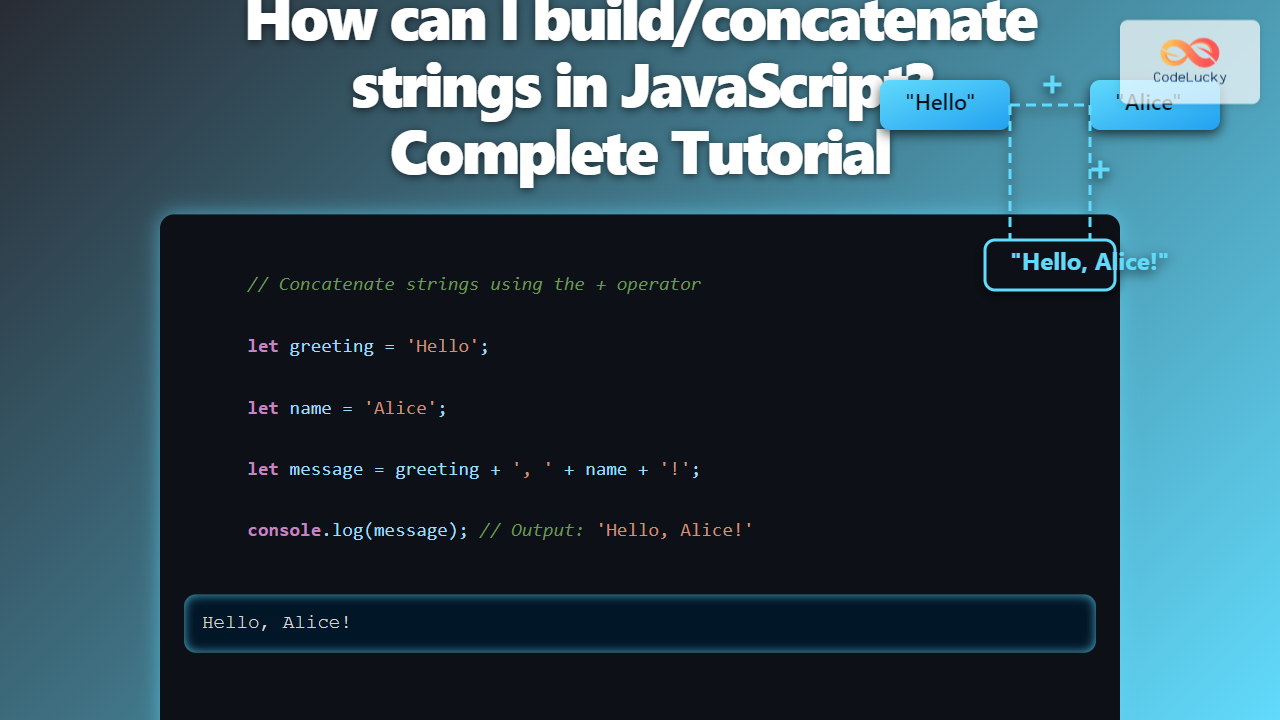
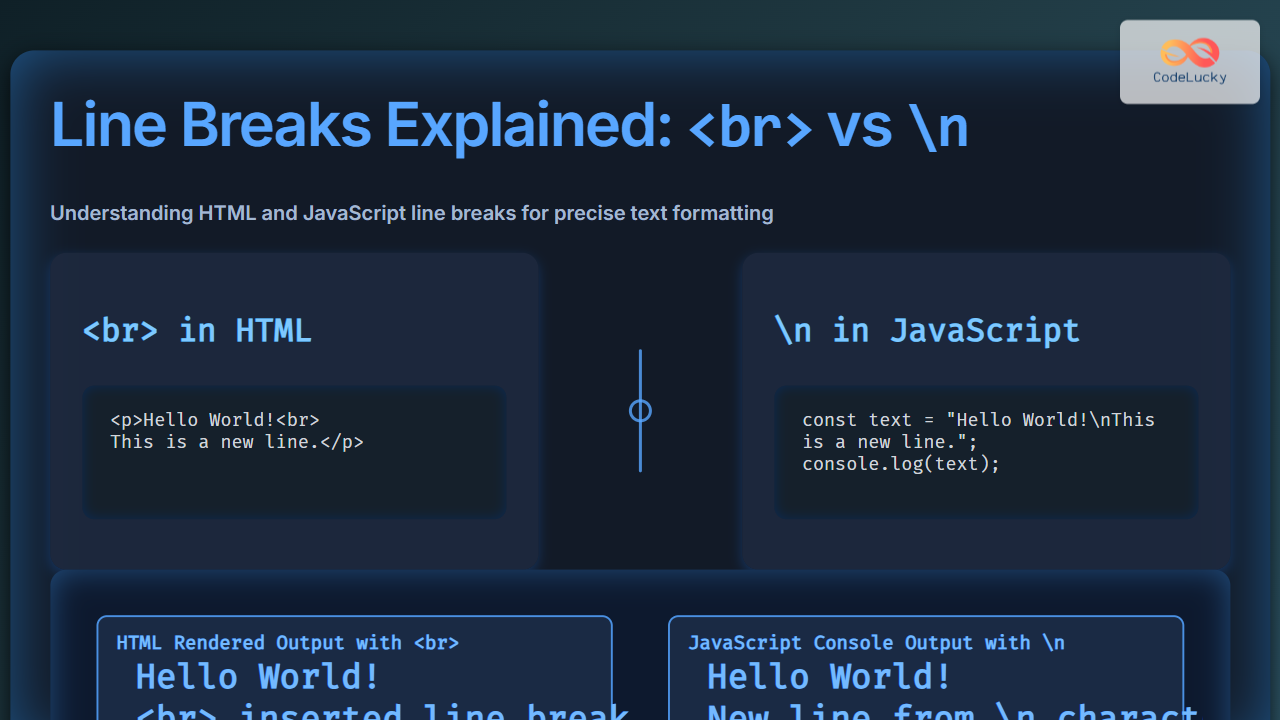
MD5 is one of the oldest and most widely-known hashing algorithms used in cybersecurity for data integrity verification and password storage. However, many developers and security enthusiasts ask: Is it possible to decrypt MD5 hashes? This article delves deeply into how MD5 hashing works, whether MD5 hashes are decryptable, and what implications this has for security. Additionally, we provide practical examples, visuals including mermaid diagrams, and interactive explanations where useful.
Understanding MD5 Hashing: What is MD5?
MD5 (Message Digest Algorithm 5) is a cryptographic hash function that produces a fixed-size 128-bit (16-byte) hash value from input data of any size. It is a one-way function designed to uniquely represent data in a compressed, irreversible format.
The key properties of a good hash function like MD5 are:
- Deterministic: The same input always produces the same output hash.
- Irreversibility: No feasible way to revert the hash back to the original input.
- Collision resistance: Hard to find different inputs that produce the same hash.
- Avalanche effect: Small change in input drastically changes the output hash.
Can MD5 Hashes Be Decrypted?
MD5 hashes are not decryptable in the traditional sense. Hashing is a one-way process — unlike encryption, hashing does not have a “key” that can be used to reverse the process back to the original data. Thus, MD5 hashes cannot be decrypted because the algorithm does not support a two-way transformation.
However, attackers can attempt to discover the original input by other means:
- Brute force attacks: Systematically hashing possible inputs to find a match.
- Dictionary and rainbow table attacks: Using precomputed tables of hash outputs for common inputs and reversing those hashes by lookup.
- Collision attacks: Exploiting known MD5 vulnerabilities to find different inputs that generate the same hash, though this rarely reveals the original input.
Example: Why MD5 is Considered Insecure for Password Hashing
To illustrate MD5’s vulnerabilities, consider its use in storing passwords. Suppose the password is password123. The MD5 hash is:
md5("password123") = 482c811da5d5b4bc6d497ffa98491e38An attacker with this hash can query online rainbow tables or use tools to quickly find the input:
$ echo -n "password123" | md5sum
482c811da5d5b4bc6d497ffa98491e38 -This reveals the straightforward vulnerability — the hash can be looked up and matched to the original password without actual decryption.
Interactive Explanation: Brute Force vs Rainbow Table
Imagine two paths to find the original value from an MD5 hash:
- Brute Force: Trying every possible combination until the hash matches.
- Rainbow Table: Using precomputed hash->input maps for common values.
Best Practices: Protecting Data Beyond MD5
Because MD5 is vulnerable, it is discouraged for security-critical functions like password storage. Instead, use modern hash algorithms designed for security:
- SHA-256 or SHA-3: More complex, collision-resistant hashes.
- Key stretching algorithms: bcrypt, scrypt, Argon2 — slow down hashing to thwart brute force.
- Salt: Adding unique data per input before hashing to avoid rainbow table attacks.
Summary of MD5 Decryption Possibility
| Aspect | MD5 Hash |
|---|---|
| Decryptable | No, MD5 hashes cannot be directly decrypted. |
| Vulnerabilities | Susceptible to brute force, rainbow tables, and collisions. |
| Use Case Suitability | Not suitable for secure password storage or cryptographic integrity. |
| Best Alternatives | SHA-256, bcrypt, Argon2 with salt. |
Conclusion
MD5 hashing is a one-way process and cannot be decrypted back to the original data. However, due to its vulnerabilities, attackers frequently recover input data through lookup tables or brute force attempts. For robust security, avoid MD5 in sensitive contexts and prefer modern, secure cryptographic hashing methods with salting and key stretching.