Introduction to Access Control Matrix
An Access Control Matrix (ACM) is a fundamental security model used in operating systems to define and manage permissions between subjects (users, processes) and objects (files, resources). This matrix-based approach provides a systematic way to control who can access what resources and what operations they can perform.
The Access Control Matrix serves as the cornerstone of permission management in modern operating systems, ensuring data security and preventing unauthorized access to system resources.
Understanding the Access Control Matrix Structure
The Access Control Matrix is organized as a two-dimensional table where:
- Rows represent subjects (users, processes, or principals)
- Columns represent objects (files, directories, devices, or resources)
- Cells contain access rights or permissions for each subject-object pair
Matrix Components Breakdown
| Component | Description | Examples |
|---|---|---|
| Subjects | Active entities that request access | Users (Alice, Bob), Processes (PID 1234), Applications |
| Objects | Passive entities being accessed | Files (document.txt), Directories (/home), Devices (printer) |
| Access Rights | Permissions granted to subjects | Read (r), Write (w), Execute (x), Delete (d), Create (c) |
Access Control Matrix Example
Let’s examine a practical example of an Access Control Matrix for a small office environment:
| payroll.txt | reports/ | printer1 | backup.sh | |
|---|---|---|---|---|
| Alice (Manager) | read, write | read, write, create | execute | |
| Bob (Employee) | – | read | – | |
| Carol (HR) | read, write, delete | read | – | |
| System Process | read | read, write, create, delete | manage | execute |
Analysis of the Matrix:
- Alice has managerial access to most resources except HR-specific files
- Bob has limited employee-level access to shared resources only
- Carol has specialized HR access to payroll data
- System Process maintains administrative control over all resources
Implementation Methods
Access Control Matrices can be implemented using different approaches, each with specific advantages and use cases:
1. Direct Matrix Implementation
The direct approach stores the complete matrix in memory, providing fast lookup times but requiring significant storage space for large systems.
# Example: Simple ACM implementation
class AccessControlMatrix:
def __init__(self):
self.matrix = {}
def grant_permission(self, subject, object, permission):
if subject not in self.matrix:
self.matrix[subject] = {}
if object not in self.matrix[subject]:
self.matrix[subject][object] = set()
self.matrix[subject][object].add(permission)
def check_permission(self, subject, object, permission):
return (subject in self.matrix and
object in self.matrix[subject] and
permission in self.matrix[subject][object])
2. Access Control Lists (ACLs)
ACLs store permissions by object, listing all subjects and their permissions for each resource.
3. Capability Lists
Capability lists store permissions by subject, maintaining a list of objects and permissions for each user or process.
{
"Alice": [
{"object": "payroll.txt", "permissions": ["read", "write"]},
{"object": "reports/", "permissions": ["read", "write", "create"]},
{"object": "printer1", "permissions": ["print"]}
],
"Bob": [
{"object": "reports/", "permissions": ["read"]},
{"object": "printer1", "permissions": ["print"]}
]
}
Advantages of Access Control Matrix
The Access Control Matrix model offers several key benefits for system security:
- Granular Control: Provides fine-grained permission management at the individual subject-object level
- Flexibility: Supports complex permission scenarios and dynamic access patterns
- Audit Trail: Enables comprehensive tracking of access permissions and changes
- Policy Enforcement: Ensures consistent application of security policies across the system
- Scalability: Can accommodate growing numbers of users and resources
Disadvantages and Limitations
Despite its advantages, the Access Control Matrix model has certain limitations:
- Storage Overhead: Large matrices require significant memory and storage resources
- Sparse Matrix Problem: Most cells are typically empty, leading to inefficient space utilization
- Administrative Complexity: Managing permissions becomes complex in large-scale environments
- Performance Impact: Permission checks can become slow with extensive matrices
- Maintenance Overhead: Requires constant updates as users and resources change
Real-World Applications
Access Control Matrices are widely implemented across various systems and platforms:
Operating Systems
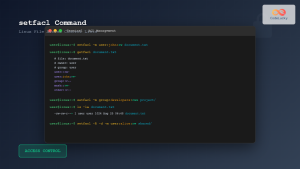
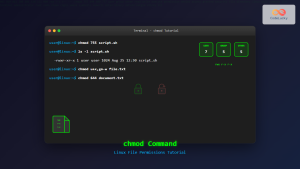
- UNIX/Linux: File permission systems using owner, group, and other categories
- Windows: NTFS permissions and Access Control Lists for files and registry keys
- macOS: Permissions framework for applications and system resources
Database Management Systems
- MySQL: User privileges on databases, tables, and columns
- PostgreSQL: Role-based access control for database objects
- Oracle: Comprehensive privilege management system
Cloud Platforms
- AWS IAM: Identity and Access Management policies
- Azure RBAC: Role-Based Access Control for resources
- Google Cloud IAM: Fine-grained access control for cloud services
Security Considerations
When implementing Access Control Matrices, several security aspects must be considered:
Principle of Least Privilege
Users and processes should be granted only the minimum permissions necessary to perform their required tasks. This reduces the potential impact of security breaches.
Regular Access Reviews
Periodic audits of the access control matrix help identify and remove unnecessary permissions, ensuring the system remains secure over time.
Dynamic Permission Updates
The matrix must support real-time updates to accommodate changing organizational needs and security requirements.
Modern Alternatives and Evolution
While Access Control Matrices remain foundational, modern systems often employ enhanced approaches:
Role-Based Access Control (RBAC)
RBAC simplifies matrix management by grouping permissions into roles and assigning users to roles rather than individual permissions.
Attribute-Based Access Control (ABAC)
ABAC uses attributes of subjects, objects, and environment to make dynamic access decisions, providing more flexible control.
Discretionary vs. Mandatory Access Control
- Discretionary (DAC): Object owners control access permissions
- Mandatory (MAC): System-enforced security policies determine access
Implementation Best Practices
To effectively implement Access Control Matrices in your systems:
- Start Small: Begin with essential subjects and objects, then expand gradually
- Use Templates: Create permission templates for common user types
- Automate Management: Implement tools for bulk permission updates and reviews
- Document Policies: Maintain clear documentation of access control policies
- Monitor Usage: Track permission usage to identify optimization opportunities
- Plan for Growth: Design the system to handle increasing scale efficiently
Conclusion
The Access Control Matrix remains a fundamental concept in operating system security and permission management. While direct implementation may face scalability challenges, understanding ACM principles is crucial for designing secure systems. Modern approaches like ACLs, capability lists, and role-based access control build upon the foundation provided by the Access Control Matrix model.
Whether you’re developing applications, managing system security, or designing access control policies, the concepts and principles of Access Control Matrices provide essential knowledge for creating robust, secure, and manageable permission systems. As technology continues to evolve, these foundational security concepts remain relevant and continue to influence modern security architectures.