In the world of algorithms, efficiency is everything. Problems in competitive programming, cryptography, and number theory often require computing large exponents modulo some number. Direct multiplication is not feasible because the numbers grow exponentially. This is where the Modular Exponentiation or Fast Power Algorithm comes into play.
This article dives deep into modular exponentiation, its importance, optimized algorithms, and Python implementation examples. We’ll also visualize the step-by-step execution to ensure you understand it both mathematically and computationally.
What is Modular Exponentiation?
Modular exponentiation computes:
(a^b) mod m
where a is the base, b is the exponent, and m is the modulus. The goal is to calculate this efficiently without directly computing large powers.
Why Do We Need Modular Exponentiation?
- Efficient Computation: Direct computation of
a^bis impractical because the result can explode in size. - Cryptography: Algorithms like RSA, Diffie–Hellman, and Elliptic Curve Cryptography depend on modular exponentiation.
- Competitive Programming: Problems involving combinatorics, modular inverses, and large numbers heavily rely on this technique.
Naive Approach: Why It Fails
A naive approach would multiply a exactly b times, reducing modulo m each time. The time complexity is O(b), which is infeasible when b can be as large as 1018.
The Fast Power Algorithm (Binary Exponentiation)
The Fast Power Algorithm, also called Binary Exponentiation, uses the binary representation of the exponent to reduce time complexity from O(b) to O(log b).
The core idea uses these rules:
- If
bis even:a^b = (a^(b/2))^2 - If
bis odd:a^b = a * (a^(b-1))
At each step, we divide the problem size in half, which results in logarithmic complexity.
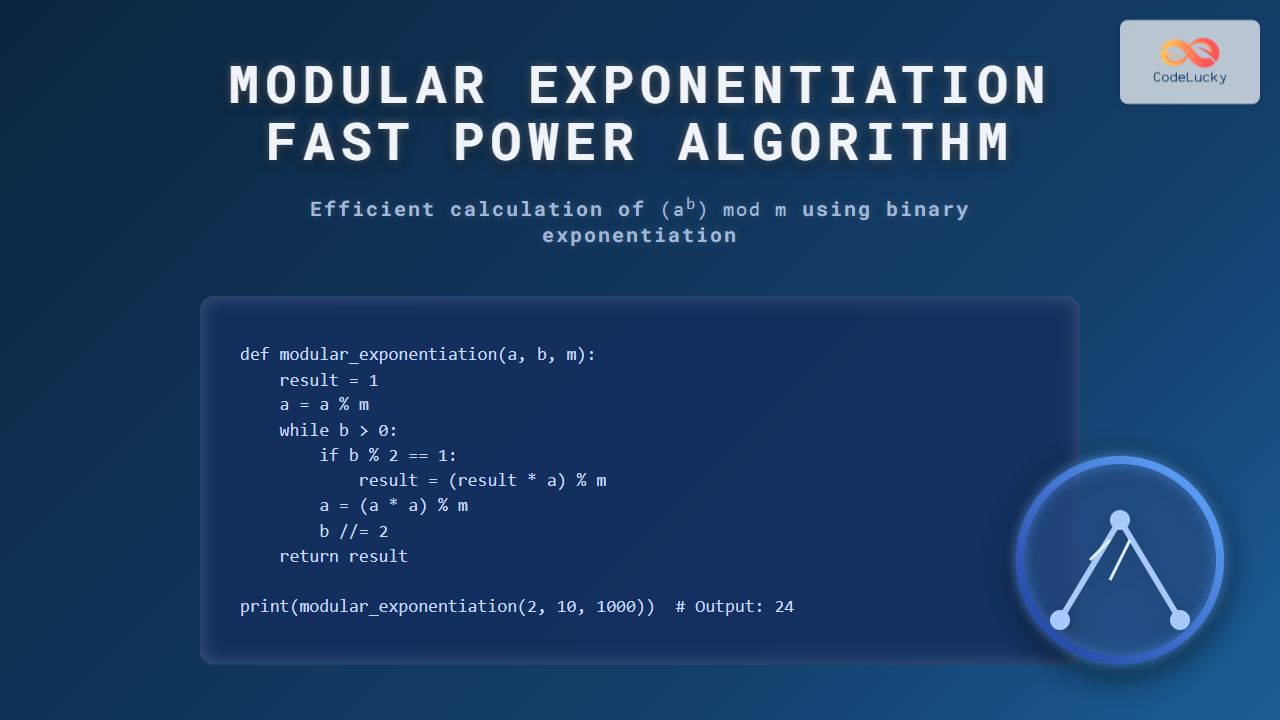
Python Implementation of Modular Exponentiation
def modular_exponentiation(a, b, m):
result = 1
a = a % m
while b > 0:
if b % 2 == 1: # If b is odd
result = (result * a) % m
a = (a * a) % m
b //= 2
return result
# Example usage:
print(modular_exponentiation(2, 10, 1000)) # Output: 24
This method ensures that multiplications never grow uncontrollably large, as every operation is reduced by modulo m.
Step-by-Step Example
Let’s compute 3^13 mod 7.
- Write exponent in binary: 13 = 1101 (base 2).
- Process from LSB to MSB.
- Maintain result as 1.
Computation:
- b=13 (odd): result = (1 * 3) mod 7 = 3
- a = (3*3) mod 7 = 2, b=6
- b=6 (even): skip multiplication
- a = (2*2) mod 7 = 4, b=3
- b=3 (odd): result = (3*4) mod 7 = 5
- a = (4*4) mod 7 = 2, b=1
- b=1 (odd): result = (5*2) mod 7 = 3
Final answer = 3.
Recursive Implementation
def fast_power_recursive(a, b, m):
if b == 0:
return 1
half = fast_power_recursive(a, b // 2, m)
half = (half * half) % m
if b % 2 == 1:
half = (half * a) % m
return half
# Example usage:
print(fast_power_recursive(3, 13, 7)) # Output: 3
Applications of Modular Exponentiation
- Cryptography: RSA encryption/decryption involves calculations like
(M^e mod n). - Discrete Mathematics: Computing modular powers for number theory problems.
- Competitive Programming: Handling large factorials, modular inverses, and Fibonacci sequences under modulo.
Interactive Python Example
You can quickly try modular exponentiation interactively in Python:
a = int(input("Enter base: "))
b = int(input("Enter exponent: "))
m = int(input("Enter modulus: "))
print("Result:", modular_exponentiation(a, b, m))
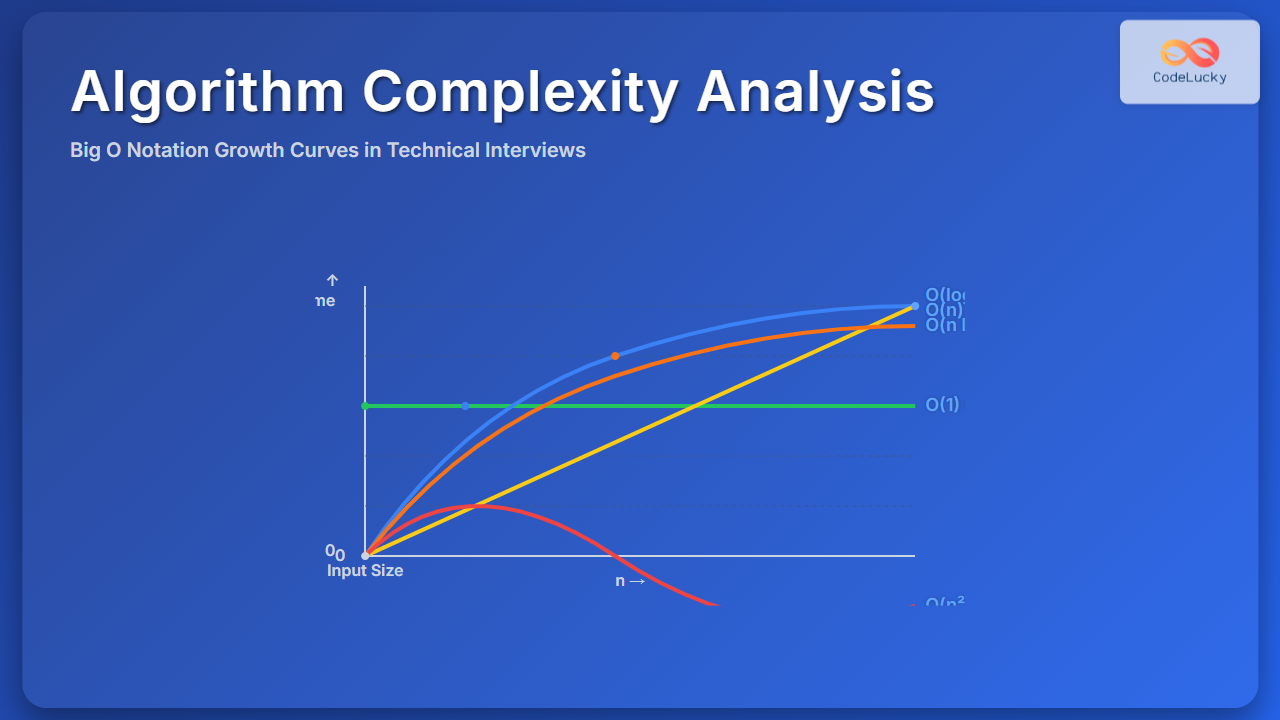
Time Complexity Analysis
- Naive Method:
O(b) - Fast Power Method:
O(log b)
This huge reduction in complexity makes modular exponentiation suitable for computations where b is extremely large.
Conclusion
The Modular Exponentiation: Fast Power Algorithm is one of the most fundamental algorithms in computer science. It enables efficient calculations, avoids overflow, and powers cryptographic systems. By understanding and implementing both iterative and recursive approaches, you’re prepared for not only competitive programming but also deeper applications in security and number theory.
- What is Modular Exponentiation?
- Why Do We Need Modular Exponentiation?
- Naive Approach: Why It Fails
- The Fast Power Algorithm (Binary Exponentiation)
- Python Implementation of Modular Exponentiation
- Step-by-Step Example
- Recursive Implementation
- Applications of Modular Exponentiation
- Interactive Python Example
- Time Complexity Analysis
- Conclusion