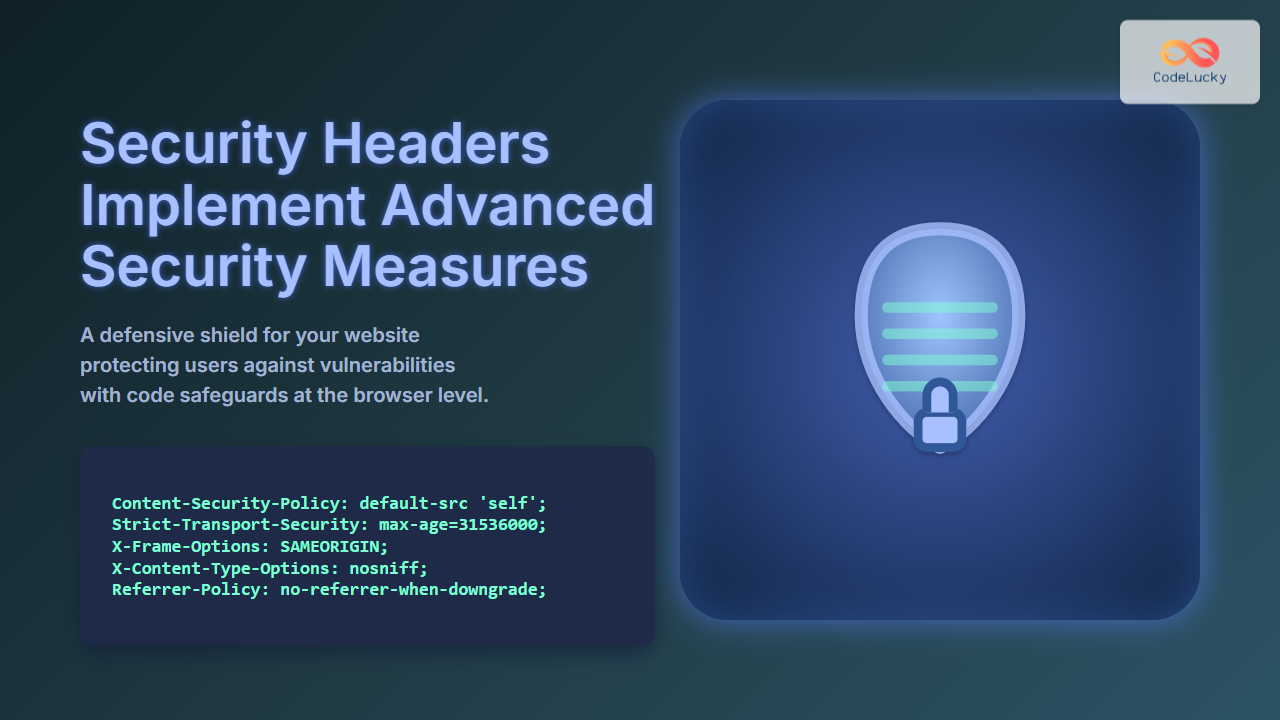
In today’s digital world, protecting web applications from malicious attacks is essential. One of the foundational ways to enhance security is through the implementation of security headers. These headers instruct browsers how to behave when handling your website’s content, mitigating threats like cross-site scripting (XSS), clickjacking, and other injection attacks. This article provides a detailed guide on advanced security headers, their purposes, practical implementation, and visualized concepts to deeply understand these vital security measures.
What Are Security Headers?
Security headers are HTTP response headers sent by the server to the browser. These headers define rules that strictly control how the browser interacts with your web content. Properly configured security headers reduce risks by enforcing security policies directly at the browser level.
Key Advanced Security Headers Explained
Here are the most impactful headers for boosting your website’s defense:
1. Content Security Policy (CSP)
CSP restricts the sources from which various content types (scripts, styles, images) can be loaded, effectively preventing XSS attacks.
Content-Security-Policy: default-src 'self'; img-src https://trustedsite.com; script-src 'self' 'unsafe-inline';In this example, only resources from the site itself or “trustedsite.com” are allowed for images, and scripts are limited to self and inline scripts (use cautiously).
2. Strict-Transport-Security (HSTS)
This header forces browsers to use HTTPS for all future requests, preventing downgrade attacks and ensuring encrypted communication.
Strict-Transport-Security: max-age=31536000; includeSubDomains; preloadSetting max-age to one year and including subdomains enhances HTTPS enforcement across your website’s domains.
3. X-Frame-Options
Prevents your website content from being embedded in iframes on other sites, protecting against clickjacking attacks.
X-Frame-Options: SAMEORIGINAlternatively, DENY blocks all framing, while ALLOW-FROM uri permits framing only on specified URIs.
4. X-Content-Type-Options
Prevents browsers from MIME-sniffing a response away from the declared content-type, protecting against some types of attacks.
X-Content-Type-Options: nosniff5. Referrer-Policy
Controls how much referrer information is sent to other sites, thereby enhancing privacy and reducing leakage of sensitive URLs.
Referrer-Policy: no-referrer-when-downgradePractical Example Implementation
Here’s how to implement these headers on an Nginx server:
server {
listen 443 ssl;
server_name example.com;
add_header Content-Security-Policy "default-src 'self'; img-src https://trustedsite.com; script-src 'self' 'unsafe-inline'";
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Content-Type-Options "nosniff" always;
add_header Referrer-Policy "no-referrer-when-downgrade" always;
# Other server configs...
}Visualizing Header Flow and Blocking
Interactive CSP Example
Test a basic CSP policy in your browser console:
document.querySelector('meta[http-equiv="Content-Security-Policy"]')?.remove();
var meta = document.createElement('meta');
meta.httpEquiv = "Content-Security-Policy";
meta.content = "default-src 'self'; script-src 'none'";
document.head.appendChild(meta);
alert('Attempting to run script blocked by CSP');
Try running an inline script now or loading external scripts to observe CSP blocking in real time.
Best Practices for Security Headers
- Test headers using tools like securityheaders.com.
- Gradually tighten CSP policies to avoid breaking legitimate resources.
- Use
report-uriorreport-todirectives in CSP for reporting violations. - Always enforce HTTPS and consider HSTS preload for better security.
- Keep headers updated as browsers evolve their security mechanisms.
Summary
Implementing advanced security headers establishes a robust first line of defense for web applications. These headers guard users against a variety of common and advanced cyber attacks by controlling resource loading, framing, content types, transport security, and referrer information.
This detailed article guides effective use of core headers including Content-Security-Policy, Strict-Transport-Security, X-Frame-Options, and others — all essential for modern web security hygiene.
Web developers and site administrators are encouraged to adopt these headers thoughtfully, test extensively, and continuously evolve configurations to keep pace with new vulnerabilities and browser updates.