Understanding Intrusion Detection Systems
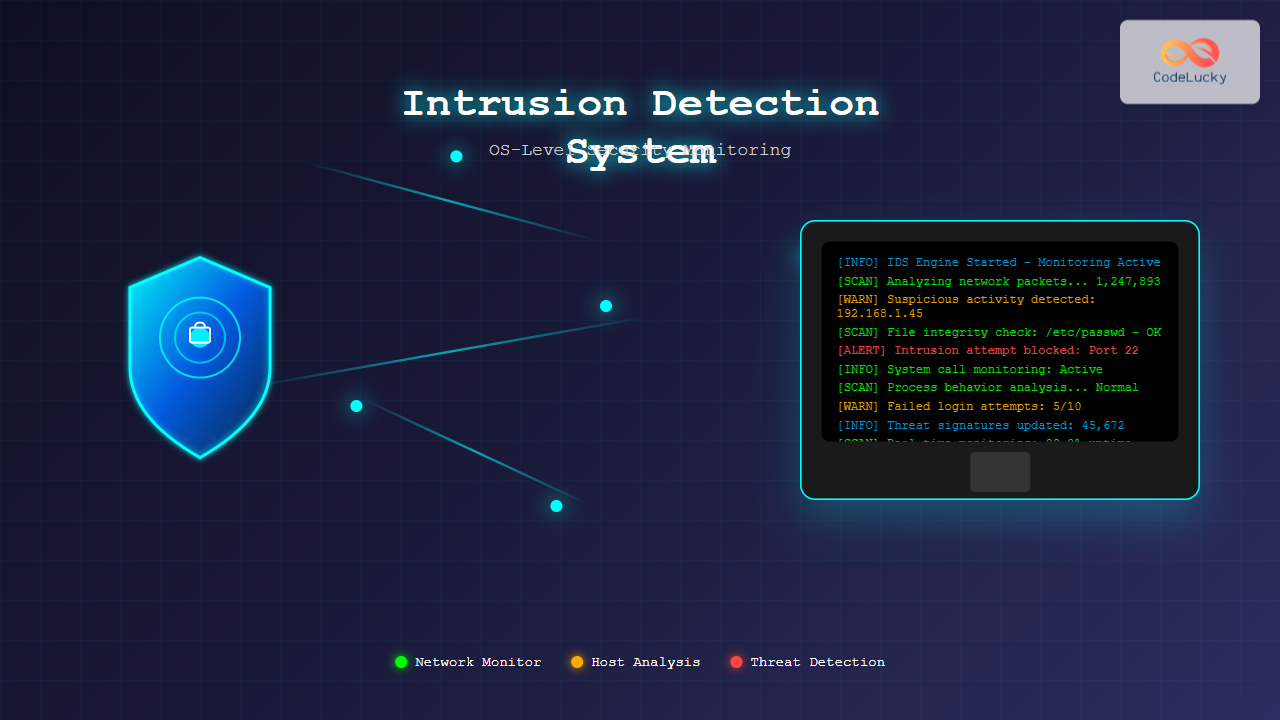
An Intrusion Detection System (IDS) is a critical security tool that monitors network traffic and system activities to detect malicious activities or policy violations. At the operating system level, IDS serves as a digital watchdog, continuously analyzing system logs, network packets, and user behaviors to identify potential security threats before they can cause significant damage.
Modern IDS implementations operate at multiple layers of the OSI model, with OS-level monitoring focusing primarily on system calls, file integrity, process behavior, and user activities. This comprehensive approach ensures that both external network-based attacks and internal system compromises are detected promptly.
Types of Intrusion Detection Systems
Network-based IDS (NIDS)
Network-based IDS monitors network traffic in real-time, analyzing packets as they traverse network segments. NIDS operates by placing sensors at strategic network points, typically near firewalls, routers, or network switches.
Key characteristics of NIDS include:
- Real-time packet analysis and inspection
- Protocol anomaly detection
- Signature-based threat identification
- Network traffic pattern analysis
- Integration with network infrastructure
Host-based IDS (HIDS)
Host-based IDS operates directly on individual systems, monitoring OS-level activities such as system calls, file modifications, registry changes, and user login patterns. HIDS provides granular visibility into system-specific activities that network-based solutions might miss.
HIDS monitoring capabilities include:
- File integrity monitoring (FIM)
- System call auditing
- Process behavior analysis
- User activity tracking
- Registry and configuration monitoring
Hybrid IDS Solutions
Modern enterprise environments often deploy hybrid IDS architectures that combine both network and host-based monitoring. This approach provides comprehensive coverage across all system layers, from network perimeter to individual host activities.
IDS Detection Methods
Signature-based Detection
Signature-based detection relies on predefined patterns or signatures of known malicious activities. This method compares observed system behavior against a database of attack signatures, providing high accuracy for known threats but limited effectiveness against zero-day attacks.
# Example signature rule for detecting SQL injection attempts
alert tcp any any -> any 80 (msg:"SQL Injection Attempt"; content:"union select"; nocase; sid:1001;)
# File integrity monitoring rule
monitor /etc/passwd /etc/shadow /etc/group
Anomaly-based Detection
Anomaly-based detection establishes baseline behavior patterns for normal system operations and identifies deviations that may indicate malicious activity. This approach excels at detecting unknown threats but may generate false positives due to legitimate system changes.
Behavioral Analysis
Behavioral analysis focuses on user and system behavior patterns, utilizing machine learning algorithms to identify suspicious activities based on context and historical data. This method is particularly effective for detecting insider threats and advanced persistent threats (APTs).
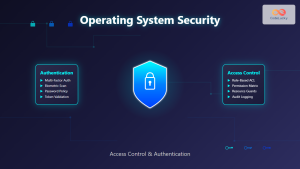
OS-Level Security Monitoring Components
System Call Monitoring
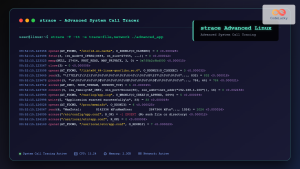
System call monitoring tracks all interactions between applications and the operating system kernel. This low-level monitoring provides detailed visibility into process activities, file operations, and network communications.
# Using strace to monitor system calls
strace -p 1234 -o /var/log/process_1234.trace
# Example system call trace output
open("/etc/passwd", O_RDONLY) = 3
read(3, "root:x:0:0:root:/root:/bin/bash\n", 4096) = 1024
close(3) = 0
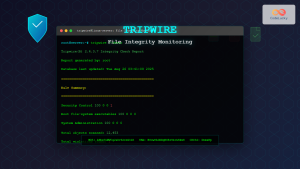
File Integrity Monitoring
File Integrity Monitoring (FIM) tracks changes to critical system files, configuration files, and executable binaries. FIM helps detect unauthorized modifications that could indicate system compromise or malware installation.
# AIDE configuration example
/bin PERMS+ACL+FTYPE+p+u+g+s+m+c+md5
/sbin PERMS+ACL+FTYPE+p+u+g+s+m+c+md5
/etc PERMS+ACL+FTYPE+p+u+g+s+m+c+md5+sha1
# Sample FIM alert output
CHANGED: /etc/passwd
Size: 1024 -> 1156
MD5: a1b2c3d4e5f6... -> f6e5d4c3b2a1...
Time: 2025-08-28 15:30:22
Log Analysis and Correlation
Comprehensive log analysis involves collecting, parsing, and correlating logs from multiple system components including authentication services, network services, and application logs.
Popular IDS Tools and Platforms
Open Source Solutions
Suricata is a high-performance network IDS engine that provides real-time intrusion detection, inline intrusion prevention, and network security monitoring capabilities.
# Suricata configuration snippet
vars:
address-groups:
HOME_NET: "[192.168.1.0/24]"
EXTERNAL_NET: "!$HOME_NET"
port-groups:
HTTP_PORTS: "80,8080,8000"
HTTPS_PORTS: "443,8443"
rule-files:
- emerging-threats.rules
- local.rules
outputs:
- eve-log:
enabled: yes
filetype: regular
filename: eve.json
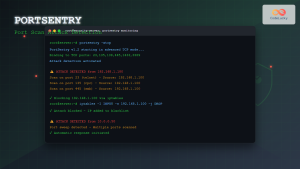
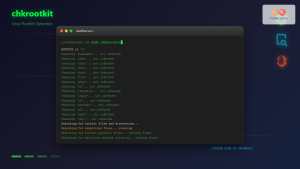
OSSEC is a comprehensive HIDS that provides log analysis, file integrity checking, policy monitoring, and active response capabilities.
/etc
/bin
/sbin
/etc/mtab
/etc/hosts.deny
no
yes
yes
yes
Commercial Solutions
Enterprise-grade IDS solutions like IBM QRadar, Splunk Enterprise Security, and McAfee Network Security Platform offer advanced correlation capabilities, centralized management, and comprehensive reporting features suitable for large-scale deployments.
Implementation Best Practices
Strategic Sensor Placement
Effective IDS implementation requires strategic placement of monitoring sensors to maximize coverage while minimizing performance impact. Critical placement points include:
- Network perimeter: Monitor traffic entering and leaving the organization
- Internal network segments: Detect lateral movement and internal threats
- Critical servers: Protect high-value assets with host-based monitoring
- DMZ zones: Monitor publicly accessible services
Tuning and Configuration
Proper tuning is essential for minimizing false positives while maintaining high detection rates. This involves:
- Baseline establishment during normal operations
- Rule customization based on environment specifics
- Threshold adjustment for anomaly detection
- Regular signature database updates
- Performance optimization for high-traffic environments
Integration with Security Infrastructure
Modern IDS deployments integrate seamlessly with existing security infrastructure including SIEM platforms, incident response systems, and automated remediation tools.
{
"alert": {
"signature": "ET MALWARE Suspicious Outbound Connection",
"severity": "high",
"source_ip": "192.168.1.100",
"destination_ip": "203.0.113.15",
"timestamp": "2025-08-28T15:45:32Z",
"protocol": "TCP",
"port": 443
},
"action": {
"block_ip": true,
"quarantine_host": true,
"notify_soc": true
}
}
Challenges and Limitations
Performance Considerations
IDS deployment can impact system and network performance, particularly in high-traffic environments. Performance optimization strategies include:
- Hardware acceleration for packet processing
- Selective monitoring based on risk assessment
- Load balancing across multiple sensors
- Efficient rule set management
- Resource allocation optimization
False Positive Management
False positive reduction requires ongoing attention and fine-tuning. Effective strategies include:
- Environment-specific rule customization
- Whitelist management for known-good activities
- Machine learning-based adaptive filtering
- Contextual analysis integration
- Regular review and adjustment cycles
Encrypted Traffic Challenges
The increasing prevalence of encrypted communications presents significant challenges for traditional IDS approaches. Modern solutions address this through:
- SSL/TLS decryption capabilities
- Metadata analysis of encrypted flows
- Certificate authority monitoring
- Behavioral analysis of encrypted connections
- Integration with DNS monitoring
Future Trends and Evolution
AI and Machine Learning Integration
Artificial intelligence and machine learning are revolutionizing IDS capabilities, enabling more accurate threat detection and reducing false positive rates through intelligent pattern recognition and behavioral analysis.
Cloud-Native IDS Solutions
As organizations migrate to cloud environments, cloud-native IDS solutions are emerging to address the unique challenges of monitoring containerized applications, serverless functions, and dynamic cloud infrastructures.
Zero Trust Architecture Integration
Zero Trust security models are driving the evolution of IDS toward identity-centric monitoring and micro-segmentation support, providing granular visibility and control across distributed environments.
Conclusion
Intrusion Detection Systems represent a fundamental component of modern cybersecurity defense strategies. By implementing comprehensive OS-level security monitoring, organizations can significantly enhance their ability to detect, analyze, and respond to security threats. Success requires careful planning, proper tool selection, ongoing tuning, and integration with broader security infrastructure.
As threats continue to evolve, IDS technologies must advance to address new challenges including encrypted communications, cloud environments, and sophisticated attack techniques. Organizations that invest in robust IDS implementations while maintaining focus on performance optimization and false positive management will be better positioned to defend against current and emerging security threats.