Hash functions are at the core of efficient data structures, especially hash tables, which enable constant-time lookups and insertions in practice. However, achieving this efficiency depends on how well the hash function is designed. In this article, we will explore the principles of hash function design, analyze what makes a good hash, provide step-by-step examples, and visualize key ideas using diagrams.
What is a Hash Function?
A hash function is a mathematical function that transforms input data (like strings, numbers, or objects) into a fixed-size integer, called the hash value or hash code. The goal is to map input keys to indices in a hash table efficiently.
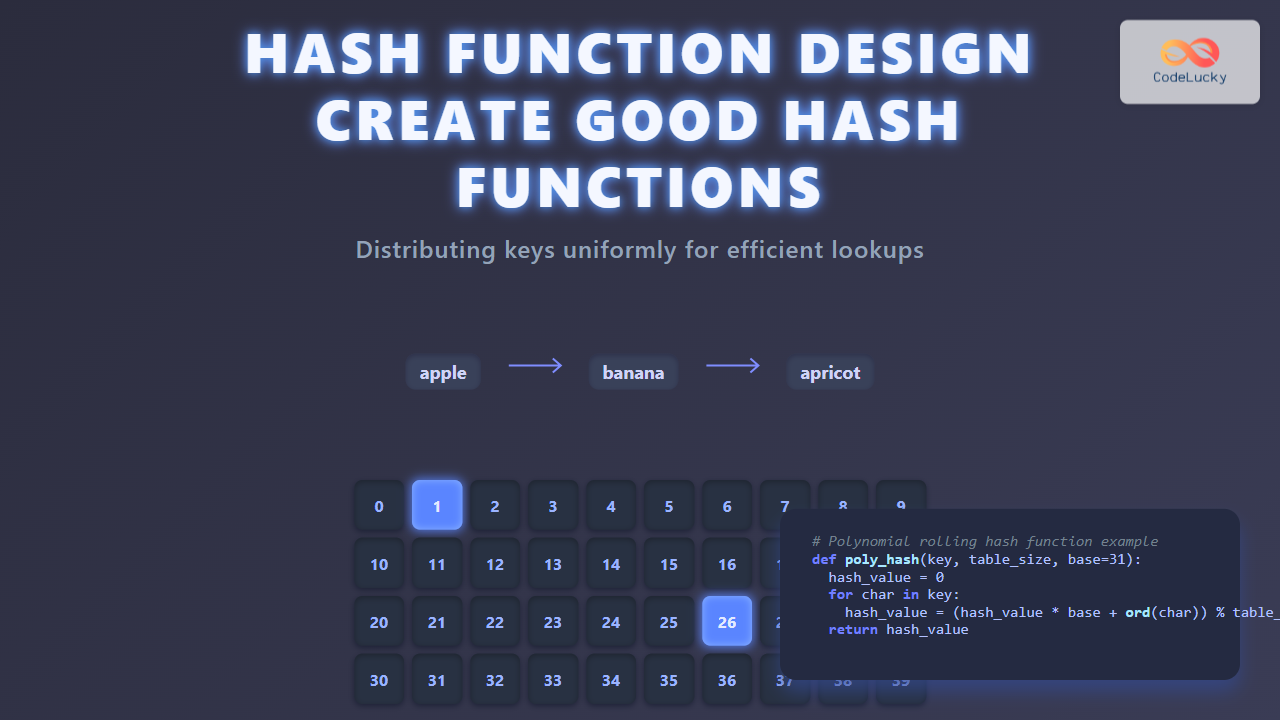
For example, hashing the string "apple" may produce the value 9342, which is then reduced modulo the table size to give an index (say 42) where the data is stored.
Qualities of a Good Hash Function
When designing hash functions, several qualities are essential:
- Uniform distribution: Keys should be spread evenly across the table to avoid clustering.
- Deterministic: The same input must always generate the same output.
- Efficiency: Compute hash values in constant or near-constant time.
- Low collision probability: Collisions (different keys mapping to the same index) should be minimized.
- Avalanche effect: Small changes in input should cause significant changes in the output hash.
Example: Simple Hash Function in Python
def simple_hash(key, table_size):
total = 0
for char in key:
total += ord(char) # Sum of Unicode code points
return total % table_size
# Example usage
keys = ["apple", "banana", "apricot", "blueberry"]
table_size = 10
for key in keys:
print(key, "->", simple_hash(key, table_size))
Output:
apple -> 0 banana -> 9 apricot -> 8 blueberry -> 2
This is a simple approach, but it has weaknesses. For example, "apple" and "papel" produce the same hash because they contain the same characters. This indicates potential collisions.
Visualizing Collisions
To avoid such problems, we need better designs.
Improving Hash Functions with Multipliers
Instead of simply summing character codes, we can combine multiplication to spread values more evenly:
def polynomial_rolling_hash(key, table_size, base=31):
hash_value = 0
for char in key:
hash_value = (hash_value * base + ord(char)) % table_size
return hash_value
# Example usage
for key in keys:
print(key, "->", polynomial_rolling_hash(key, table_size))
Sample Output:
apple -> 8 banana -> 1 apricot -> 6 blueberry -> 3
This drastically improves distribution and reduces collisions for common datasets.
Applying Hash Functions in Hash Tables
Once computed, the hash value is used with the modulo operator (%) to fit inside table size constraints. For example, hash value 9342 in a table of size 100 results in index 42.
Testing Distribution
We can test if a hash function distributes values uniformly by checking how many keys map to each bucket:
from collections import defaultdict
def test_distribution(keys, table_size, hash_func):
distribution = defaultdict(int)
for key in keys:
index = hash_func(key, table_size)
distribution[index] += 1
return distribution
keys = ["dog", "cat", "bird", "fish", "lion", "tiger", "bear", "shark", "zebra", "giraffe"]
table_size = 7
distribution = test_distribution(keys, table_size, polynomial_rolling_hash)
print("Distribution across buckets:", dict(distribution))
Expected Output:
Distribution across buckets: {1: 2, 3: 1, 4: 3, 5: 2, 6: 2}
Better hash functions distribute inputs more evenly, reducing the chance of overloaded buckets.
Best Practices for Designing Good Hash Functions
- Use prime numbers as table sizes to minimize patterns.
- Avoid simplistic approaches like adding character codes directly.
- Choose hash functions suited to input data type (strings, numbers, compound keys).
- Combine arithmetic operations (addition, multiplication, modulus) for better mixing.
- Always test distribution with expected key sets before production use.
Real-World Use Cases
Hash functions appear in many domains beyond hash tables:
- Cryptography: Secure hash functions like SHA-256 ensure data integrity.
- Databases: Indexing systems use hashing for fast lookups.
- Caching: Content-addressable storage relies heavily on hashing.
- Compilers: Symbol tables in programming languages use hash-based structures.
Conclusion
Designing good hash functions is a blend of mathematical intuition and practical testing. Poorly designed hashes cause collisions, reduced performance, and clustering in hash tables. By following best practices such as using polynomial rolling hash, choosing prime table sizes, and testing distribution, developers can build efficient, scalable, and collision-minimized hashing systems.