What is a Distributed Operating System?
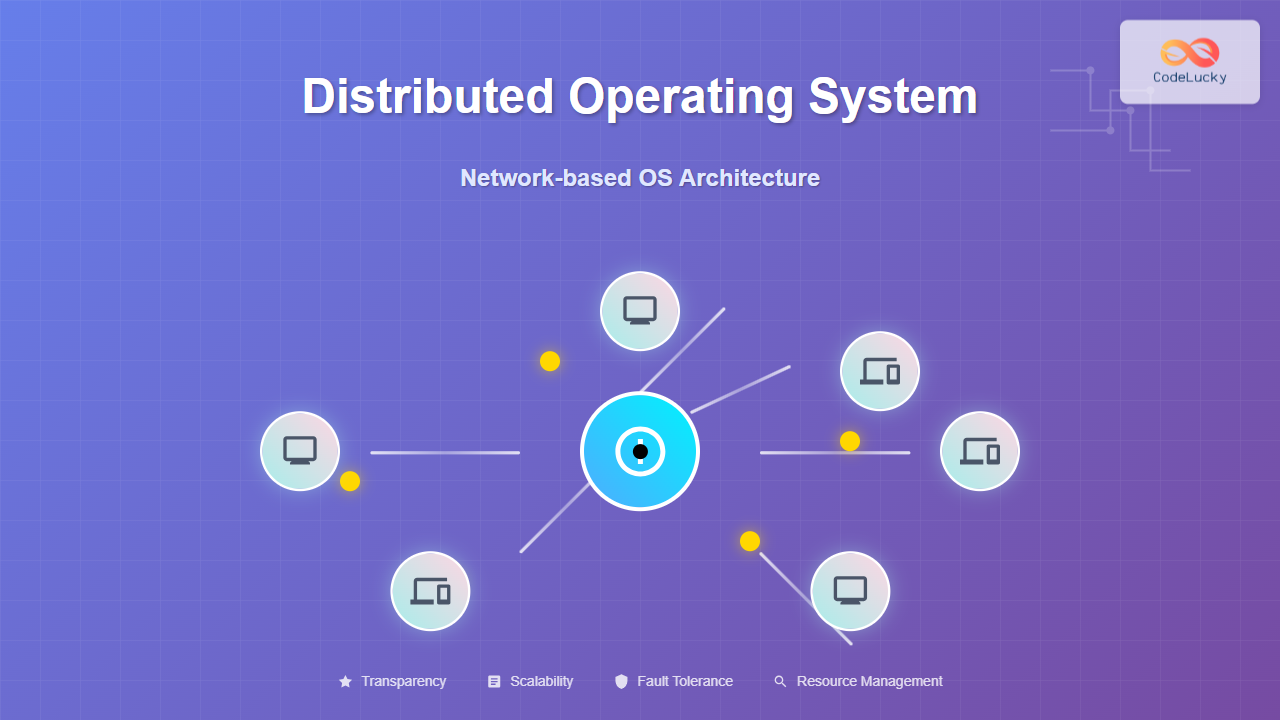
A distributed operating system is a sophisticated software system that manages and coordinates multiple interconnected computers, making them appear and function as a single unified system to users and applications. Unlike traditional centralized operating systems that run on a single machine, distributed operating systems leverage the collective computational power, storage, and resources of multiple networked nodes to deliver enhanced performance, reliability, and scalability.
The fundamental principle behind distributed operating systems is transparency – users interact with the system without being aware of the underlying distributed nature. Whether accessing files, running processes, or utilizing system resources, the complexity of network communication and resource distribution remains completely hidden from the end user.
Core Architecture Components
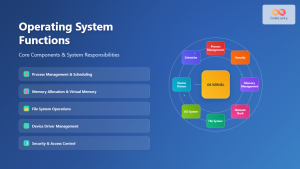
A distributed operating system consists of several critical architectural components that work together to provide seamless operation across multiple nodes:
Network Communication Layer
The communication layer serves as the backbone of distributed operating systems, enabling seamless data exchange between nodes. This layer implements various communication protocols and mechanisms:
- Message Passing: Nodes communicate through structured messages containing data and control information
- Remote Procedure Calls (RPC): Allows processes to execute procedures on remote nodes as if they were local
- Shared Memory Abstraction: Creates the illusion of shared memory across distributed nodes
- Network Protocols: TCP/IP, UDP, and specialized distributed system protocols
Resource Management System
Resource management in distributed systems involves coordinating and allocating various computational resources across multiple nodes:
- CPU Scheduling: Distributing computational tasks across available processors
- Memory Management: Managing distributed memory pools and virtual memory systems
- Storage Coordination: Handling distributed file systems and data replication
- Load Balancing: Ensuring optimal resource utilization across all nodes
Key Characteristics and Features
Transparency Levels
Distributed operating systems provide multiple levels of transparency to create a seamless user experience:
| Transparency Type | Description | Example |
|---|---|---|
| Location Transparency | Users don’t need to know where resources are located | Accessing files without knowing which server hosts them |
| Migration Transparency | Resources can move between nodes without user awareness | Process migration during load balancing |
| Replication Transparency | Multiple copies of resources exist without user knowledge | File replication for fault tolerance |
| Failure Transparency | System continues operating despite node failures | Automatic failover to backup nodes |
Scalability and Performance
Distributed operating systems offer significant advantages in terms of scalability and performance optimization:
- Horizontal Scaling: Adding more nodes to increase system capacity
- Parallel Processing: Simultaneous execution of tasks across multiple processors
- Resource Pooling: Combining computational resources for enhanced performance
- Geographic Distribution: Nodes can be located across different geographic regions
Communication Mechanisms
Inter-Process Communication (IPC)
Effective communication between processes running on different nodes is crucial for distributed systems functionality. The primary IPC mechanisms include:
Message Passing Systems
Message passing provides a robust communication model where processes exchange information through structured messages:
# Example: Distributed message passing
import socket
import json
class DistributedMessenger:
def __init__(self, node_id, port):
self.node_id = node_id
self.port = port
self.socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
def send_message(self, target_node, message):
try:
# Connect to target node
self.socket.connect((target_node['ip'], target_node['port']))
# Prepare message with metadata
msg_data = {
'sender': self.node_id,
'timestamp': time.time(),
'content': message
}
# Send serialized message
self.socket.send(json.dumps(msg_data).encode())
# Receive acknowledgment
response = self.socket.recv(1024).decode()
return json.loads(response)
except Exception as e:
return {'error': str(e)}
finally:
self.socket.close()
# Usage example
messenger = DistributedMessenger('node_1', 8080)
result = messenger.send_message(
{'ip': '192.168.1.100', 'port': 8081},
'Process migration request'
)
Remote Procedure Calls (RPC)
RPC mechanisms allow processes to execute procedures on remote nodes transparently:
// Example: RPC implementation in distributed OS
public class DistributedRPC {
private NetworkInterface network;
private RequestHandler handler;
public Object remoteCall(String nodeId, String procedure, Object[] params) {
try {
// Serialize procedure call
RPCRequest request = new RPCRequest(procedure, params);
byte[] serializedRequest = serialize(request);
// Send to remote node
RPCResponse response = network.sendRequest(nodeId, serializedRequest);
// Handle response
if (response.isSuccess()) {
return deserialize(response.getResult());
} else {
throw new RemoteException(response.getErrorMessage());
}
} catch (NetworkException e) {
// Implement fault tolerance
return handleFailure(nodeId, procedure, params);
}
}
private Object handleFailure(String nodeId, String procedure, Object[] params) {
// Find alternative node or cache result
String backupNode = findBackupNode(nodeId);
if (backupNode != null) {
return remoteCall(backupNode, procedure, params);
}
return null;
}
}
Synchronization and Coordination
Distributed Synchronization Challenges
Coordinating activities across multiple nodes presents unique challenges that distributed operating systems must address:
- Clock Synchronization: Maintaining consistent time across all nodes
- Mutual Exclusion: Ensuring exclusive access to shared resources
- Deadlock Prevention: Avoiding circular wait conditions in distributed environments
- Consensus Algorithms: Achieving agreement among distributed nodes
Distributed Locking Mechanisms
Implementing effective locking mechanisms ensures data consistency across distributed nodes:
// Distributed Lock Implementation
class DistributedLock {
private:
std::string resource_id;
std::vector<Node> nodes;
int majority_count;
public:
bool acquireLock(int timeout_ms) {
auto start_time = std::chrono::steady_clock::now();
int votes = 0;
// Request lock from majority of nodes
for (auto& node : nodes) {
LockRequest request(resource_id, getCurrentTimestamp());
try {
LockResponse response = sendLockRequest(node, request);
if (response.granted) {
votes++;
}
// Check if majority achieved
if (votes >= majority_count) {
return true;
}
} catch (NetworkTimeoutException& e) {
// Continue with other nodes
continue;
}
// Check timeout
auto current_time = std::chrono::steady_clock::now();
auto elapsed = std::chrono::duration_cast<std::chrono::milliseconds>
(current_time - start_time).count();
if (elapsed > timeout_ms) {
break;
}
}
// Release partial locks if majority not achieved
if (votes < majority_count) {
releaseLock();
return false;
}
return true;
}
void releaseLock() {
for (auto& node : nodes) {
ReleaseRequest request(resource_id);
sendReleaseRequest(node, request);
}
}
};
Fault Tolerance and Reliability
Failure Detection and Recovery
Distributed operating systems implement sophisticated mechanisms to detect and recover from various types of failures:
- Node Failures: Complete hardware or software failures
- Network Partitions: Communication failures between node groups
- Byzantine Failures: Nodes producing incorrect or malicious behavior
- Performance Degradation: Nodes operating below expected performance levels
Replication Strategies
Data and process replication provides fault tolerance through redundancy:
Real-World Implementations
Amoeba Operating System
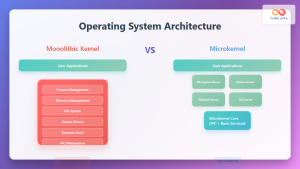
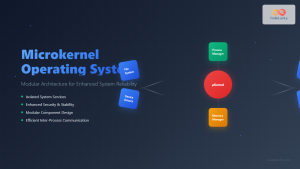
Amoeba was one of the pioneering distributed operating systems developed at Vrije Universiteit Amsterdam. Key features include:
- Microkernel Architecture: Minimal kernel with services running as user processes
- Location-Independent Naming: Objects identified by capabilities rather than locations
- Process Migration: Dynamic process relocation for load balancing
- Distributed File System: Files stored across multiple servers with automatic replication
Plan 9 from Bell Labs
Plan 9 represents a research-oriented distributed operating system with innovative design principles:
- Everything is a File: All system resources represented as files in a namespace
- Network Transparency: Remote resources accessed identically to local ones
- Protocol Independence: Multiple network protocols supported simultaneously
- Dynamic Resource Binding: Resources can be mounted and unmounted dynamically
Modern Cloud Operating Systems
Contemporary distributed systems like Kubernetes and Docker Swarm implement distributed operating system principles:
# Kubernetes Distributed Application Example
apiVersion: apps/v1
kind: Deployment
metadata:
name: distributed-app
spec:
replicas: 5
selector:
matchLabels:
app: distributed-app
template:
metadata:
labels:
app: distributed-app
spec:
containers:
- name: app-container
image: myapp:latest
ports:
- containerPort: 8080
resources:
requests:
memory: "256Mi"
cpu: "250m"
limits:
memory: "512Mi"
cpu: "500m"
nodeSelector:
zone: distributed-cluster
---
apiVersion: v1
kind: Service
metadata:
name: distributed-service
spec:
selector:
app: distributed-app
ports:
- port: 80
targetPort: 8080
type: LoadBalancer
Performance Optimization Strategies
Load Distribution Algorithms
Effective load balancing ensures optimal resource utilization across distributed nodes:
class DistributedLoadBalancer:
def __init__(self, nodes):
self.nodes = nodes
self.load_metrics = {}
self.algorithm = 'weighted_round_robin'
def select_node(self, task):
if self.algorithm == 'least_connections':
return self._least_connections()
elif self.algorithm == 'weighted_round_robin':
return self._weighted_round_robin()
elif self.algorithm == 'resource_based':
return self._resource_based_selection(task)
def _resource_based_selection(self, task):
best_node = None
best_score = float('-inf')
for node in self.nodes:
# Calculate node fitness score
cpu_score = (100 - node.cpu_usage) * 0.4
memory_score = (100 - node.memory_usage) * 0.3
network_score = node.network_bandwidth * 0.2
load_score = (100 - node.current_load) * 0.1
total_score = cpu_score + memory_score + network_score + load_score
if total_score > best_score:
best_score = total_score
best_node = node
return best_node
def update_node_metrics(self, node_id, metrics):
self.load_metrics[node_id] = {
'cpu_usage': metrics['cpu'],
'memory_usage': metrics['memory'],
'active_connections': metrics['connections'],
'response_time': metrics['response_time'],
'timestamp': time.time()
}
Caching and Data Locality
Optimizing data access patterns reduces network overhead and improves system performance:
- Distributed Caching: Strategic placement of frequently accessed data
- Data Prefetching: Anticipatory data loading based on access patterns
- Locality-Aware Scheduling: Scheduling tasks near required data
- Content Delivery Networks: Geographic distribution of data replicas
Security in Distributed Operating Systems
Authentication and Authorization
Securing distributed systems requires comprehensive authentication and authorization mechanisms:
- Distributed Authentication: Single sign-on across multiple nodes
- Certificate-Based Security: Public key infrastructure for node verification
- Access Control Lists: Fine-grained permission management
- Secure Communication: Encrypted data transmission between nodes
Threat Mitigation Strategies
Distributed systems face unique security challenges requiring specialized mitigation approaches:
public class DistributedSecurityManager {
private CertificateAuthority ca;
private EncryptionService encryption;
private AuditLogger auditLogger;
public boolean authenticateNode(NodeCredentials credentials) {
try {
// Verify certificate chain
Certificate nodeCert = credentials.getCertificate();
if (!ca.verifyCertificate(nodeCert)) {
auditLogger.logFailure("Invalid certificate", credentials.getNodeId());
return false;
}
// Check certificate revocation
if (ca.isRevoked(nodeCert)) {
auditLogger.logFailure("Revoked certificate", credentials.getNodeId());
return false;
}
// Verify digital signature
byte[] challenge = generateChallenge();
byte[] signature = credentials.signChallenge(challenge);
if (verifySignature(nodeCert.getPublicKey(), challenge, signature)) {
auditLogger.logSuccess("Node authenticated", credentials.getNodeId());
return true;
}
return false;
} catch (SecurityException e) {
auditLogger.logError("Authentication error", e);
return false;
}
}
public SecureChannel establishSecureChannel(String nodeId) {
// Implement perfect forward secrecy
KeyPair ephemeralKeys = generateEphemeralKeyPair();
EncryptionKey sessionKey = negotiateSessionKey(nodeId, ephemeralKeys);
return new SecureChannel(sessionKey, encryption);
}
}
Future Trends and Developments
Edge Computing Integration
The evolution of distributed operating systems increasingly incorporates edge computing paradigms, bringing computation closer to data sources and end users. This trend addresses latency requirements and bandwidth limitations in modern distributed applications.
Artificial Intelligence and Machine Learning
AI-powered distributed operating systems leverage machine learning for:
- Predictive Resource Management: Anticipating resource demands
- Intelligent Load Balancing: ML-based traffic distribution
- Automated Failure Prediction: Proactive system maintenance
- Adaptive Performance Tuning: Dynamic system optimization
Quantum-Safe Distributed Systems
As quantum computing advances, distributed operating systems must evolve to incorporate quantum-resistant security mechanisms and potentially leverage quantum computing capabilities for enhanced performance and security.
Best Practices for Implementation
Design Principles
Successful distributed operating system implementation requires adherence to fundamental design principles:
- Modularity: Design loosely coupled, independently deployable components
- Scalability: Ensure system can grow horizontally and vertically
- Fault Tolerance: Plan for failures at every level
- Performance: Optimize for latency and throughput requirements
- Security: Implement defense-in-depth strategies
- Maintainability: Design for easy updates and modifications
Development and Testing Strategies
Testing distributed systems requires specialized approaches to ensure reliability and performance:
- Chaos Engineering: Deliberately introducing failures to test resilience
- Load Testing: Validating performance under various load conditions
- Network Partition Testing: Verifying behavior during communication failures
- Integration Testing: Ensuring proper component interaction
Distributed operating systems represent a fundamental shift from traditional centralized computing models, offering unprecedented scalability, reliability, and performance through network-based resource coordination. As organizations continue to embrace distributed architectures for mission-critical applications, understanding these systems’ principles, implementations, and best practices becomes increasingly vital for system architects, developers, and IT professionals.
The continuous evolution of distributed operating systems, driven by advances in cloud computing, edge computing, and artificial intelligence, ensures their continued relevance in addressing the computational challenges of tomorrow’s interconnected world.
- What is a Distributed Operating System?
- Core Architecture Components
- Key Characteristics and Features
- Communication Mechanisms
- Synchronization and Coordination
- Fault Tolerance and Reliability
- Real-World Implementations
- Performance Optimization Strategies
- Security in Distributed Operating Systems
- Future Trends and Developments
- Best Practices for Implementation