Podman (Pod Manager) is a powerful, daemonless container engine that provides a Docker-compatible command-line interface for managing containers and pods on Linux systems. Developed by Red Hat, Podman offers enhanced security through rootless containers and direct integration with systemd, making it an excellent choice for modern container management.
What is Podman?
Podman is an open-source container management tool that allows you to develop, manage, and run OCI (Open Container Initiative) containers and pods without requiring a daemon. Unlike Docker, Podman runs containers as child processes, providing better security and resource management.
Key Features of Podman
- Daemonless Architecture: No background daemon required
- Rootless Containers: Run containers without root privileges
- Docker Compatibility: Drop-in replacement for Docker commands
- Pod Support: Native Kubernetes pod management
- Systemd Integration: Generate systemd service files
- Security: Enhanced security through user namespaces
Installing Podman on Linux
Installation varies by distribution. Here are the most common methods:
Ubuntu/Debian
# Update package list
sudo apt update
# Install Podman
sudo apt install podman
# Verify installation
podman --versionCentOS/RHEL/Fedora
# For CentOS/RHEL
sudo yum install podman
# For Fedora
sudo dnf install podman
# Verify installation
podman --versionBasic Podman Commands
Container Lifecycle Management
Let’s explore the fundamental commands for container management:
Running Your First Container
# Run a simple hello-world container
podman run hello-world
# Output:
# Hello from Docker!
# This message shows that your installation appears to be working correctly.Running Interactive Containers
# Run Ubuntu container interactively
podman run -it ubuntu:20.04 /bin/bash
# Inside container:
root@container-id:/# ls
bin boot dev etc home lib lib32 lib64 libx32 media mnt opt proc root run sbin srv sys tmp usr varRunning Detached Containers
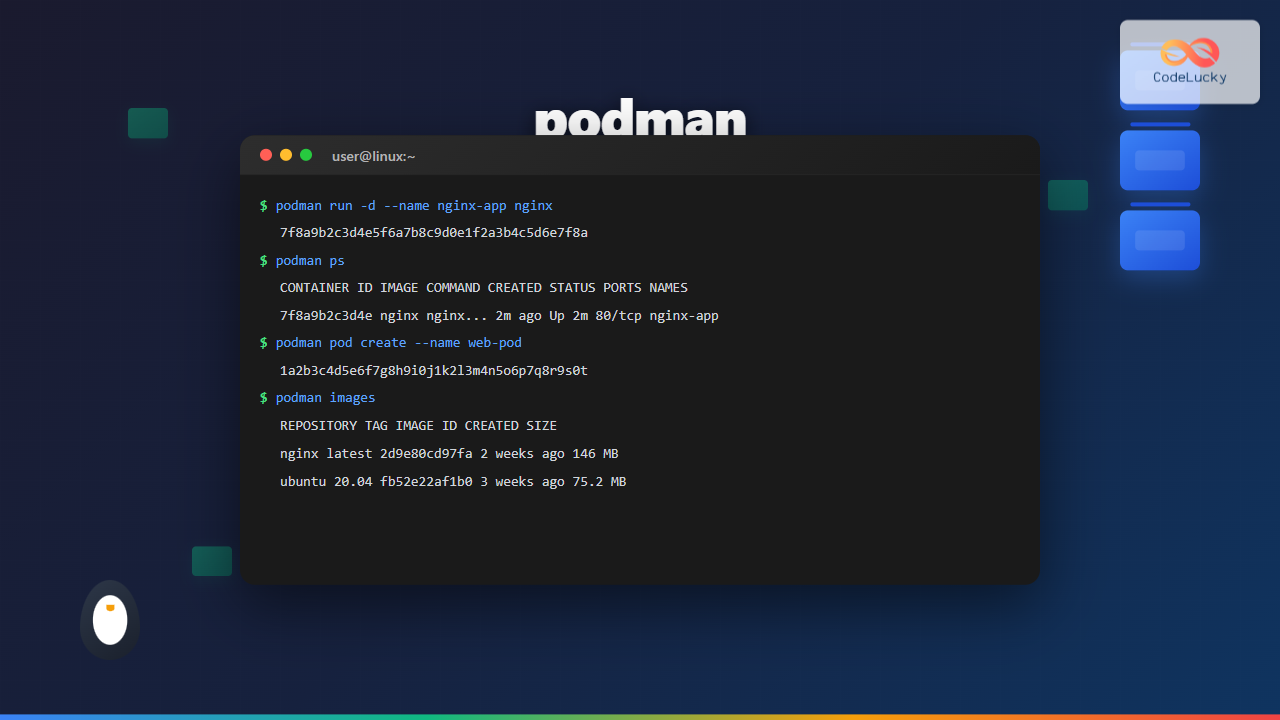
# Run Nginx in detached mode
podman run -d --name my-nginx -p 8080:80 nginx
# Output:
# 7f8a9b2c3d4e5f6a7b8c9d0e1f2a3b4c5d6e7f8a9b0c1d2e3f4a5b6c7d8e9f0aContainer Information and Management
Listing Containers
# List running containers
podman ps
# Output:
# CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
# 7f8a9b2c3d4e nginx nginx -g daemon o... 2 minutes ago Up 2 minutes ago 0.0.0.0:8080->80/tcp my-nginx
# List all containers (including stopped)
podman ps -aContainer Inspection
# Get detailed container information
podman inspect my-nginx
# Get specific information using format
podman inspect --format='{{.State.Status}}' my-nginx
# Output:
# runningContainer Logs
# View container logs
podman logs my-nginx
# Follow logs in real-time
podman logs -f my-nginx
# View last 50 lines
podman logs --tail 50 my-nginxContainer Control Commands
Starting and Stopping Containers
# Stop a running container
podman stop my-nginx
# Start a stopped container
podman start my-nginx
# Restart a container
podman restart my-nginx
# Pause/unpause a container
podman pause my-nginx
podman unpause my-nginxExecuting Commands in Running Containers
# Execute command in running container
podman exec my-nginx ls /etc
# Interactive shell in running container
podman exec -it my-nginx /bin/bash
# Run command as specific user
podman exec -u nginx my-nginx whoamiImage Management
Working with Container Images
Pulling Images
# Pull specific image
podman pull ubuntu:20.04
# Pull latest version
podman pull redis:latest
# Pull from specific registry
podman pull quay.io/podman/helloListing and Managing Images
# List all images
podman images
# Output:
# REPOSITORY TAG IMAGE ID CREATED SIZE
# docker.io/library/nginx latest 2d9e80cd97fa 2 weeks ago 146 MB
# docker.io/library/ubuntu 20.04 fb52e22af1b0 3 weeks ago 75.2 MB
# Remove specific image
podman rmi ubuntu:20.04
# Remove unused images
podman image pruneBuilding Custom Images
# Create Dockerfile
cat << EOF > Dockerfile
FROM ubuntu:20.04
RUN apt-get update && apt-get install -y curl
COPY app.py /app/
WORKDIR /app
CMD ["python3", "app.py"]
EOF
# Build image
podman build -t my-app:1.0 .
# Build with custom context
podman build -f Dockerfile.prod -t my-app:prod .Advanced Podman Features
Pod Management
Pods are groups of containers that share network and storage resources:
Creating and Managing Pods
# Create a new pod
podman pod create --name my-pod -p 8080:80
# List pods
podman pod ls
# Output:
# POD ID NAME STATUS CREATED INFRA ID # OF CONTAINERS
# 1a2b3c4d5e6f my-pod Created 10 seconds ago 7f8a9b2c3d4e 1
# Add containers to pod
podman run -dt --pod my-pod --name web-server nginx
podman run -dt --pod my-pod --name app-server python:3.9
# Inspect pod
podman pod inspect my-podPod Operations
# Start/stop entire pod
podman pod start my-pod
podman pod stop my-pod
# Remove pod (stops all containers first)
podman pod rm my-pod
# Generate Kubernetes YAML
podman generate kube my-pod > my-pod.yamlVolume Management
Creating and Using Volumes
# Create named volume
podman volume create my-data
# List volumes
podman volume ls
# Run container with volume
podman run -d --name database \
-v my-data:/var/lib/mysql \
mysql:8.0
# Bind mount host directory
podman run -d --name web-app \
-v /host/path:/container/path \
nginxVolume Inspection and Cleanup
# Inspect volume
podman volume inspect my-data
# Remove volume
podman volume rm my-data
# Remove unused volumes
podman volume pruneNetwork Management
Working with Networks
# List networks
podman network ls
# Output:
# NETWORK ID NAME DRIVER
# 2f259bab93aa podman bridge
# Create custom network
podman network create my-network
# Run container with custom network
podman run -d --network my-network \
--name web-server nginx
# Connect existing container to network
podman network connect my-network existing-containerRootless Containers
One of Podman’s standout features is the ability to run containers without root privileges:
Setting Up Rootless Mode
# Check if rootless is configured
podman info --format '{{.Host.Security.Rootless}}'
# Configure subuid and subgid (as root)
echo "username:100000:65536" >> /etc/subuid
echo "username:100000:65536" >> /etc/subgid
# Initialize rootless environment
podman system migrateBenefits of Rootless Containers
- Enhanced security through user namespaces
- No need for privileged daemon
- Better resource isolation
- Reduced attack surface
Systemd Integration
Podman integrates seamlessly with systemd for service management:
Generating Systemd Service Files
# Generate systemd service for container
podman generate systemd --name my-nginx
# Generate and save to file
podman generate systemd --name my-nginx \
--files --new
# Enable and start service
systemctl --user enable container-my-nginx.service
systemctl --user start container-my-nginx.serviceManaging Services
# Check service status
systemctl --user status container-my-nginx.service
# View service logs
journalctl --user -u container-my-nginx.service
# Restart service
systemctl --user restart container-my-nginx.serviceContainer Security Best Practices
Security Features
# Run container with read-only root filesystem
podman run -d --read-only --name secure-app nginx
# Set security options
podman run -d --security-opt label=disable \
--name app nginx
# Limit resources
podman run -d --memory 512m --cpus 1.5 \
--name limited-app nginx
# Run with specific user
podman run -d --user 1000:1000 \
--name user-app nginxTroubleshooting Common Issues
Container Won’t Start
# Check container status and logs
podman ps -a
podman logs container-name
# Inspect container configuration
podman inspect container-name
# Test with interactive mode
podman run -it image-name /bin/bashPermission Issues
# Check SELinux context
ls -Z /path/to/mounted/directory
# Fix SELinux labels
podman run -v /host/path:/container/path:Z image-name
# Check user namespaces
podman unshare cat /proc/self/uid_mapNetwork Connectivity
# Test container network
podman exec container-name ping google.com
# Check port mapping
podman port container-name
# Inspect network configuration
podman inspect container-name --format '{{.NetworkSettings}}'Podman vs Docker Comparison
| Feature | Podman | Docker |
|---|---|---|
| Architecture | Daemonless | Client-Server with daemon |
| Root Privileges | Rootless by default | Requires daemon as root |
| Pod Support | Native | Via Docker Compose |
| Systemd Integration | Built-in | Third-party solutions |
| Command Compatibility | Docker-compatible | Native commands |
Performance Optimization Tips
Resource Management
# Monitor resource usage
podman stats
# Set resource limits
podman run -d --memory 1g --cpus 2 \
--name optimized-app nginx
# Use multi-stage builds
FROM node:16 AS builder
WORKDIR /app
COPY package*.json ./
RUN npm ci --only=production
FROM node:16-alpine
WORKDIR /app
COPY --from=builder /app/node_modules ./node_modules
COPY . .
CMD ["node", "server.js"]Image Optimization
# Use specific tags instead of latest
podman pull nginx:1.21-alpine
# Clean up after builds
podman image prune -f
# Use .containerignore file
echo "node_modules" > .containerignore
echo "*.log" >> .containerignoreConclusion
Podman represents a significant advancement in container technology, offering enhanced security, better resource management, and seamless integration with Linux systems. Its daemonless architecture and rootless capabilities make it an excellent choice for production environments where security is paramount.
Whether you’re migrating from Docker or starting fresh with containers, Podman’s Docker-compatible interface ensures a smooth transition while providing additional benefits like pod support and systemd integration. The extensive command set and advanced features covered in this guide should help you effectively manage containers in any Linux environment.
As containerization continues to evolve, Podman’s approach to security-first, daemon-free container management positions it as a leading solution for modern application deployment and management.