Capability-based security represents a revolutionary approach to access control in modern operating systems, moving beyond traditional user-based permissions to implement object-oriented security models. This paradigm shift offers enhanced security, better scalability, and more intuitive permission management through the concept of capabilities – unforgeable tokens that grant specific access rights to system resources.
Understanding Capability-based Security
A capability-based security system fundamentally changes how we think about access control. Instead of asking “who is trying to access this resource?”, it asks “what permission does this entity possess?” This approach treats security permissions as transferable objects that can be passed between processes, stored, and manipulated like any other data structure.
The core principle revolves around capabilities – cryptographically secure tokens that embody specific access rights. Unlike traditional access control lists (ACLs), capabilities are held by the requesting entity rather than being attached to the resource itself.
Key Components of Capability Systems
Capability-based systems consist of several fundamental elements:
- Capability Objects: Unforgeable tokens containing access rights and resource identifiers
- Object References: Secure pointers to system resources that cannot be guessed or forged
- Capability Domains: Isolated execution environments that hold sets of capabilities
- Authority Transfer: Mechanisms for safely passing capabilities between entities
How Capability-based Security Works
The operational model of capability-based security differs significantly from traditional approaches. Here’s how a typical access request proceeds:
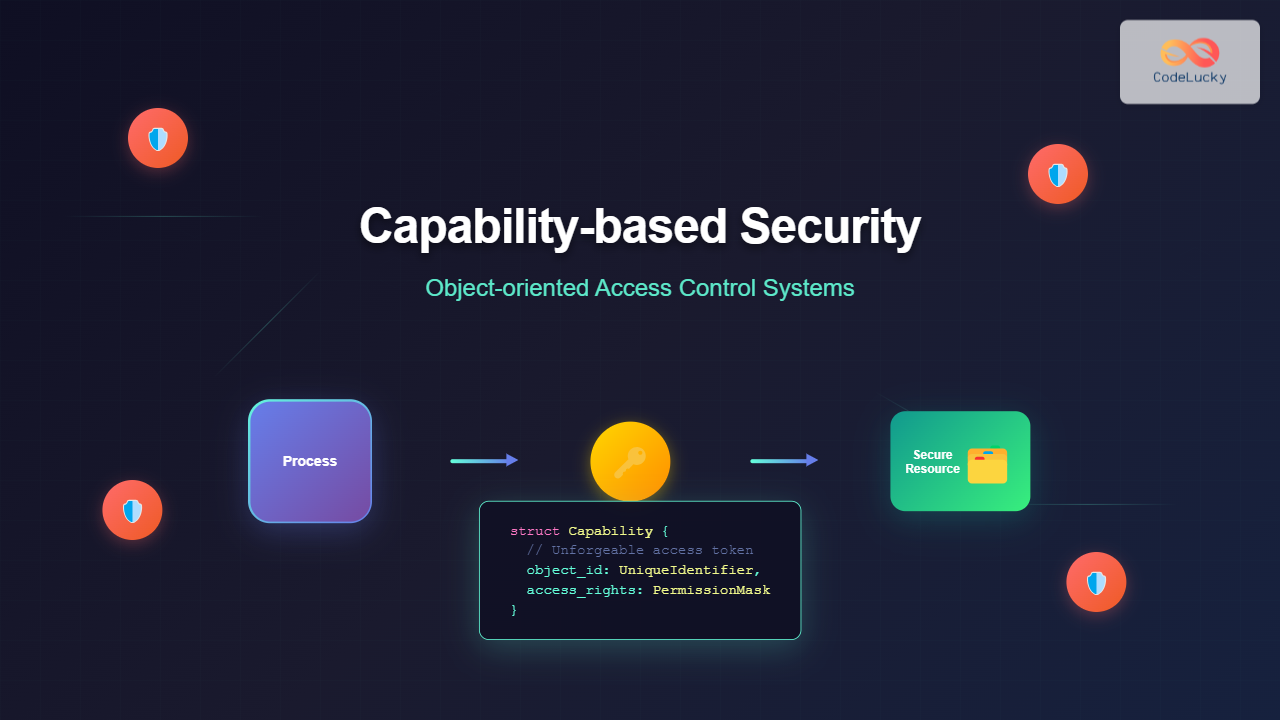
Capability Structure and Properties
A typical capability contains several critical components:
struct Capability {
object_id: UniqueIdentifier,
access_rights: PermissionMask,
validity_period: TimeRange,
cryptographic_signature: Hash,
delegation_depth: Integer
}
Each capability must be unforgeable, meaning it cannot be created, modified, or duplicated without proper authorization. This is typically achieved through cryptographic signatures or by storing capabilities in protected kernel memory.
Advantages of Capability-based Security
Capability-based systems offer numerous advantages over traditional access control mechanisms:
Fine-grained Access Control
Capabilities enable precise permission specification at the object level. Instead of broad user categories, each capability can specify exactly what operations are permitted on a specific resource.
Principle of Least Privilege
Programs naturally operate with minimal necessary permissions since they can only access resources for which they hold valid capabilities. This significantly reduces the attack surface and potential for privilege escalation.
Dynamic Permission Management
Capabilities can be created, transferred, and revoked dynamically during program execution, enabling flexible security policies that adapt to changing requirements.
Simplified Security Analysis
Security analysis becomes more straightforward since access rights are explicitly represented as data structures that can be inspected and verified.
Implementation Models
Capability-based security can be implemented through various architectural approaches:
Hardware-supported Capabilities
Some systems implement capabilities at the hardware level, using special memory protection mechanisms and tagged architectures. Examples include the Cambridge CAP computer and Intel’s discontinued iAPX 432.
Software-based Capability Systems
Most modern implementations use software-based approaches where the operating system kernel manages capabilities as protected data structures.
Hybrid Approaches
Contemporary systems often combine capability-based mechanisms with traditional access control, creating hybrid models that leverage the strengths of both approaches.
Real-world Examples and Case Studies
EROS (Extremely Reliable Operating System)
EROS demonstrated pure capability-based design where every system resource was accessed through capabilities. The system achieved remarkable security properties by eliminating ambient authority entirely.
seL4 Microkernel
The seL4 microkernel uses capability-based access control for all system resources, including memory pages, interrupt handlers, and communication endpoints. This design enables formal verification of security properties.
Web Browser Security Models
Modern web browsers implement capability-like mechanisms through same-origin policies and permission APIs, where web pages must explicitly request access to sensitive resources like cameras or location data.
Challenges and Limitations
Despite their advantages, capability-based systems face several implementation challenges:
Revocation Problem
Once a capability is transferred to another entity, revoking access becomes complex since the capability holder may have created additional copies or delegated rights to other processes.
Confused Deputy Attack
Programs with multiple capabilities might be tricked into misusing their privileges on behalf of less-privileged entities, potentially leading to unauthorized access.
Performance Overhead
Capability validation and management can introduce performance overhead compared to simpler access control mechanisms, particularly in systems with frequent resource access patterns.
Complexity of Implementation
Implementing a secure capability system requires careful attention to many subtle details, making it more complex than traditional access control approaches.
Design Patterns and Best Practices
Capability Confinement
Design applications to operate within capability domains that limit the scope of available resources. This pattern helps implement the principle of least privilege effectively.
Authority Attenuation
When transferring capabilities, always provide the minimum necessary permissions. Create attenuated capabilities that have reduced access rights compared to the original.
Capability Wrapping
Wrap capabilities in higher-level abstractions that provide additional security checks and logging capabilities before granting access to underlying resources.
Integration with Modern Systems
Capability-based security principles are increasingly integrated into modern computing environments:
Container Security
Container platforms like Docker and Kubernetes implement capability-like mechanisms to control access to system resources, using Linux capabilities to limit container privileges.
Mobile Operating Systems
Both Android and iOS use permission models that resemble capability-based systems, requiring apps to explicitly request access to sensitive resources and allowing users to grant or deny specific permissions.
Cloud Computing
Cloud platforms implement capability-based access control through mechanisms like AWS IAM roles and policies, where access tokens grant specific permissions to cloud resources.
Future Directions and Research
Research in capability-based security continues to evolve, focusing on several key areas:
Distributed Capabilities
Extending capability-based security to distributed systems while maintaining security properties across network boundaries remains an active research area.
Blockchain and Distributed Ledgers
Exploring how blockchain technology can provide unforgeable capability tokens in decentralized environments without requiring a central authority.
Machine Learning Integration
Investigating how machine learning can enhance capability-based systems by predicting access patterns and automatically adjusting security policies.
Conclusion
Capability-based security represents a powerful paradigm for implementing object-oriented access control in modern computing systems. By treating permissions as transferable objects rather than static attributes, these systems provide enhanced security, better scalability, and more intuitive permission management.
While implementation challenges exist, the core principles of capability-based security continue to influence modern system design, from mobile app permissions to cloud security models. As computing systems become more distributed and complex, the flexibility and security properties of capability-based approaches become increasingly valuable.
Understanding capability-based security is essential for system designers, security professionals, and developers working on modern computing platforms. The concepts and patterns discussed in this article provide a foundation for implementing more secure and maintainable access control systems in various computing environments.