Operating system encryption serves as the cornerstone of modern data protection, safeguarding sensitive information from unauthorized access, data breaches, and cyber threats. As digital assets become increasingly valuable, understanding and implementing robust encryption mechanisms within operating systems has become essential for both individual users and enterprise environments.
Understanding Operating System Encryption
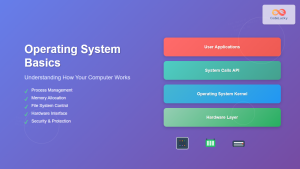
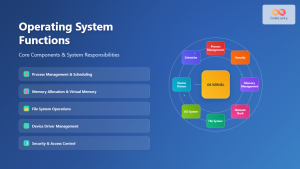
Encryption in operating systems involves the systematic conversion of readable data into an encoded format that can only be deciphered with the correct decryption key. This process occurs at multiple layers within the OS architecture, from file system level to memory protection, ensuring comprehensive data security across all system components.
Types of Encryption in Operating Systems
Symmetric Encryption
Symmetric encryption utilizes a single key for both encryption and decryption processes. This method offers high performance and is commonly implemented for bulk data encryption within operating systems.
Key Characteristics:
- Single shared key for encryption/decryption
- Fast processing speed
- Lower computational overhead
- Suitable for large data volumes
Common Algorithms:
- AES (Advanced Encryption Standard): 128, 192, or 256-bit keys
- DES (Data Encryption Standard): Legacy 56-bit encryption
- 3DES (Triple DES): Enhanced version using three DES operations
- ChaCha20: Modern stream cipher with high performance
Asymmetric Encryption
Asymmetric encryption employs a pair of mathematically related keys: a public key for encryption and a private key for decryption. This approach eliminates the need for shared secret keys but requires more computational resources.
Popular Algorithms:
- RSA: Widely used for key exchange and digital signatures
- ECC (Elliptic Curve Cryptography): Efficient alternative to RSA
- Diffie-Hellman: Key exchange protocol
Full Disk Encryption (FDE)
Full Disk Encryption represents the most comprehensive approach to data protection at the operating system level, encrypting entire storage devices including the operating system, applications, and user data.
Implementation Methods
Software-Based FDE:
- BitLocker (Windows): Integrated encryption solution using AES
- FileVault (macOS): XTS-AES 128 encryption with hardware acceleration
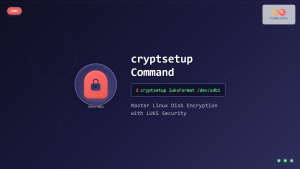
- LUKS (Linux): Flexible disk encryption specification
- dm-crypt (Linux): Kernel-level transparent disk encryption
Hardware-Based FDE:
- Self-Encrypting Drives (SEDs)
- Trusted Platform Module (TPM) integration
- Hardware Security Modules (HSMs)
File-Level Encryption
File-level encryption provides granular control over individual files and directories, allowing users to selectively protect sensitive data without encrypting the entire system.
Windows Encrypting File System (EFS)
EFS integrates seamlessly with NTFS file system, providing transparent encryption and decryption for authorized users.
Implementation Example:
cipher /e /s:C:\SecureFolder
cipher /u /n C:\SecureFolder\*.*
Linux File Encryption
eCryptfs Implementation:
# Mount encrypted directory
sudo mount -t ecryptfs /home/user/secure /home/user/secure
# Encrypt specific files using GPG
gpg --cipher-algo AES256 --compress-algo 1 --symmetric filename.txt
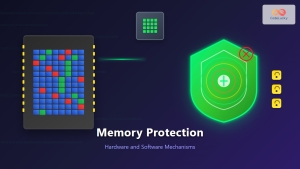
Memory Encryption
Memory encryption protects data while it resides in system RAM, preventing unauthorized access through physical memory dumps or cold boot attacks.
Technologies and Implementation
- Intel Total Memory Encryption (TME): Hardware-level RAM encryption
- AMD Secure Memory Encryption (SME): System memory protection
- ARM TrustZone: Secure and non-secure memory regions
Network and Communication Encryption
Operating systems implement various protocols to secure network communications and data transmission.
Transport Layer Security
- TLS/SSL: Secure web communications
- IPSec: Network layer security protocol
- VPN Integration: Virtual private network encryption
- SSH: Secure shell for remote access
Key Management Systems
Effective key management ensures the security and accessibility of encryption keys throughout their lifecycle.
Key Generation and Storage
- Hardware Random Number Generators: True entropy sources
- Key Derivation Functions (KDF): PBKDF2, Argon2, scrypt
- Secure Key Storage: Hardware security modules, TPM
- Key Escrow: Enterprise key recovery mechanisms
Key Rotation and Lifecycle
# Example key rotation implementation
import os
import hashlib
from cryptography.fernet import Fernet
class KeyManager:
def __init__(self):
self.current_key = None
self.previous_keys = []
def generate_new_key(self):
"""Generate new encryption key"""
new_key = Fernet.generate_key()
if self.current_key:
self.previous_keys.append(self.current_key)
self.current_key = new_key
return new_key
def rotate_keys(self, max_previous=5):
"""Rotate keys and maintain history"""
self.generate_new_key()
if len(self.previous_keys) > max_previous:
self.previous_keys = self.previous_keys[-max_previous:]
Performance Considerations
Encryption implementation must balance security requirements with system performance to maintain optimal user experience.
Hardware Acceleration
- AES-NI Instructions: Intel/AMD processor acceleration
- Cryptographic Coprocessors: Dedicated encryption hardware
- GPU Acceleration: Parallel processing for encryption tasks
- ARM Cryptography Extensions: Mobile device optimization
Performance Optimization Strategies
- Algorithm Selection: Choose appropriate encryption methods
- Block Size Optimization: Efficient data chunking
- Caching Mechanisms: Reduce key derivation overhead
- Parallel Processing: Multi-threaded encryption operations
Security Best Practices
Implementation Guidelines
- Use Strong Algorithms: AES-256, RSA-2048 minimum
- Implement Perfect Forward Secrecy: Session key independence
- Regular Security Audits: Vulnerability assessments
- Multi-Factor Authentication: Enhanced access control
- Secure Key Storage: Hardware security modules
Common Vulnerabilities and Mitigation
- Side-Channel Attacks: Timing analysis, power consumption
- Key Exposure: Memory dumps, swap files
- Implementation Flaws: Weak random number generation
- Social Engineering: User education and awareness
Future Developments
The encryption landscape continues evolving with emerging technologies and quantum computing threats.
Quantum-Resistant Cryptography
- Post-Quantum Algorithms: NIST standardization process
- Lattice-Based Cryptography: Quantum-resistant foundations
- Code-Based Systems: Alternative mathematical approaches
- Multivariate Cryptography: Polynomial equation systems
Emerging Technologies
- Homomorphic Encryption: Computation on encrypted data
- Confidential Computing: Secure execution environments
- Zero-Knowledge Proofs: Privacy-preserving verification
- Blockchain Integration: Decentralized key management
Conclusion
Operating system encryption forms the backbone of modern cybersecurity, protecting valuable data through multiple layers of defense. From full disk encryption to granular file-level protection, implementing comprehensive encryption strategies requires careful consideration of security requirements, performance implications, and user accessibility. As threats evolve and quantum computing approaches, organizations must stay informed about emerging encryption technologies and maintain robust security practices to ensure long-term data protection.
The successful implementation of encryption in operating systems demands a holistic approach, combining strong algorithms, proper key management, hardware acceleration, and regular security assessments. By following established best practices and staying current with technological developments, system administrators and developers can create resilient security architectures that protect against both current and future threats.