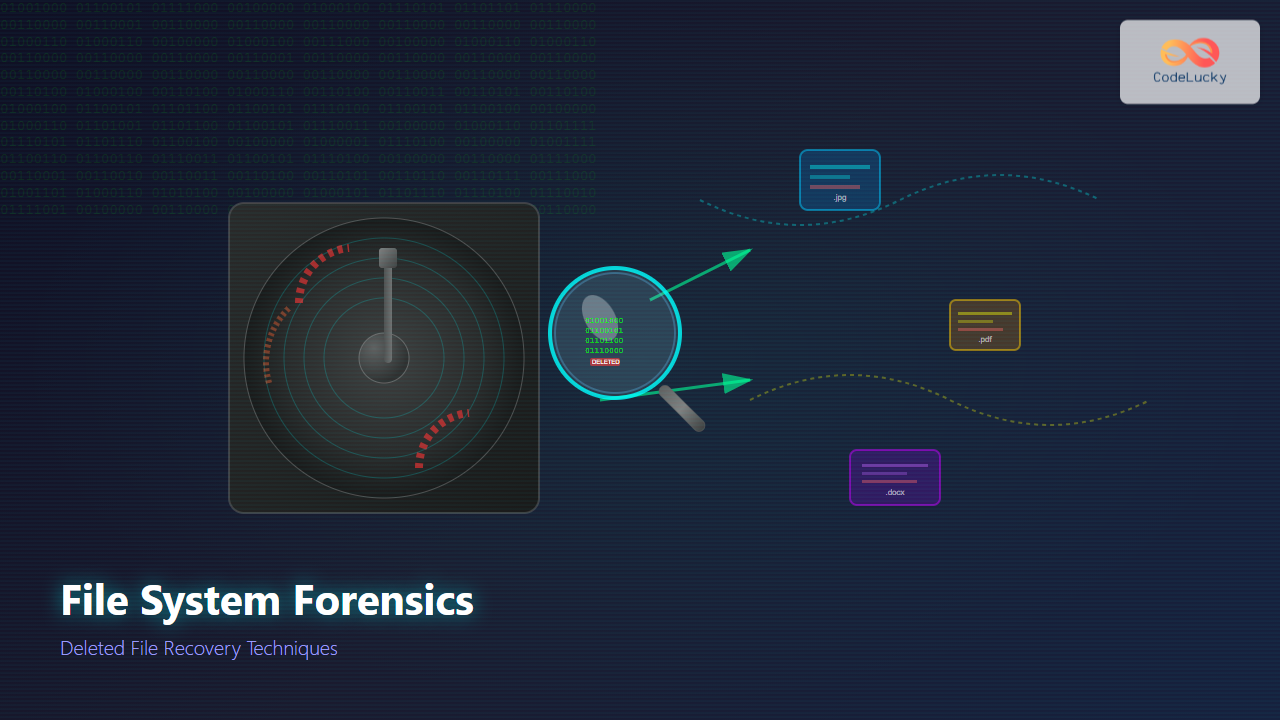
Understanding File System Forensics
File system forensics is a critical discipline within digital forensics that focuses on analyzing file systems to recover deleted data, understand file operations, and reconstruct digital evidence. When files are “deleted” from a computer system, they’re rarely completely erased immediately, making recovery possible through various forensic techniques.
The foundation of file system forensics lies in understanding how operating systems manage data storage. Modern file systems use complex structures including metadata tables, allocation bitmaps, and journaling mechanisms that can preserve traces of deleted files long after they appear to be gone.
How File Deletion Actually Works
The Deletion Process
Contrary to popular belief, when you delete a file, the operating system doesn’t immediately overwrite the actual data. Instead, it follows a multi-step process:
- Metadata Removal: The file’s entry is removed from the directory structure
- Allocation Marking: The file’s data blocks are marked as “available” in the allocation table
- Reference Clearing: Directory pointers to the file are cleared or nullified
- Eventual Overwriting: Data blocks may be overwritten when new files need storage space
File System Specific Behavior
NTFS (Windows): Uses Master File Table (MFT) entries that contain file metadata. Deleted files often remain in the MFT with modified attributes, and the actual data persists in unallocated clusters until overwritten.
ext4 (Linux): Employs inodes to store file metadata. When files are deleted, inode entries are marked as free, but the underlying data blocks typically remain intact until reused by new files.
APFS (macOS): Features copy-on-write semantics and snapshots, which can preserve deleted file data in previous filesystem states even after standard deletion.
Key Forensic Concepts and Terminology
Slack Space
File slack space occurs when a file doesn’t completely fill its allocated cluster. The unused portion of the final cluster may contain remnants of previously deleted files, creating a goldmine for forensic analysis.
# Example: Analyzing slack space in a 4KB cluster
File Size: 1,500 bytes
Cluster Size: 4,096 bytes
Slack Space: 4,096 - 1,500 = 2,596 bytes of potential evidence
Unallocated Space
Unallocated space represents areas of the storage medium not currently assigned to any file. This space frequently contains complete or partial deleted files and is a primary target for recovery operations.
File Carving
File carving is the process of extracting files from unallocated space without relying on file system metadata. This technique uses file signatures (magic numbers) to identify file beginnings and ends.
| File Type | Header Signature | Footer Signature |
|---|---|---|
| JPEG | FF D8 FF | FF D9 |
| 25 50 44 46 | 25 25 45 4F 46 | |
| PNG | 89 50 4E 47 | 49 45 4E 44 AE 42 60 82 |
| ZIP | 50 4B 03 04 | 50 4B 05 06 |
Deleted File Recovery Techniques
Metadata-Based Recovery
This approach leverages residual filesystem metadata to locate and recover deleted files. Tools analyze structures like the MFT in NTFS or inode tables in ext filesystems to find entries marked as deleted but still containing valid data pointers.
# Example: Basic MFT analysis pseudocode
def analyze_mft_entry(entry):
if entry.flags & MFT_DELETED:
if entry.data_runs_valid():
return reconstruct_file(entry.data_runs)
return None
for entry in mft_entries:
recovered_file = analyze_mft_entry(entry)
if recovered_file:
save_recovered_file(recovered_file)
Signature-Based File Carving
File carving searches raw disk data for known file signatures, enabling recovery even when metadata is corrupted or overwritten. Advanced carving techniques include:
- Header/Footer Carving: Matches file headers with corresponding footers
- Structure-Based Carving: Analyzes internal file structures for validation
- Fragment Recovery: Reconstructs fragmented files across non-contiguous sectors
Journal and Log Analysis
Modern filesystems maintain journals or logs that record file operations. These structures can provide valuable information about deleted files, including:
- Original file locations and sizes
- Deletion timestamps
- Associated metadata changes
- Transaction sequences leading to deletion
Practical Recovery Tools and Methods
Command-Line Tools
TestDisk and PhotoRec: Open-source utilities for partition recovery and file carving respectively.
# PhotoRec example usage
sudo photorec /dev/sdb1
# Interactive menu allows selection of:
# - File types to recover
# - Destination directory
# - Search algorithms
Sleuth Kit (TSK): Comprehensive forensic analysis framework with command-line tools for various recovery tasks.
# List deleted files in NTFS filesystem
fls -rd /dev/sdb1
# Recover specific file by inode
icat /dev/sdb1 1234 > recovered_file.txt
# Analyze file system journal
jls /dev/sdb1
Specialized Forensic Suites
EnCase: Industry-standard commercial forensic platform with advanced deleted file recovery capabilities, including predictive file carving and timeline analysis.
FTK (Forensic Toolkit): Comprehensive forensic suite featuring automated deleted file detection, advanced searching, and integrated reporting capabilities.
X-Ways Forensics: Powerful forensic tool with sophisticated carving algorithms, including support for custom file types and fragmented file reconstruction.
Advanced Recovery Scenarios
Dealing with File Fragmentation
Fragmented files present significant recovery challenges as their data blocks are scattered across the storage medium. Advanced techniques include:
Overwritten Data Recovery
When deleted files are partially overwritten, forensic analysts employ several strategies:
- Partial Recovery: Extract salvageable portions of overwritten files
- Cross-Reference Analysis: Use related files or cache data for reconstruction
- Lower-Level Recovery: Analyze magnetic force microscopy or raw flash memory for traces
Encrypted File System Challenges
Modern encrypted filesystems (FileVault, BitLocker, LUKS) complicate recovery efforts. Successful recovery typically requires:
- Access to encryption keys or passwords
- Recovery of key material from memory dumps
- Exploitation of implementation vulnerabilities
- Analysis of unencrypted metadata structures
Forensic Best Practices and Legal Considerations
Evidence Preservation
Imaging: Always work with forensic images rather than original media to preserve evidence integrity. Use tools like dd, dcfldd, or commercial imaging solutions that generate cryptographic hashes for verification.
# Create forensic image with verification
dd if=/dev/sdb of=evidence.img bs=64K conv=noerror,sync
md5sum evidence.img > evidence.img.md5
sha256sum evidence.img > evidence.img.sha256
Chain of Custody
Maintain detailed documentation of all recovery procedures, including:
- Timestamps of all operations
- Tools and versions used
- Personnel involved in analysis
- Hash values for verification
- Environmental conditions during analysis
Legal and Ethical Considerations
File system forensics must comply with applicable laws and regulations:
- Authorization: Ensure proper legal authority for data recovery activities
- Privacy: Respect privacy rights and data protection regulations
- Admissibility: Follow procedures that maintain evidence admissibility in legal proceedings
- Scope Limitation: Restrict analysis to authorized data and time periods
Emerging Trends and Technologies
SSD and Flash Memory Forensics
Solid-state drives introduce unique challenges for deleted file recovery due to wear leveling, TRIM commands, and garbage collection. Recovery strategies must account for:
- Logical-to-physical address translation complexity
- Controller-level data management policies
- Reduced data remnant persistence
- Encryption at the hardware level
Cloud Storage Forensics
Cloud-based storage systems require specialized forensic approaches considering:
- Distributed data storage across multiple locations
- Synchronization artifacts and version history
- API-based evidence collection methods
- Jurisdictional and access control challenges
Machine Learning Applications
AI and machine learning enhance forensic capabilities through:
- Intelligent File Classification: Automated identification of file types and content
- Pattern Recognition: Detection of suspicious deletion patterns or data hiding attempts
- Predictive Analysis: Estimation of data recovery success rates
- Anomaly Detection: Identification of unusual filesystem behaviors
Conclusion
File system forensics and deleted file recovery represent critical capabilities in modern digital investigations. As storage technologies evolve and data protection mechanisms become more sophisticated, forensic practitioners must continually adapt their techniques and tools.
Success in this field requires a deep understanding of filesystem internals, proficiency with specialized recovery tools, and adherence to strict forensic protocols. Whether investigating cybersecurity incidents, conducting legal discovery, or performing data recovery operations, the principles and techniques outlined in this guide provide a solid foundation for effective file system forensics.
The future of deleted file recovery will likely see increased integration of artificial intelligence, enhanced support for emerging storage technologies, and continued evolution of legal frameworks governing digital evidence. Staying current with these developments while maintaining rigorous technical and ethical standards remains essential for forensic professionals in this rapidly advancing field.